2022HZWA(服务器部分)
通过对小型集群服务器分析,该服务器系统类型是?
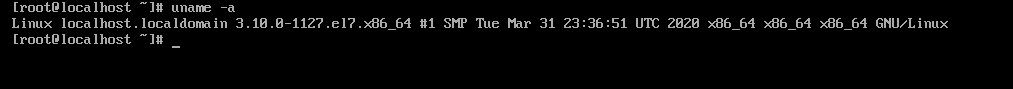
通过对小型集群服务器分析,该服务器系统时区是?
通过对小型集群服务器分析,该服务器的sshd端口是多少?(答案格式:填写数字 如:10)

小型集群服务器涉案网站的域名?(答案格式填写小写字母 . 数字组合 如:www.sina.com)
1 | [root@localhost nginx]# cat /www/backup/panel/2021-11-24/vhost/nginx/www.huarun.com.conf |
1 | server_name www.huarun.com |
涉案网站做了反向代理操作,使用的策略是什么?(答案格式:填写汉字 如:负载均衡)
1 | [root@localhost nginx]# cat /www/server/nginx/conf/nginx.conf |
1 | upstream huarun-server { |
这是按权重来的负载均衡
Docker中数据库容器的运行日志是在哪里,写出完整路径下的日志文件?(答案格式填写小写字母与数字等组合 如: /www/wwroot123/ab344/aa.log)
1 | [root@localhost nginx]# docker inspect 05 | grep log |
涉案网站管理后台登录密码的加密算法?
下面开始网站重构部分
先把docker都启起来
1 | [root@localhost /]# docker ps -a |
数据库docker没起来,看一下日志
1 | 2023-08-18 09:01:53+00:00 [Note] [Entrypoint]: Entrypoint script for MySQL Server 5.6.51-1debian9 started. |
看起来是my.cnf的问题,find一下逐一排查
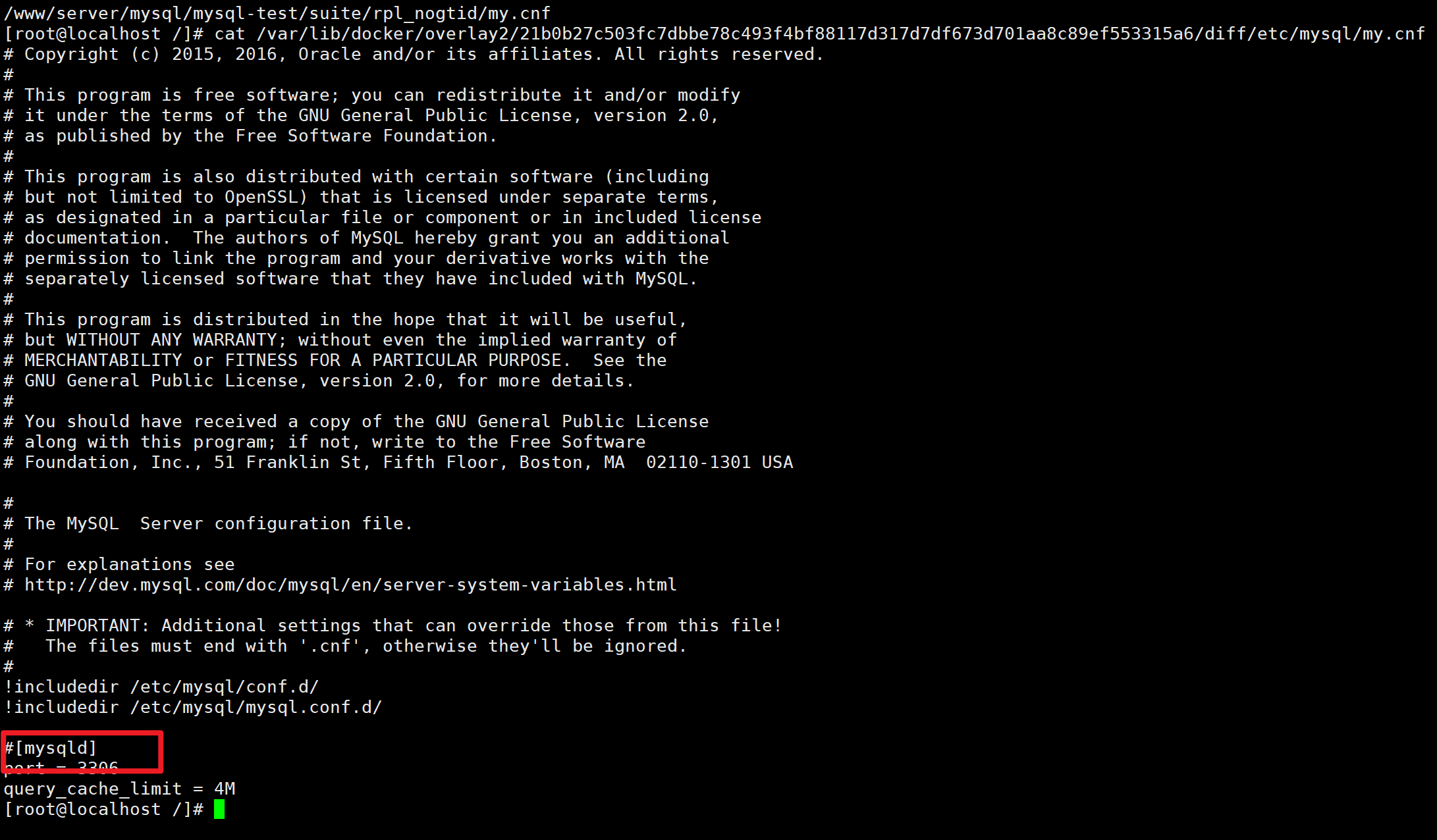
发现是这里被注释掉了,去掉注释符以后成功启动

试一下起nginx

查看配置文件
这是我vps上正常的配置文件
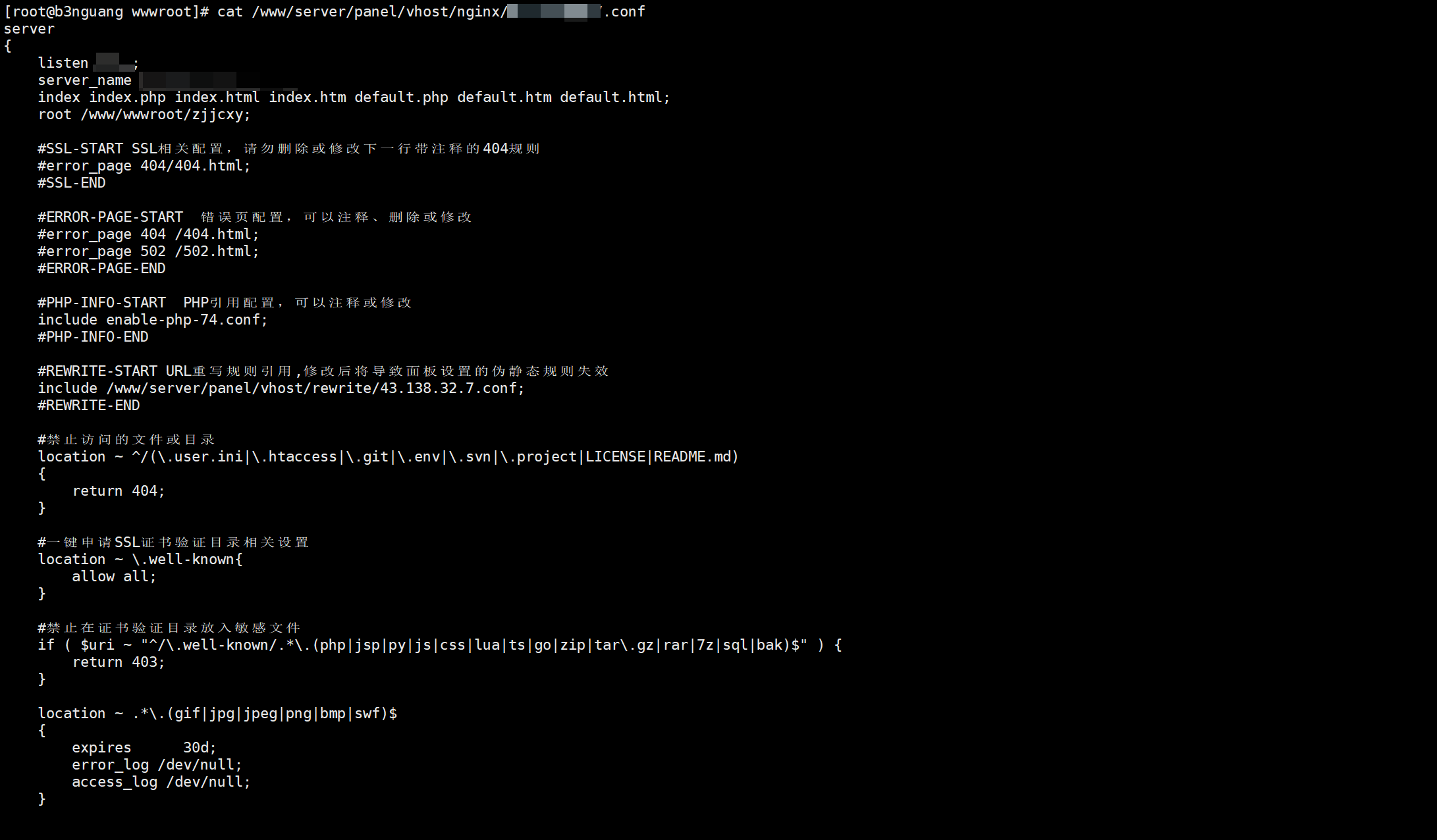
这是检材的配置文件

尝试补全
1 | #PROXY-START/ |
网站已经起来了,但是路由有点问题,访问192.168.110.131/index.php
进去容器
1 | root@a17719ef3c96:/var/www/html# cat /var/www/html/application/admin/controller/Login.php |
1 | if($result['upwd'] == md5(md5($data['password'].$result['utime']) |
两次md5加密
涉案网站的数据库是否开启general日志?(答案格式填写是或者否)
先看一眼数据库密码
1 | root@a17719ef3c96:/var/www/html/application# cat database.php |

得到容器ip地址


为了绕密,我选择拉一个宝塔对容器内文件进行操作,因为容器内没有vi等编辑指令


应该是随便一发就可以登录的,但是用户名错误

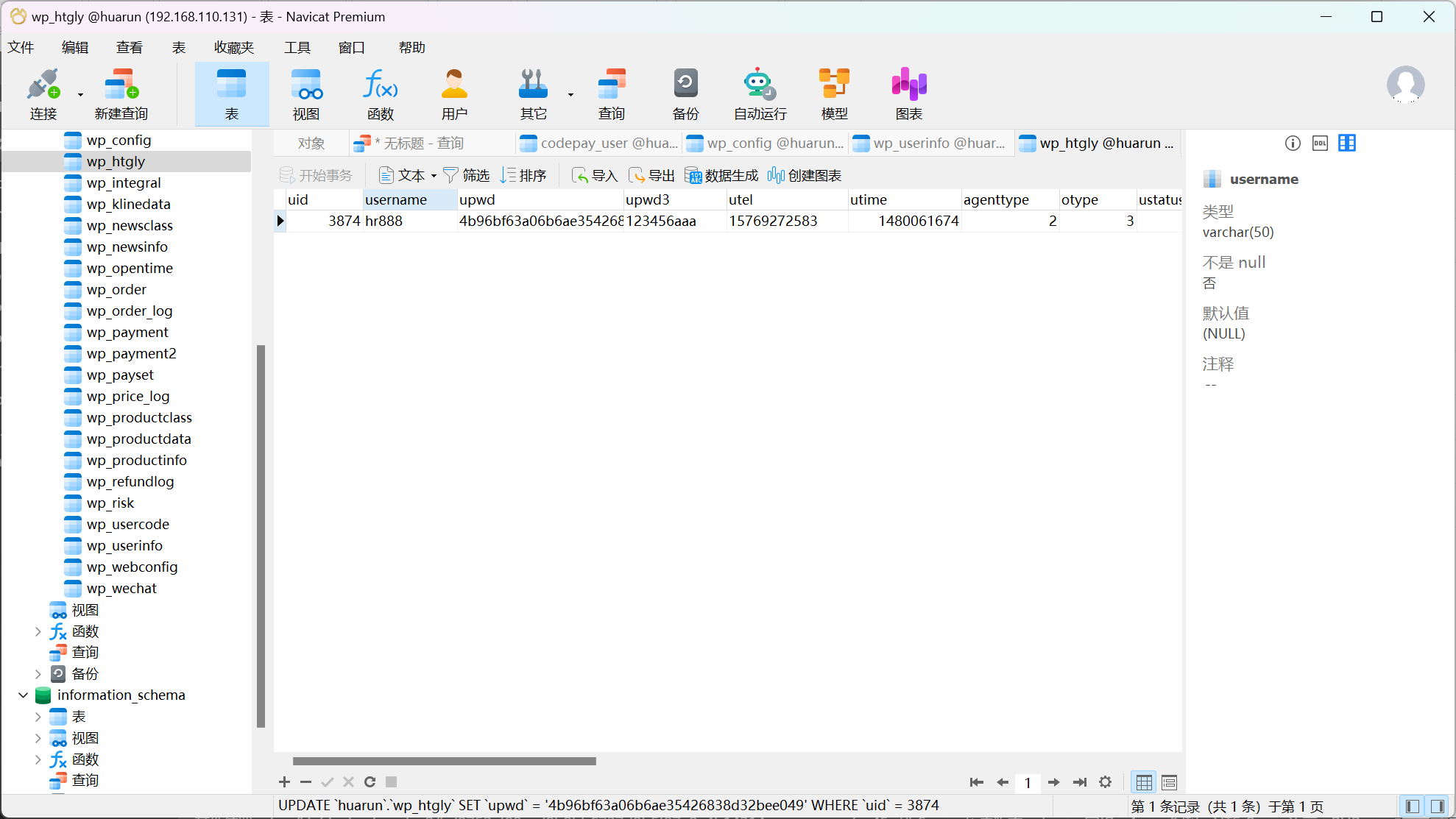
找到了用户名,登陆成功

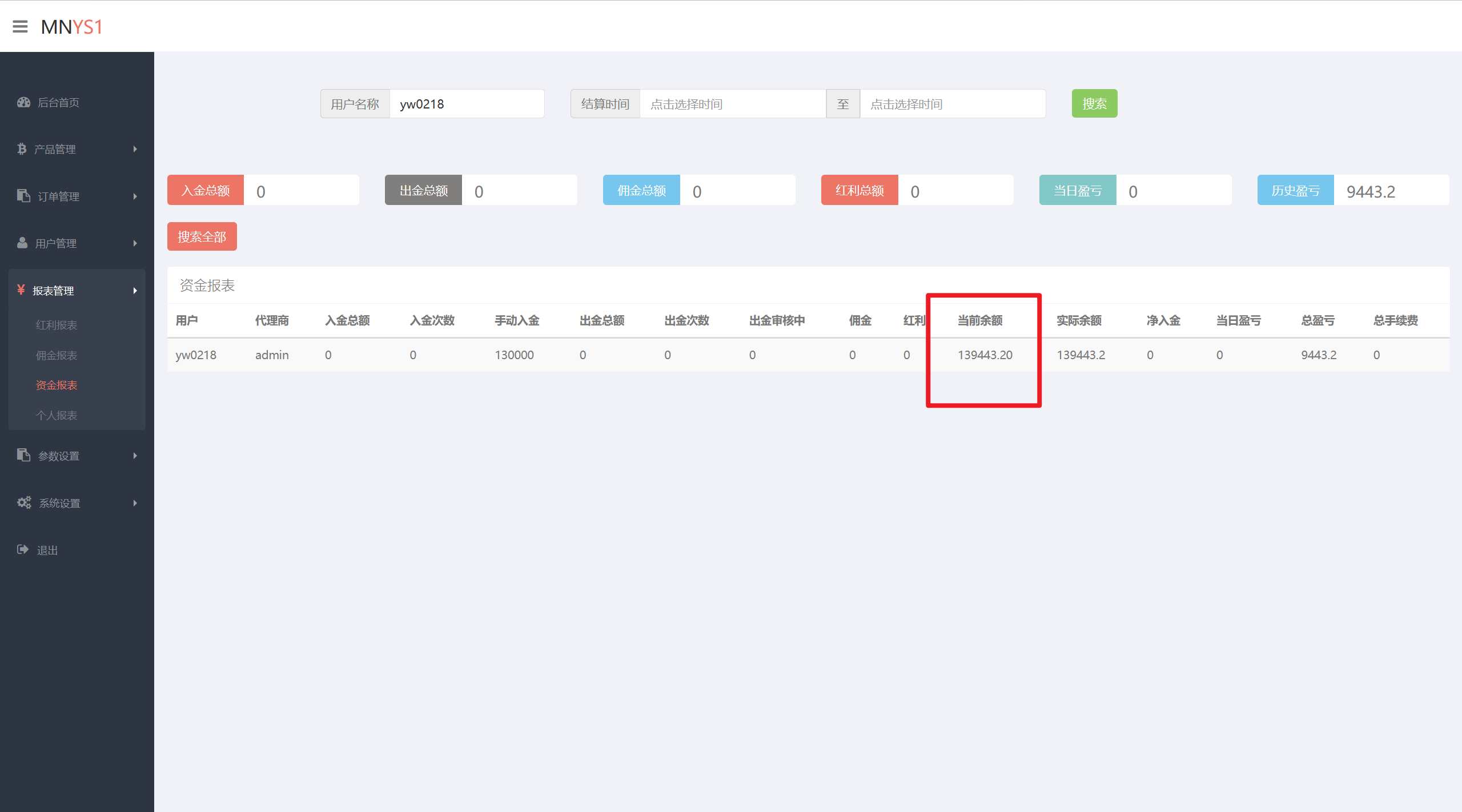
用户名”yw0218”的提现余额是多少元?(答案格式填写数字 保留小数点后二位 如:123.12)
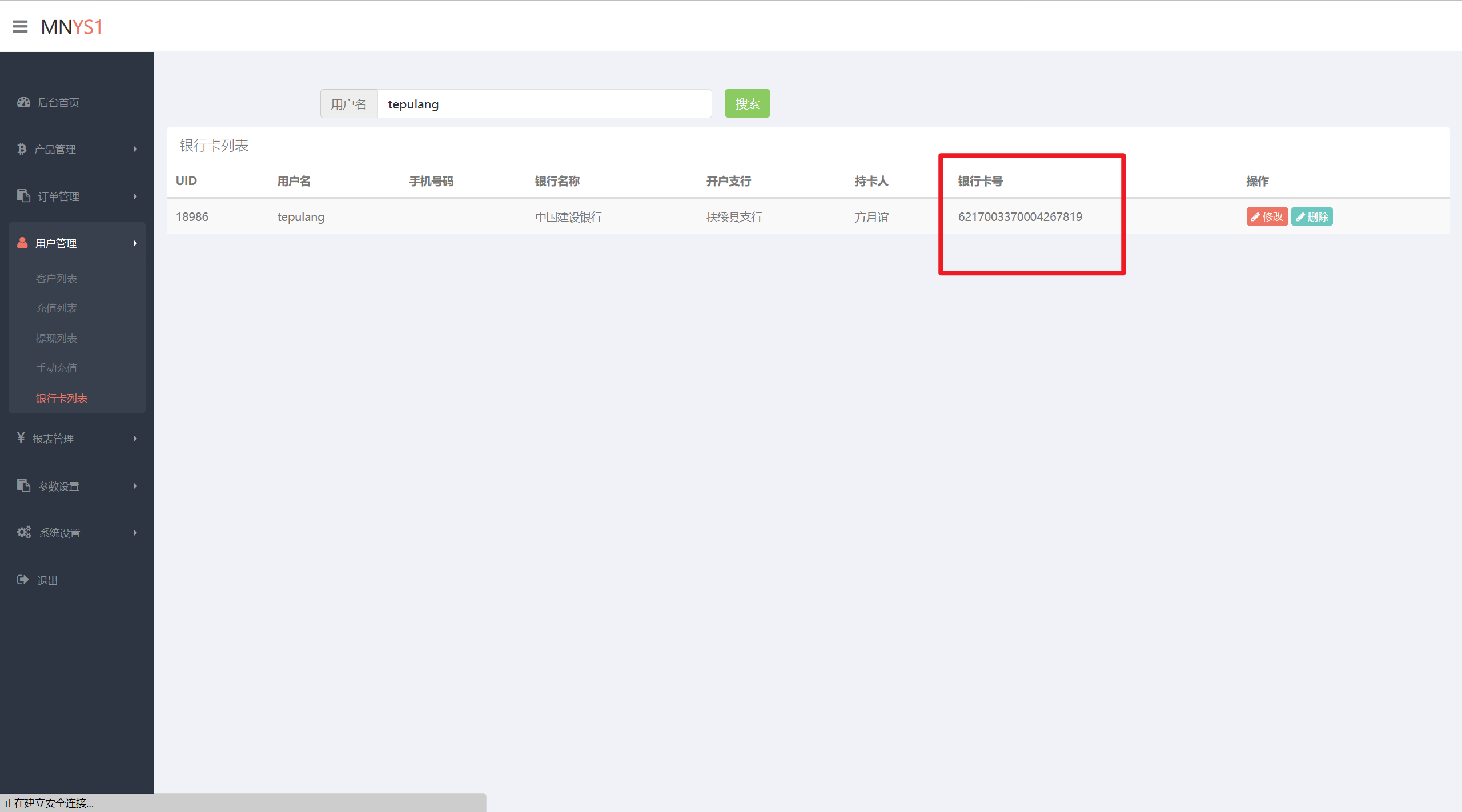
曾经的用户名为”fang25”的用户,其提现银行卡号是多少?(格式:填写数字:111111111111111111)
这里有个坑点,曾经用户名,那么我们就要查看mysql日志

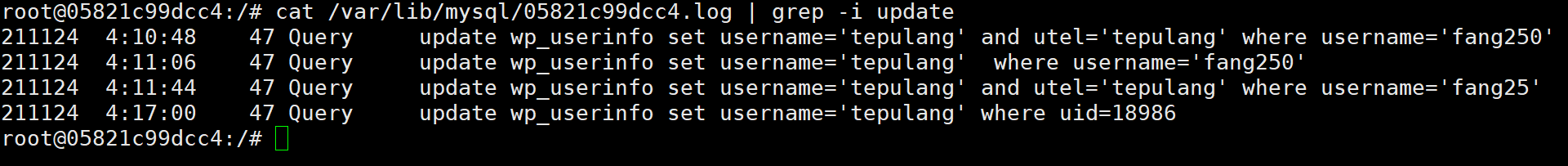
曾经的用户名为”fang25”的用户,其于2021-10-22日充值金额为多少元?(格式:填写数字取整 如:123)

曾经的用户名为”fang25”的用户,其于2021-10-22日进行利益一笔交易,其成交价格为多少元?(格式:填写数字 保留小数点后三位 如:123.123)

通过查看后台可以看出一共有多少产品?(答案格式填写数字 如:123)

一共有多少用户被禁用?(答案格式填写数字 如:123)
无脑方法是一页一页看
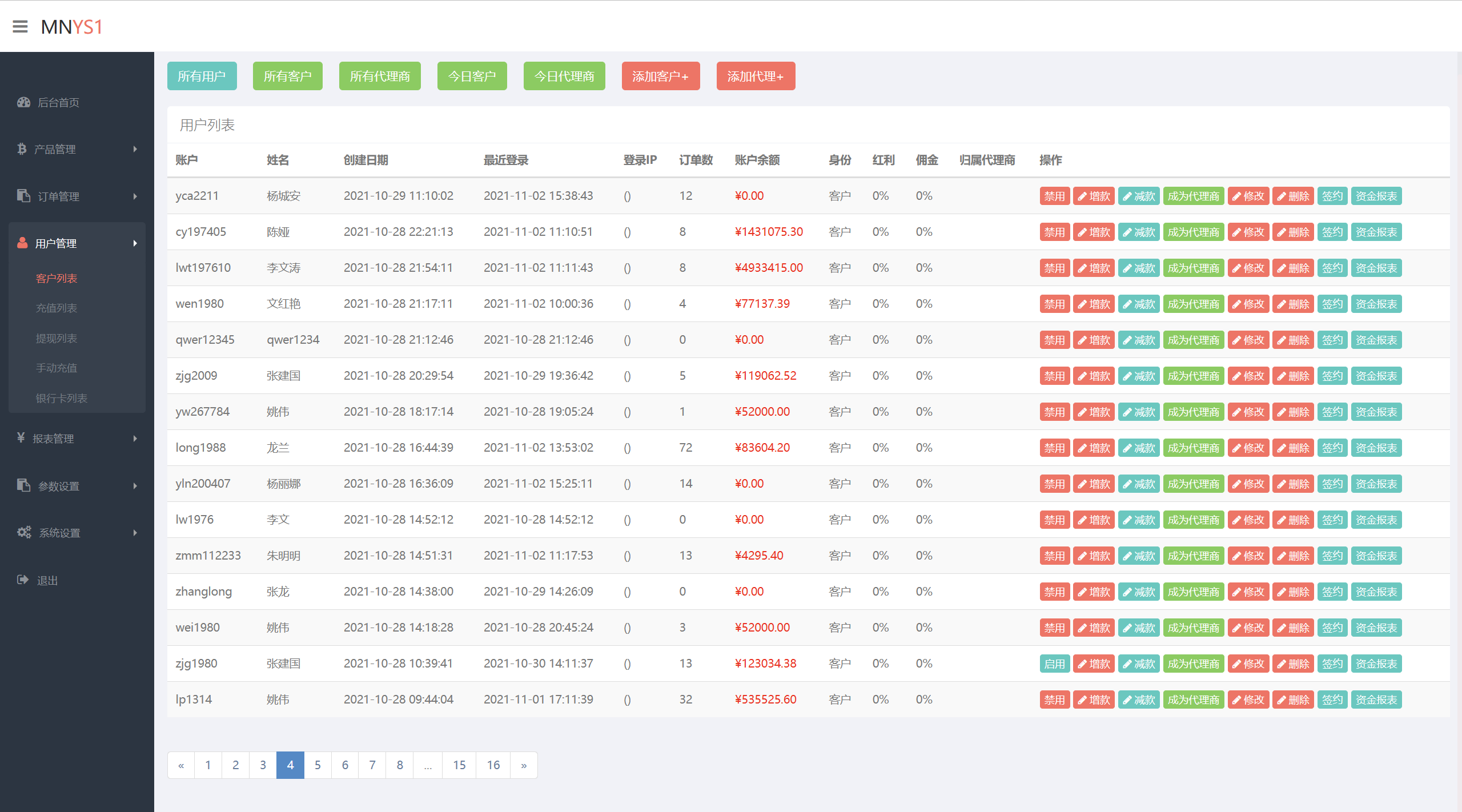
像这里,张建国就是禁用的,16页翻起来也很快
也可以在数据库里找
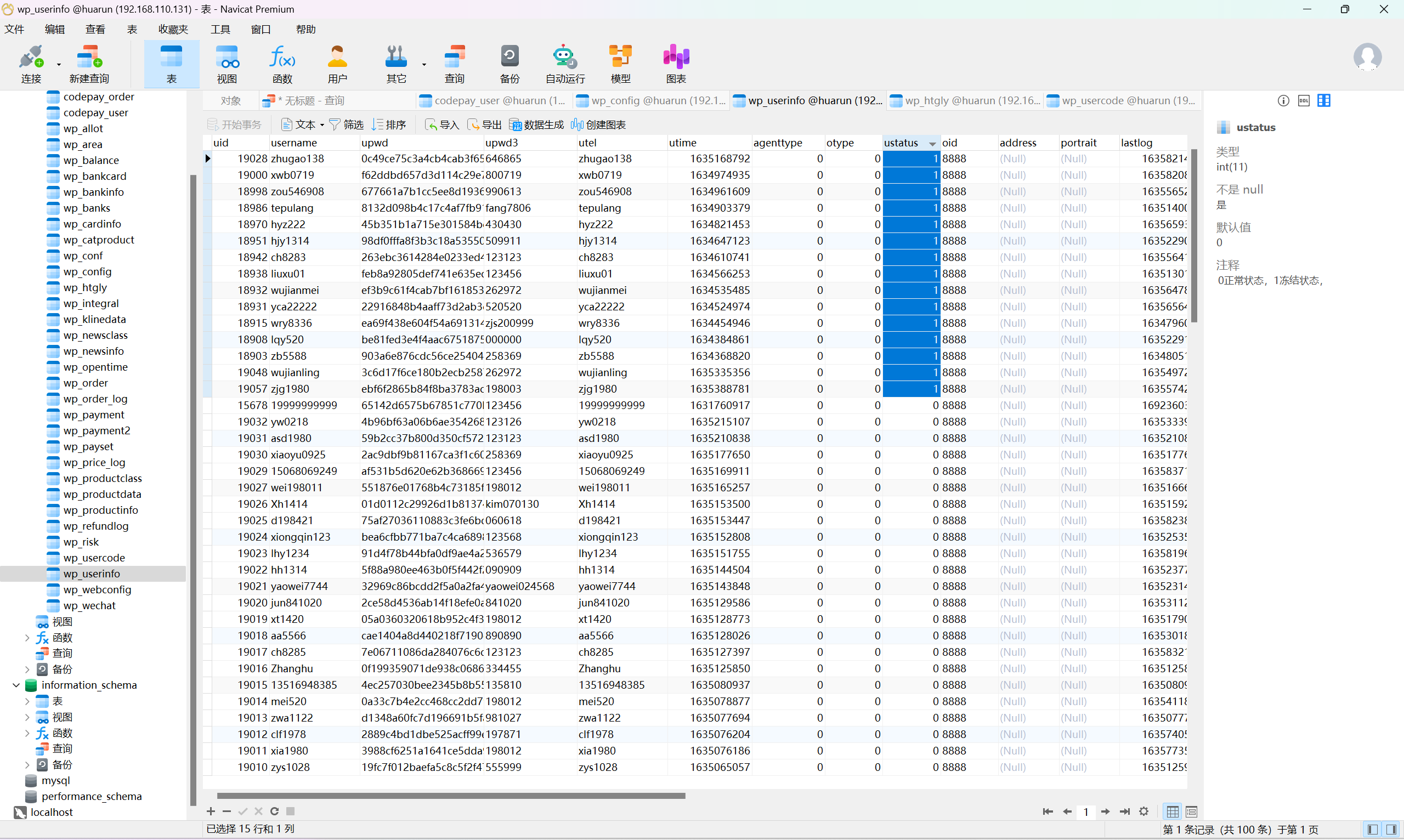
根据设置规则,单笔提现最大金额是多少?(格式:填写数字取整 如:123)

交易账号为”Ywei520”的用户再交易平台上委托金额是多少元?(格式:填写数字 保留小数点后一位 如:123.1)

本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 本光!
评论
