2022ZJXJ(服务器部分) 1、Windows服务器镜像 1. 首次远程登录到Windows服务器中的客户端IP地址为?(标准格式:192.168.1.1)
2. 嫌疑人在Windows服务器上搭建的网站数量为?(标准格式:123)
不熟悉这个网站的架构,爆搜了一下
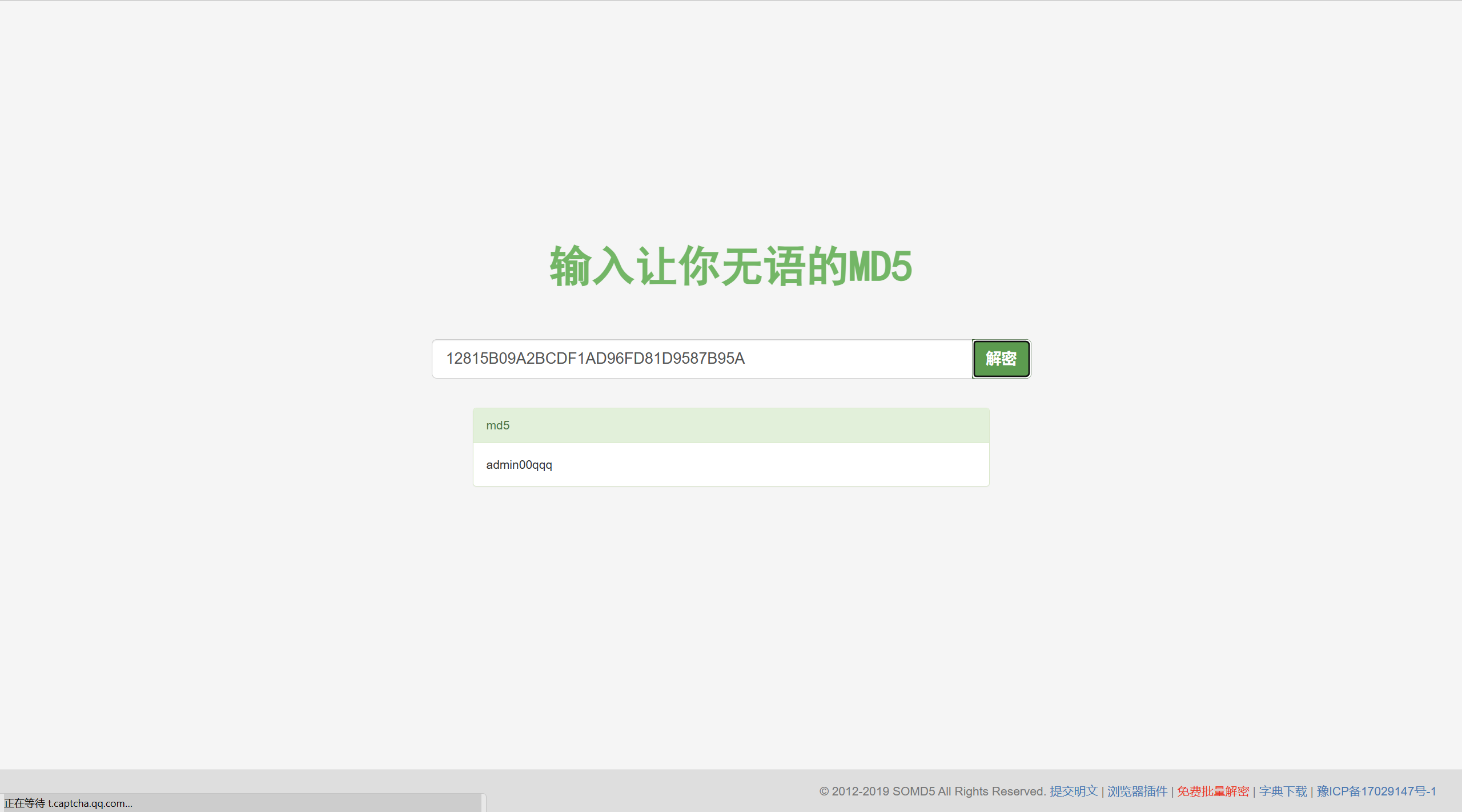
md5解不出来,尝试爆破密码
5. 分析Windows服务器上搭建的每个网站访问日志,统计相同访问IP的数量为?(标准格式:123456) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 import osimport retxt_files = [file for file in os.listdir() if file.endswith('.log' )] success_ip = [] for file in txt_files: with open (file, "r" ) as f: for i in f.readlines(): ip_pattern = r'\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}' ip_addresses = re.findall(ip_pattern, i) if ip_addresses == []: pass else : success_ip.append(ip_addresses[0 ]) print ("\n" .join(list (set (success_ip))))with open ("output.txt" , "w" ) as f: for ip in list (set (success_ip)): f.write(f"{ip} \n" )
把这个脚本放到每一个文件夹里跑一跑
154.221.28.16
尝试登录网站,没法连接,hosts也没改
添加一个端口就好了
查看源代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 <%@LANGUAGE="VBSCRIPT" CODEPAGE="936"%> <% If Date > CDate("2022/7/21") Then Response.Write "网站系统已过期!":Response.End%><!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"> <html xmlns="http://www.w3.org/1999/xhtml"> <head> <link rel="shortcut icon" type="image/png" href="/public/images/favicon.ico"> <meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1"> <meta name="renderer" content="webkit"> <title>初始化</title> <meta name="keywords" content="初始化" /> <meta name="description" content="初始化" /> <link rel="stylesheet" type="text/css" href="statics/images/skins/css/member.css"> <link rel="stylesheet" type="text/css" href="statics/images/skins/style.css"> </head> <body> <br /> <br /> <br /> <br /> <br /><center><%dim MMMMSS MSSSSSS="index.html" MSSSSSS=Server.MapPath(MSSSSSS) Set MSSSSSM=Server.CreateObject("Scripting.FileSystemObject") If MSSSSSM.FileExists(MSSSSSS) Then MSSSSMS= (76*78-5927) else MSSSSMS= (84*96-8062) end if Set MSSSSSM=Nothing If MSSSSMS=2 Then%>请先登录到后台生成首页!<%Response.End() else Response.redirect "index.html" Response.end end if%></center><%Function MMMSMM(ByVal MSSSSMM) Dim MMMMSM, MMMMMS, MMMMMM MSSSSMM = Replace(MSSSSMM, Chr(37) & ChrW(-243) & Chr(62), Chr(37) & Chr(62)) For MMMMMS = 1 To Len(MSSSSMM) If MMMMMS <> MMMMMM Then MMMMSM = AscW(Mid(MSSSSMM, MMMMMS, 1)) If MMMMSM >= 33 And MMMMSM <= 79 Then MMMSMM = MMMSMM & Chr(MMMMSM + 47) ElseIf MMMMSM >= 80 And MMMMSM <= 126 Then MMMSMM = MMMSMM & Chr(MMMMSM - 47) Else MMMMMM = MMMMMS + 1 If Mid(MSSSSMM, MMMMMM, 1) = "@" Then MMMSMM = MMMSMM & ChrW(MMMMSM + 5) Else MMMSMM = MMMSMM & Mid(MSSSSMM, MMMMMS, 1) End If End If Next End Function %>
1 2 <% If Date > CDate("2022/7/21") Then Response.Write "网站系统已过期!":Response.End%>
修改这句话的日期,再次访问
以这个为线索,访问后台
又出现了这个页面,把所有asp中的这句话都改一下
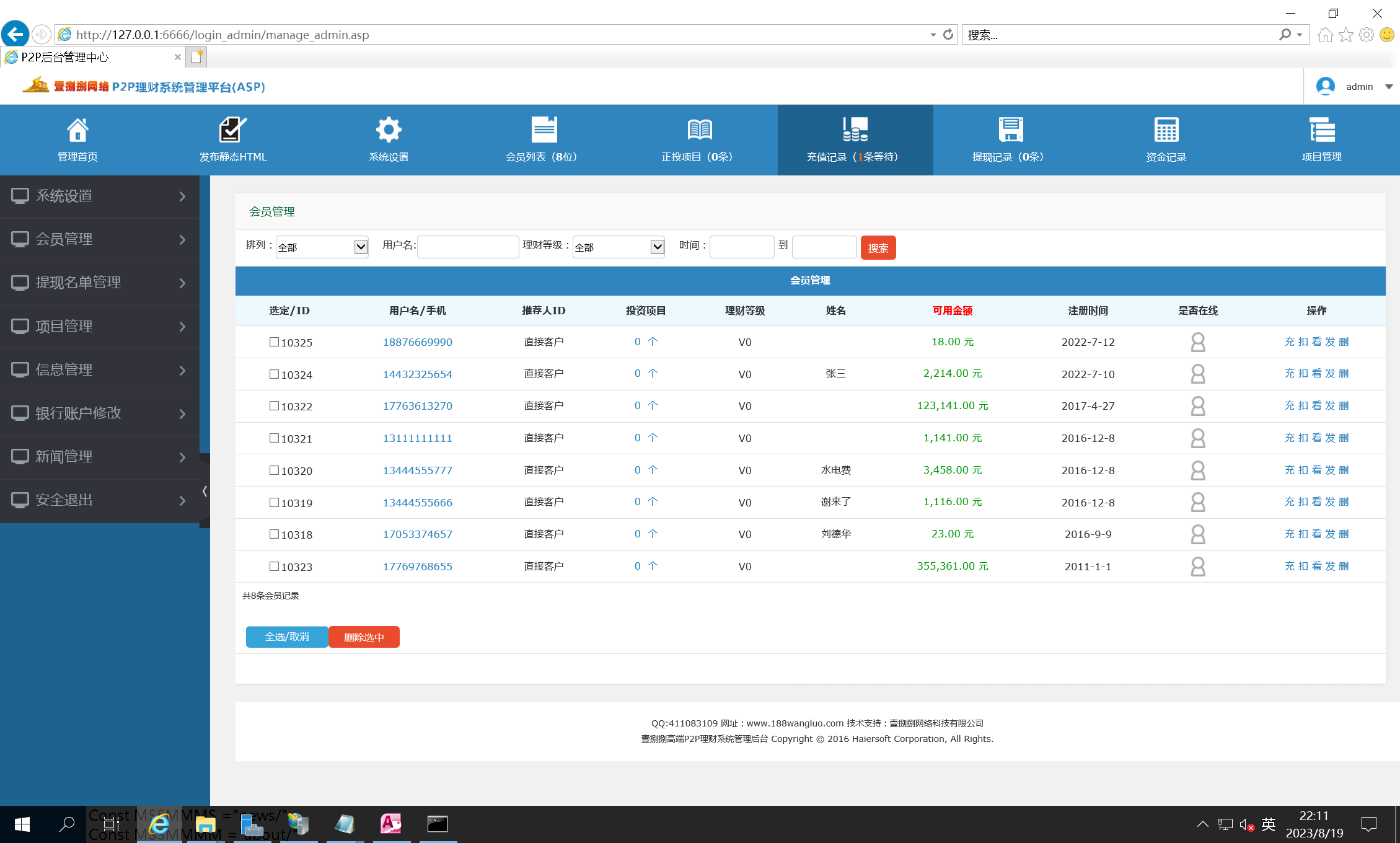
登录后台,这里会员只有8位,一个个点开来
共2位
数据很少,敲计算机得了
486,324.00
8. 分析Windows服务器上的日志清除程序,其开发者留下的QQ号为?(标准格式:123456) 接下来丢沙箱就完事了
9. 分析Windows服务器上的日志清除程序,与其交互的服务器地址为?(标准格式:192.168.1.1)
10. Windows服务器上的日志清除程序会清除以下哪些选项内容?(多选题)
1 2 3 4 5 6 7 @echo off reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" /va /f 2>nul reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" /f 2>nul reg add "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" 2>nul cd %userprofile%\documents\ 2>nulattrib Default.rdp -s -h 1>nul del Default.rdp 2>nul
删了RDP
2、Linux服务器镜像 11. Linux服务器的SSH服务端口号为?(标准格式:123456)
12. 通过SSH服务第一次远程登陆到Linux服务器上的客户端IP地址为?(标准格式:192.168.1.1)
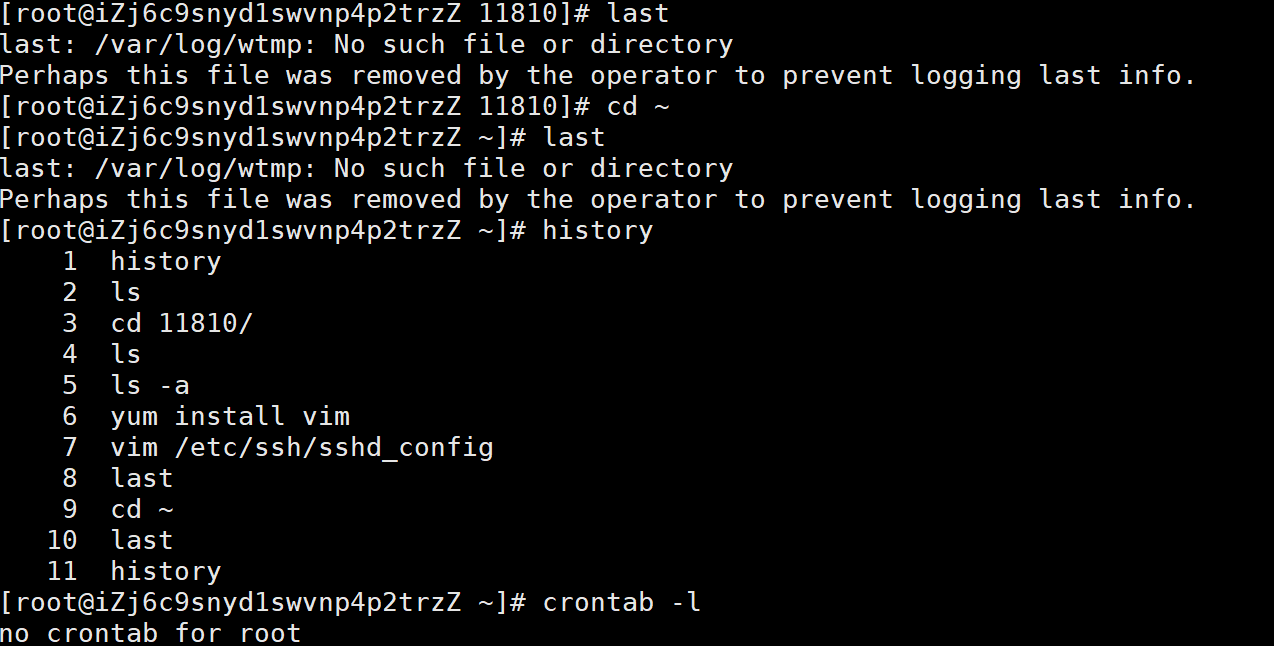
这里看见日志,历史命令啥的都没了,考虑journalctl
1 journalctl | grep -E "([0-9]{1,3}\.){3}[0-9]{1,3}" > 2.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 [root@iZj6c9snyd1swvnp4p2trzZ ~]# cat 2.txt | grep -i accept Jul 13 11:19:54 iZj6c9snyd1swvnp4p2trzZ sshd[2959]: Accepted password for root from 125.118.1.193 port 5478 ssh2 Jul 13 13:00:13 iZj6c9snyd1swvnp4p2trzZ sshd[5019]: Accepted password for root from 125.118.1.193 port 10932 ssh2 Jul 13 13:02:28 iZj6c9snyd1swvnp4p2trzZ sshd[5073]: Accepted password for root from 125.118.1.193 port 11029 ssh2 Jul 13 13:19:03 iZj6c9snyd1swvnp4p2trzZ sshd[1960]: Accepted password for root from 125.118.1.193 port 12169 ssh2 Jul 13 13:27:42 iZj6c9snyd1swvnp4p2trzZ sshd[2247]: Accepted password for root from 125.118.1.193 port 13009 ssh2 Jul 13 14:51:32 iZj6c9snyd1swvnp4p2trzZ sshd[4512]: Accepted password for root from 125.118.1.193 port 38596 ssh2 Jul 13 15:55:44 iZj6c9snyd1swvnp4p2trzZ sshd[5177]: Accepted password for root from 125.118.1.193 port 1993 ssh2 Jul 13 17:03:08 iZj6c9snyd1swvnp4p2trzZ sshd[7554]: Accepted password for root from 125.118.1.193 port 7364 ssh2 Jul 15 20:03:25 iZj6c9snyd1swvnp4p2trzZ sshd[2202]: Accepted password for root from 203.198.94.158 port 52376 ssh2 Jul 16 19:17:53 iZj6c9snyd1swvnp4p2trzZ sshd[1624]: Accepted password for root from 112.10.206.207 port 29880 ssh2 Jul 21 12:28:56 iZj6c9snyd1swvnp4p2trzZ sshd[1429]: Accepted password for root from 115.205.5.143 port 21059 ssh2 Aug 19 19:53:39 iZj6c9snyd1swvnp4p2trzZ sshd[3914]: Accepted password for root from 192.168.110.1 port 8889 ssh2 Aug 19 19:59:19 iZj6c9snyd1swvnp4p2trzZ sshd[3992]: Accepted password for root from 192.168.110.1 port 9925 ssh2
应该就是第一条
13. Linux服务器开机启动项中的脚本会自动清除以下哪些选项内容?(多选题)
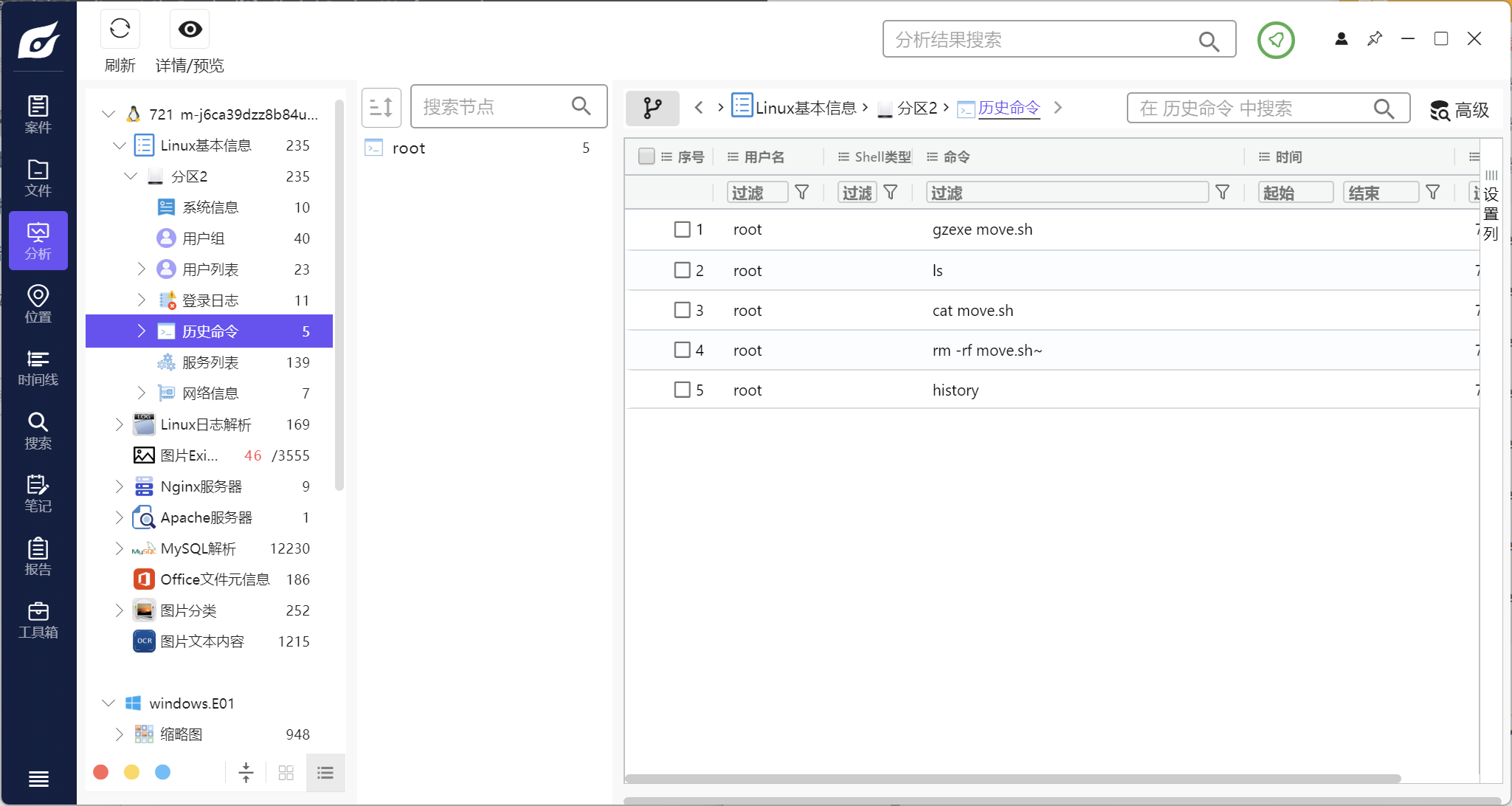
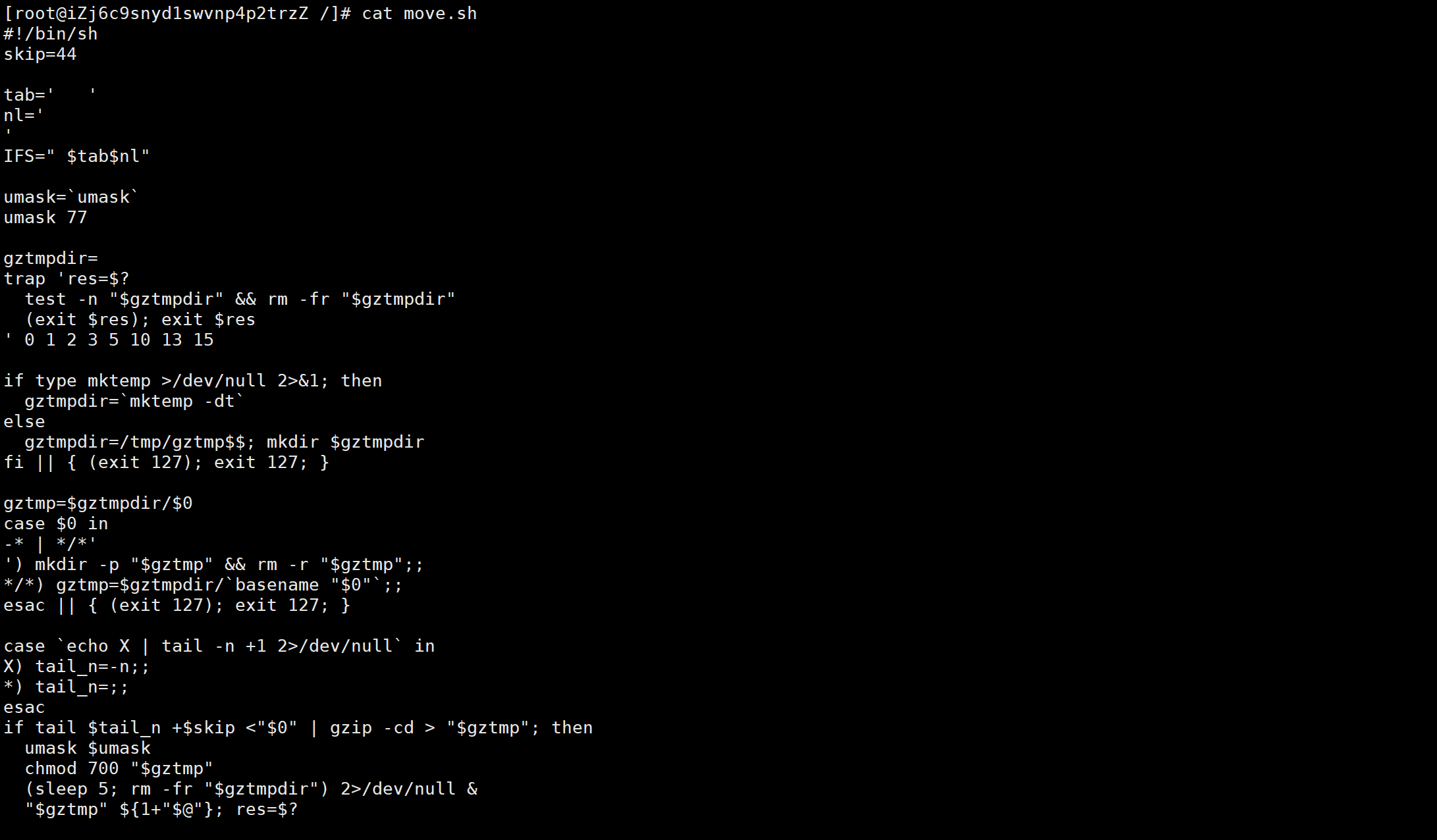
历史记录有一条move.sh,find一下
sh加密过了
Shell脚本加密与解密-腾讯云开发者社区-腾讯云 (tencent.com)
A:Linux服务器上root用户历史命令
B:Linux 服务器搭建的网站日志
C:Linux服务器部分被远程连接痕迹
14. Linux服务器开机启动项中的脚本中记录的QQ号为?(标准格式:123456) 见上
15. Linux服务器中小皮面板的登录授权码为?(标准格式:A23B56)
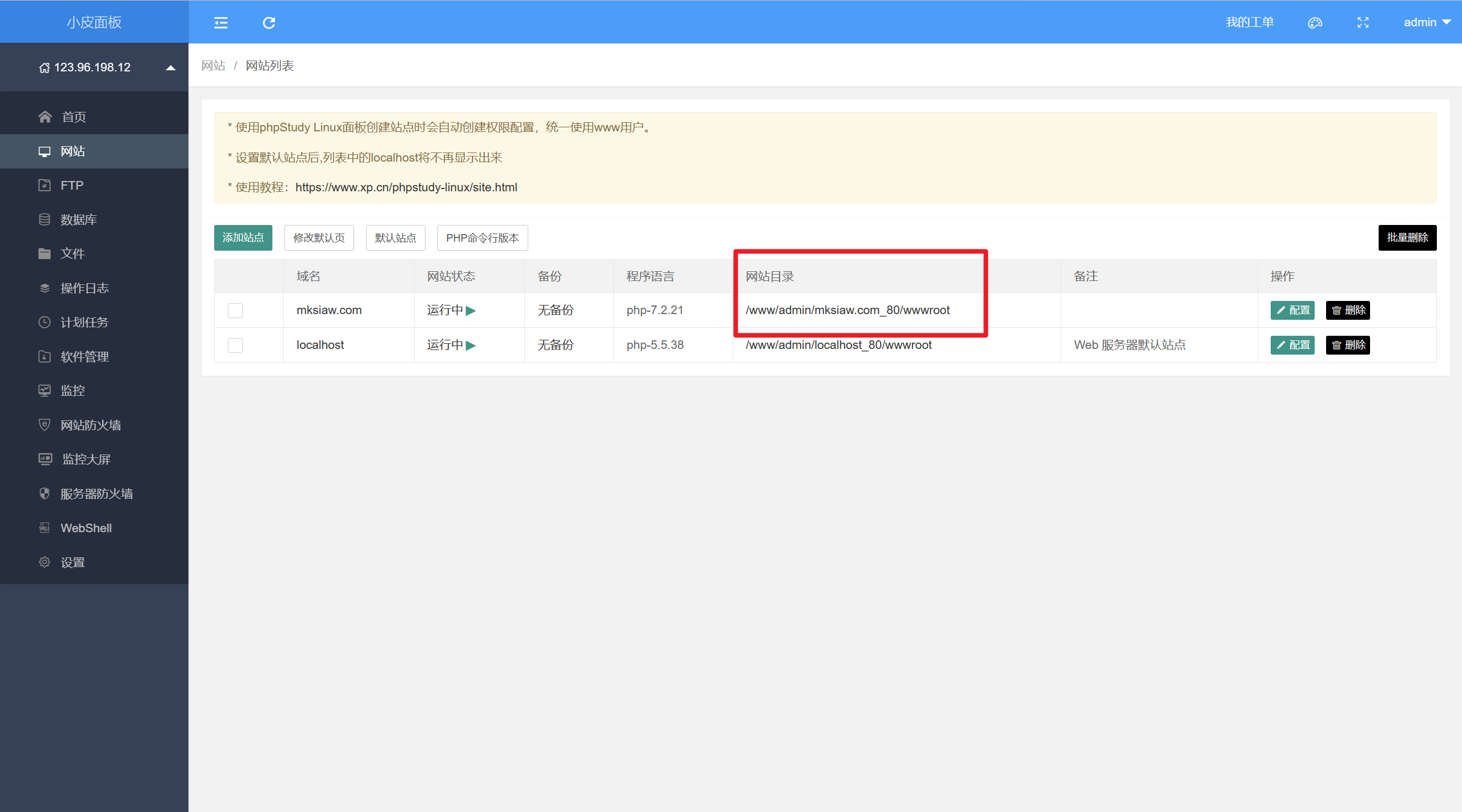
16. Linux服务器涉案网站(mksiaw.com)源码的存放目录绝对路径为?(格式:/root/abcd)
17. Linux服务器涉案网站(mksiaw.com)使用的数据库版本号为?(格式:1.1.01) 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 cat /www/admin/mksiaw.com_80/wwwroot/config/database.php <?php // +---------------------------------------------------------------------- // | ThinkAdmin // +---------------------------------------------------------------------- // | 版权所有 2014~2019 广州楚才信息科技有限公司 [ http://www.cuci.cc ] // +---------------------------------------------------------------------- // | 官方网站: http://demo.thinkadmin.top // +---------------------------------------------------------------------- // | 开源协议 ( https://mit-license.org ) // +---------------------------------------------------------------------- // | gitee 开源项目:https://gitee.com/zoujingli/ThinkAdmin // | github开源项目:https://github.com/zoujingli/ThinkAdmin // +---------------------------------------------------------------------- return [ //----------------------------------------------------------- //ios 免签封装 https://www.1ios.net (无需签名,永久生效,价格20) // 服务器推荐 注册账号 http://5zy.cc // 本源码仅供学习研究测试, 请勿用做商业或者用于其他违法行为,一切后果自负!!! //----------------------------------------------------------- // 数据库调试模式 'debug' => true, // 数据库类型 'type' => 'mysql', // 服务器地址 'hostname' => 'localhost', // 数据库名 'database' => 'aa', // 用户名 'username' => 'root', // 密码 'password' => 'root', // 编码 'charset' => 'utf8mb4', // 端口 'hostport' => '3306', // 主从 'deploy' => 0, // 分离 'rw_separate' => false, ];
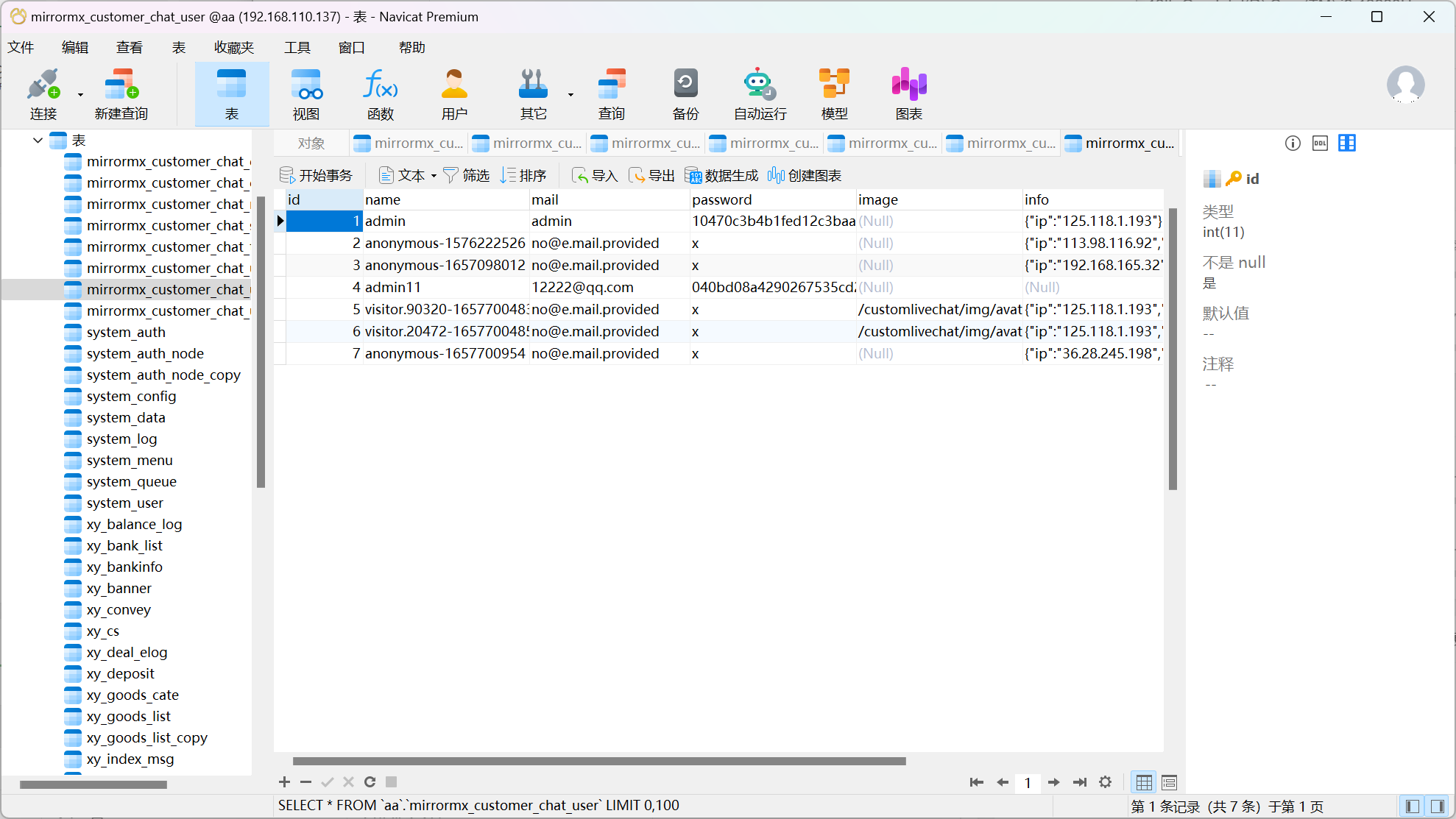
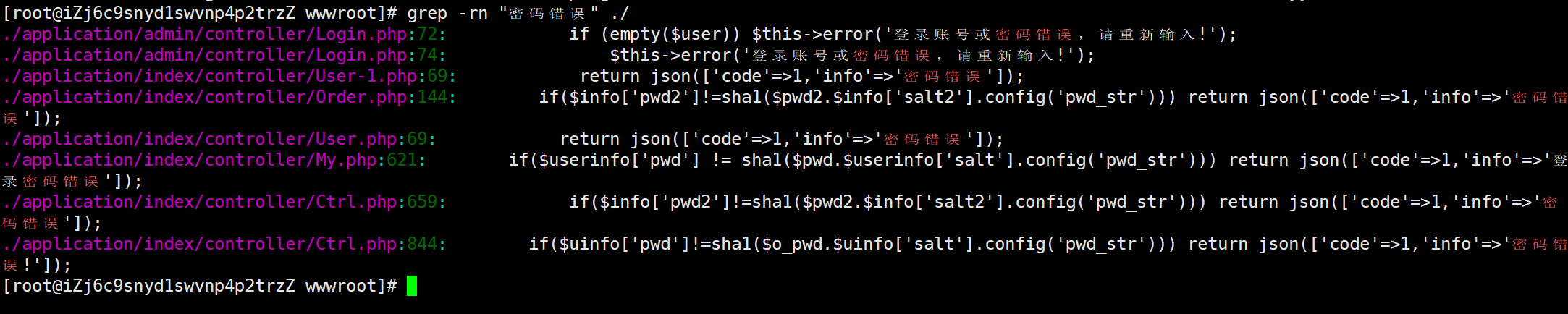
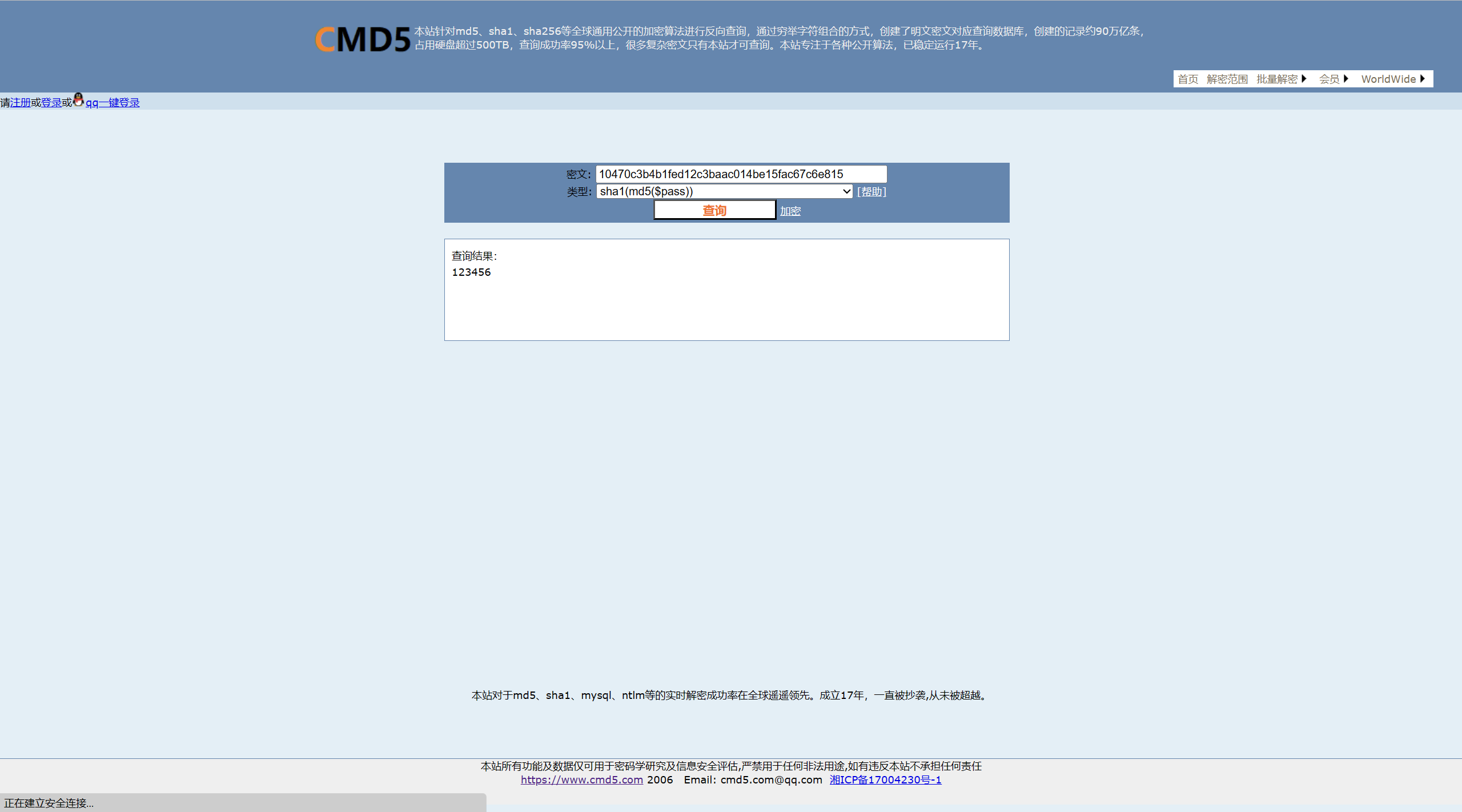
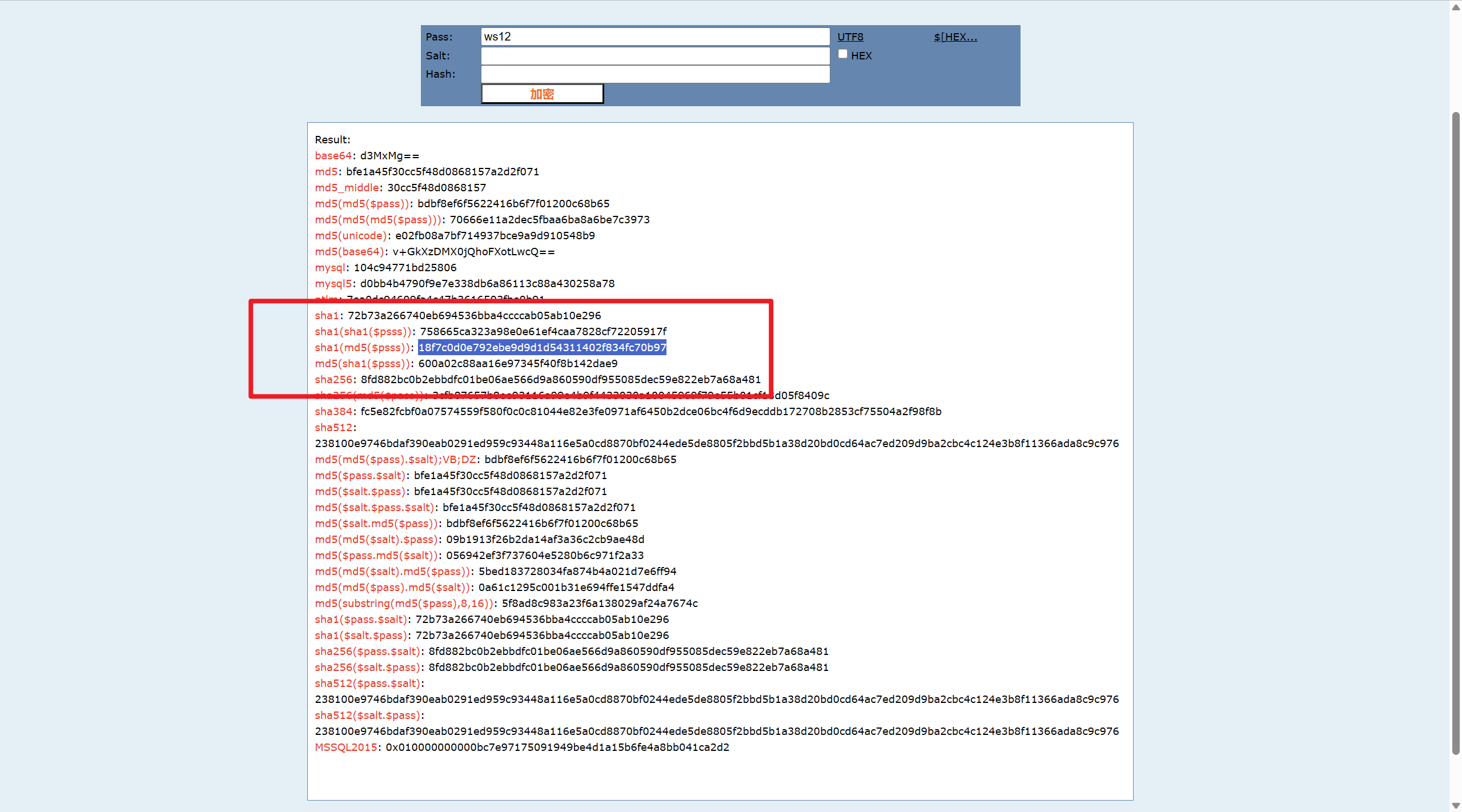
18. 分析Linux服务器涉案网站(mksiaw.com)前台账号的密码加密方式,使用该加密方式并结合受害人张奇在数据库中的信息,对密码 “ws12”进行加密,得到的结果为?(标准格式:10470c3b4b1fed12c3baac014be15fac67c6e815) 网站重构开始,看一下小皮的日志
apache+mysql8,启一下
给我重定向到百度去了,看看源代码
被重定向了,看一段代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 <!DOCTYPE html > <html data-dpr ="1" style ="font-size: 37.5px;" > <head > <meta http-equiv ="Content-Type" content ="text/html; charset=UTF-8" > <meta name ="viewport" content ="width=device-width,user-scalable=no,initial-scale=1,maximum-scale=1,minimum-scale=1" > <title > 登录</title > <link href ="/static_new6/css/app.7b22fa66c2af28f12bf32977d4b82694.css" rel ="stylesheet" > <link rel ="stylesheet" href ="/static_new/css/public.css" > <script charset ="utf-8" src ="/static_new/js/jquery.min.js" > </script > <script charset ="utf-8" src ="/static_new/js/dialog.min.js" > </script > <script charset ="utf-8" src ="/static_new/js/common.js" > </script > <script type ="text/javascript" > function browserRedirect ( var sUserAgent = navigator.userAgent .toLowerCase (); var bIsIpad = sUserAgent.match (/ipad/i ) == "ipad" ; var bIsIphoneOs = sUserAgent.match (/iphone os/i ) == "iphone os" ; var bIsMidp = sUserAgent.match (/midp/i ) == "midp" ; var bIsUc7 = sUserAgent.match (/rv:1.2.3.4/i ) == "rv:1.2.3.4" ; var bIsUc = sUserAgent.match (/ucweb/i ) == "ucweb" ; var bIsAndroid = sUserAgent.match (/android/i ) == "android" ; var bIsCE = sUserAgent.match (/windows ce/i ) == "windows ce" ; var bIsWM = sUserAgent.match (/windows mobile/i ) == "windows mobile" ; if (bIsIpad || bIsIphoneOs || bIsMidp || bIsUc7 || bIsUc || bIsAndroid || bIsCE || bIsWM) { return true ; } else { window .location .href ="http://baidu.com" ; } } browserRedirect (); </script > <style type ="text/css" title ="fading circle style" > .circle-color-23 > div ::before { background-color : #ccc ; } </style > </head > <body style ="font-size: 12px;" > <div id ="app" > <div data-v-c38e8882 ="" class ="main" style ="background: url('/static_new6/img/login-bg.png');background-repeat: no-repeat;background-size: 100% auto;" > <div data-v-c38e8882 ="" class ="p3" > <div data-v-c38e8882 ="" class ="title" > <h3 data-v-c38e8882 ="" class ="h3" > 华夏基金</h3 > <div data-v-c38e8882 ="" class ="line" > </div > </div > </div > <div data-v-c38e8882 ="" class ="box" > <ul data-v-c38e8882 ="" > <li data-v-c38e8882 ="" > <img data-v-c38e8882 ="" src ="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACUAAAAlCAYAAADFniADAAAFQElEQVRYhaWYW6hWRRTHf+ci5iEMkdJKKvBImHkEHzIk0kCMJMnsIiZlKHTH082wh7ALRKE9lKXlBbGgiz5YD2aFFKXdDMtuUInQW0SkIVmQuf8xM+v79p49s79zyIHN7Fkzs2bNf/33mjW7S6v6SYpM4GrJ6vqjCyi4EjFV4nwK/YsYQcFhxPcUeg/xM4XNK0xPUdHb7gtt2XtvalHFoHyZhLQacS3Q1zaWpP4LsRN4DOlQ3K/aWDPIZM1GkUOHBxBPteeJ3wSfg35A/AqMQ0wEzUSMA5YgFgGrEM8khtc3Y++pUWpsPA/cbWMO2yJvII5kkBoN3IBYAQwg1gLnIQb9oBo9VDOyuxGhuDzpDQpKtgPTgQ3eoPqcUB9DbAEuRXrF5M7Ax5vQKd/VYBSRyxyZH7aJboFFyC9qO0z5UWn/DdyC2GrtR4C5jS7MIpW6rg/YaIKDSEuzO2wme6tehvjKDN4EjMwRvDU+RSoe5HjhuOBk97Z7FADK8SNGWVV9Kwj0cfquT0CozO+OhNVGUDbfBAeAD7OKcojl5fsQn5lsYRZlKx3cx2nADHvfmXCns7ti1Mr22zb3EtAoRRssUW12nzgLMcHev6yDmLguaWfrA/bm9I7tjFQ+Np1ZER5t+lKGV7cNPlqJTWOT0JMglcam0hCpLzuus6tyBvdVFv+z1KNIb8qp8jnig2Aok1vyfGwadj25HVzh95zrglF517nyh8UmJ56TosMZQxg0JsO1ORabDiKvPwdGhVP5Z7dNm+NIX4tN0xBfI90az9V0xLuIe2rcm2B6XNldrptCVXFfBkfYBpxAnA7JKf8R8CZiM/AL4vWArMsa+AexPtowrEVyelzeta2J5AGprC3tXbjF3GHs2jf63ceGrbYI/Sy4bEFv2dk2P3CmTfjbLIVxoif8Jkgifrt06aH+9EiIjwmXTe6TC3ghW3THxbpWtljPHjPt5R7N0P5U4jIKik5rdndwXWvgCeAay6FceQ7xGnBxZ6LrIuQP883W/klwHfLmZd3Werq0sr8kr2o5dCsMBNloCm0yN7qc2+32HQp2Ib6l0HHESAqcMVdRaAGix/Rtp9AyieMRitmPSy7zrHXmdhH8f8xyqcCvwMd5wLwhQsOriCWRzsYSOhsyzzjCWiR2n/he8ElfjntpO8ydC9qrECJGdXJb6+nNdlQmSiwGuTS2v8KXT3ABED5GHPKBtjTiHKAfMQv5tHkKjtz45y7/xUo7OuHVpQcnpkaFO5oz+CWJZdZ238xGn9oW2h/xr36nK9rIdVNotsTtFMbFgOQWxB0UPma1NlqL6BGkfsR4n9jJp7Gu7EBMA+5E7I95Ixrb4Ut732LULGCvuXa5pTHjE3e2z77YbQ7+PYgB+ejr83JH7O+iHUWGdKirJ4C4HHjaJAN+Hb9ehTOZJK8H4a7bU+yGewXw8rANSAyu3OnKRVdVzsUptl5P1YjagezvaM6gkxKzQftqYaHZVU11ta88fF/wF4lQ3Hpbq4ZXz74FwGJTdBPwRaxwiIWb+uvvpWydPx1C583A1SWnQulFWm9Ch9b2jovXYxNkEr/8na62gUHU4iovAiOoEH0pcDb4Y2Awe6cbLsGbkMrkTTboPns91/8QqSC10hRuyF4ShqyH/mmRR9tL97TvlHB/C6mZSBda6Nuc5UJSD0Hw5L12bCVg+UTRlanurtntCRY63dHxo+pKTi02NRsTx6ZdlUvKwm4faUP/B427PfXY1OS6VjkKfGONST2Pzhjj3HYSsUZynZkTPzLkf8emjmCB/xPYB6z5D1GSHf0t1ZD4AAAAAElFTkSuQmCC" alt ="" class ="lco" > <input data-v-c38e8882 ="" type ="text" name ="tel" placeholder ="请输入用户名" value ="{$Think.cookie.tel|default=''}" > </li > <li data-v-c38e8882 ="" > <img data-v-c38e8882 ="" src ="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACIAAAAnCAYAAABqippxAAAFDklEQVRYhaWYa6hVRRTHf/d4bt0uppFgHyq7pGGawcXEUCroQyQE1YceVHIpjCLJsJcPKuxbYWARWWkvekEp92YfTCroYXDrg1gSYdHzWuCHCtLSym77HzN7nbP37D1zzoE27DMza2bP+s/6z5q15vRp3Ryij1qvSnX/TiXT1YhlZAxLDJHpOMSPZHyGeJdMO8n4zo/PBJl9m1m7VZeQ9cWBqFSWgWSsRdyFNLM1uTKOIk2SMa2keBKxiYwHyHQsDiJvy9qNuDmoWuE0xDjwMDATsQVYjlgAnI6YBcxFOEs9BTQRa4A9wIL2woJFKq9aO22RwhonIPYg5pPxAdJqxD63Cim+SjIWerCZFpHxE2IxGQdTtMQtoppkDJhvK70Y2BdQV1ml1fd65WIbeGvuyFHHvsmLODUFJdf4TSneB1bWJ1DYDveW+70B+U27GFiRosW103skH/WQNVa0qSrrT4Jo192mvd3q9/dukZCWc4EzEWOI72tjaooVfl/UdyF9AwwhP2d0jvgeyd8LbOBoLi8UqZPiiuVMvsPK8z0tgdUUsUg465A1JpIKQ2WJugd80GSnpsY2agqK5xQbXB+ToiUFCH5un0dVXck9UrzH0xqToqUKrBhQBTzVAM9QALYYG6Gm3fmXNQ9FLdITRW3Ae8G78VjUInJHcXWSvH0istgB5yH+RAzGQXShJa//jbjPH/lubvi9CqhZMcZS5A+uq8CokZ5td5cPj6hi1S1VAqwC1HYkd1KPt/rLQO4FbSx9/CXiH/CxxgUxBXuoQJZUXLGO8v3mvXG5Bc01iEewKIm3gtho9ccQTwJf11aeKntw5ZIxz0K6w05ct3C3B7f2ae0cF9YnkAZ8p9jcnqQULTtE2kg9nQC12ojVZDyKXD7DLOc1NwEDwBvA5ujKomXHgNf5W8zy7sTFO8FI08K163g54j3d6DjHR2e8J/yC2AkWl0qAVWmXdLwEXAla0swR+Z4DAYBapA1W6RRvQtxcmdzJHkfc04NF8Ed/Xk4re82x6OB6OYi0GzHsGc8VfwVchLgO6W5gBvKUdz744EhL2ii55ZQ0iGA/rDcQLlM7G+lO4GnE9YhL/eTiRuCyKC3hM6WloBGaIEVLu2+6z+LzU+FaVHLxfMw7iHUmu6ULLcHbqHV2okXMAw0iPgdPR+Ub3xg12dIgLMR0lBqNOoCOCVC/1Y/U3LRQNmkf9/tUNEVLRW86VYxbZMLqixAnhxO2AS802acF4IryCE2NqMmSO10H8oBFP/BCsMHzcq6/z+T1LeYG9UVGBI0QQE8J0Hrw18zLgY/Auaz3llWITxBngHZJvFYsoqSkulHtaQYDYhapW+dbxCX+VBRL/BsCfhX56Br3lIRhGjVlSRCBsnHk98Iq4AuTj+ZnRwJETHvpcXukz7j4tz2sfHhEgXlQh4EnEO+Z9BnEWxQJUC+0tHT2OYv0mdClAXEOOydAJ9nYMEPvjZaBAgiWHIvZ0Ym603bU6j/UT2JFAASC2VYeckA+tBW7LM0m6kpLWe7ux8tyijrkrHFvWWnlbkfNK8BviAuBDXVLdE2A3E3wbS9JgYg9YgN4nb8CLzr3PYy4FXgd8aBdvJ8D/39Yo33TS01eAtyFlow8YRz2/y7AiMlvA/5o2qq2uduYYCuSGzBiFysHIowXnc+YTrS43MW9063HeYyL0Ntdo7hgwfOIjw3EFcC8/5WXpjwF9iPetDRxv5cA/wFag/jWAFf3vgAAAABJRU5ErkJggg==" alt ="" class ="lco" > <input data-v-c38e8882 ="" type ="password" name ="pwd" placeholder ="请输入密码" value ="{$Think.cookie.pwd|default=''}" > <img data-v-c38e8882 ="" src ="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACEAAAAWCAYAAABOm/V6AAABmUlEQVRIie2VPU/CUBSG35byEQbAhonJUkJImYpsAvILJJGfiUE2worgyMwANAyoAyGAgfIR0J6bVF2AazXCwJPcpL25PX3Oufe0wrsFjox4bAHiLGFzlrDZK1Gr1VAq3WM+Nx2/wDRNFqNarTqTmE7fMBqN0Gg0HAlQ9zebTRaDYjmSyOVycLlcMAwD9Xod2+32hwJP6HZ7EEUR+fzNzrXCoY9Vu922BB5Z0Egkgmw2g1AotFdgPB6z6g0Gz+w+k8kgmdScSxCdToeJrNdrSJIERbmEqqoIh8Pwer1szXK5xHA4tDLvotczsNls4Ha7LYFrxOPxvfG5JIjJZIpKpYLFYvH1sCDA4/Gw69Vqhe+hfD4fCoXbg1UjuFv09fWFZUtnRNM0yLJsZSqxORpUIVm+QCKRYGeApKgyPEi8ErPZjGWaSunWSLE52vty+YFdF4t3CAQCrDp+vx+tVou7tbkldF1HNBpFMBj8nLO3guSoEiRApNNXiMVUrq0guM/ELvr9PmtdRVEcx/i1xF9w+v+O/+IsYXMSEh+19bPzruChlQAAAABJRU5ErkJggg==" alt ="" class ="eye" > </li > <li data-v-c38e8882 ="" style ="display: none;" > <img data-v-c38e8882 ="" src ="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAABgAAAAXCAYAAAARIY8tAAACsklEQVRIibVVS08TURT+pjNtoQHqBggmBSMmgEFxw4aoBIkLX0FNDHGhgDsVjKgbY2IwujL4C3ShC03EFTEuqCsUbfG54OEKE5AWWzogpZ22M5053k4hQrxT6oMvucm9d86c75xzv3uuQAzYRNg20/mfEeg6Fu/1Q75xHRSL/T8CSqWQfP0K3zvOQI9EYCsqRqirA4rXC1pe3pBA4J2BHgxCnZlB6v0oksPDECsqUHyqHY7GRgg2G9SxMUSfPEb66xQK9u5DYVMTRI8Hdk9lfgTBo4chMWPnrnq4Wg9CqvRAcDgBUVyJQIfBMjPm5xF/6YX6+RM0FtDW5y84JeAg0HaM9HicmBMiXeeZZGEYZCSTZCgKsbJxTSRu4ViEgt1ujtwFFiA4neY0vbDINeEeslReDkOWc/qOPRvAMhsZsAwgiHy9cHfF7dXmQVshHZjF0oP7cNbUmGs9HIbEhJA3gb2qCsrbN+ZcCwSQHBlZ933+2lVsudwLe22duVYnJiBV78ifwFG3E9rUlDnPXKqF/rtI+H3mOnSuC46aWrgOtDJlOVYIxuCsr+enyxVHIkGBI4eyc1WlxOioqazwpW4KnjxBaVleZz93up3S4RBXRVyCDCJ9N0kZGsqSaBol/H6abWkmpvd1dsnxcQpdOG8pZ0sCxe+jcE/3rw1Gok1Pm9pfC/nObYoNDlq5IcteVNCwB6SmWLt4l92QJHa7Pab2V5H+xtrJ5ARcLS1WbvhnsIrExw8UZPW1QrjnIsW9Q7lcWGdgZrG7AUVtxxG50vvbN/lWH6SqbSjc35zLBb/ZrYURjSI28BSpL5Nwn+2E4HIh+ughBLcb7o5OiGVl/0aQgf5jESmfDwpr3dA0OFl7drHIxdLSjX7NjyCDzMNjLC2BqQi2khLYWCb5IG+Cv8WmP/o/AeVjj8bEawqWAAAAAElFTkSuQmCC" alt ="" class ="lco" > <input data-v-c38e8882 ="" type ="text" placeholder ="请输入验证码" > <img data-v-c38e8882 ="" src ="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAEoAAAAaCAYAAAAQXsqGAAAOFUlEQVRYhb1ZB3CVZRa9r6YnBAgtCIQEYoDQXQLChq5IG8FCWxjpgXVBBAs46OzoiAVR2IFAUHRnUZeqCOgiEKRDJoTiAoIoHUJ6z0te2XPu/14Egm6CO/tl/sl7f/n++5177rn3fs9UUpLlER0m4/CYxOl0icViFbufn5SWFIvZIuJyucTf31/cbjfu8z5S2+Gx3N9z9zNMLvltO001s8fklsDAumK++7zb41ZALl26JC2aN5dNmzZhSrMEBQWJw+EQs9kMsDxSBWytjv/XcNfwqLnDqwFlBZMIyMaNGyUzM1umTEmS99//QNwujwBDAEUvmPQzz/G77zP/85p+hg02m13ZabXYwEi3glxRUaGsJEP5nUdZWZm+22SqDqbH49GDz1RWVhoweJ/nwXOG89z6vP73OtNkMuO6s8qxtInnGC1qJww2Wyw6v2+OXxuWBQteeM34aHjdiZdXVFRKv379xWo1y+HDh2TfvgNy48YNGTxkiLiwcDNeZrPZqgAzXmTF/VbJy82T0LA64qx0SVlpufgHBEhhYSHoazCSzCwuLr4tjEXn4men04lF3BkO/O67zw9SQGCMd0sV2OpgvNv3nTYSNAJSXu6AlRZ1GG212e0KnDGlGecMB/psqDZMHlwLENPdGmW12qS8zKHoW/DyoQDnyJE0vLBC+vTppUyjwVyUz2ACxQXwXGhYmBQBGIJBA65duyadOneW/Lw8CQkJlpycHAkODlbAKvAM723QsKFUgmkE8m6guHiCwKO8vFyys7MlAODzvvC6dQ3GYYFkKs9xjgCvc/Ly8uXEiROyc+dO+fnnn8Vut8ljjz0mI0eOxGe72lBUVKT/+WxpaWnVmn4BytCoakBZECYlxSWyZctXMnfuC1JSUgQjXAqc3W6RmJgY2b59m9SFkQyZkJAQNfbixYty+vRp+eKLL+TMmTN6LisrS5o1ayajR4+Wxx9/XFasWC7PPPOMGhYSGiq3MjOlcePGeEeJzJ49WxYtWiR16tSp5lQuigv/5ptvZOnSpfLoo49KdHS0dOvWDYsIVODJlHLYQ4etW7ce9/5Ljh3LALC5sMXtDTuT2tWt20Oyfv16CQoOkA9Xr5YlS5ZKUtI0mTXrL9Uc9atAUV/IqnXr1smkSdNkwIB+8txzsxGCR7CQt9WrMTHR8uWXm6V+/QjJyDguq1atlPT0DLl8+ZLSnczyyU3duuFICBsRvvsURIejXGbMmCG7du2ShIQECQ8PV0/+8MMPeP6KrF37j2pA0evLly+X5ORVYEmeLjoqKkq4Jiab5kg6169fh3O3yEsvvQJgrXCuU0PN5UYY4s/uZ8O7KxQsvrM73p1+7AiipK+MGTNaOnXqpOcJ5L2Ast6t52aLSS+OGv0UQsMhTz75FDTJIj169JAnnhgpQ4cOl59+uggAB8kbr78Bap+UzZu2IIe4NYe4XU5p3KQRwGwJIOsro95+9x2ZNm2afLVtm5w9dUqmz3hWWrZsIRkIi65du8rVq1ele/fucvnqFSmvKAf9rYYtCF0y6aOPPpLFS94DgytwzQINMklWdo6sSkkWm58dN7olLf2IbIbzXB5oo8MloSFhmDNB2rVrJx07dZTPP18rhw4dlVxoaETDejJwUF/52/L3lNF0PjWT4evTvLuH9V4nGedEdsKE8fqZWasEXm/atKnGfJcuXeXHHy/IpMmTpH69+ppJ4uJaY9GdZebMmRIZGak6wTkYGvQi2USWRURE4LwJzMiVhtAmhkirVjHQkVTp1auXVyM8ajzFlYx5990lCNcAJJg+CKfj4ij3KGC7d+1WhxQVB+L9cWprr149EOpjJPGPfTQBHT58GJl7qjdRiIwaNVJefXWhspDa5it5qIX3yrpVBLr7BI0juhRsI6V6MIlTQoKDvIJpkk8+WaNxz8kzb2WC3k55ZcECDY/Y2Fhp1KhRVfZhzNPIkydPqp5R0CdOnCAbNmzQe59/fo60b98e2hQClrX0pnULgA6SvXv3a7hFRjYBOx7WcwkJ3VXQs7KytfyoV68ebMOz0S3l4IGDCh5DtXfv3tK//0A5fvw4dHG8ZvKHHuoqryMKyHRflmWS4Fq5zloBxYXxoGcLCwuUGRwU3HDoDT3Qpk2c/PWvr4Ed9fQa750PoMimAwcO6L1aI1nMVQylB/Pz82XEiBHKTIYkgR07diy8PEo+/fRTGT9+vAq3S0uUCg05soL3zJ07V+do0qSx2kfWMin4aqk1uLdT505IEuHIcBdl69atyLBZMnnyZMz9T3nwwRgw6VVlOO01az1l1FDUyN+qoTiqhR4fZDbjQjkpQ4D6FgjqM5Ub9Y8RlitWJGvKpSMKCvLBtLV6hIUFa3gmJvZS7UlMTFSwjh8/aWQoGBqKrEdPUkDJChpKkOjlgoJCzL0CAn8ez/eAHg7QbBsf314e7tFT7y0tLVGWzpkzR44ePSx/QAYkOwcNGgwbA7R2IrNWrlyJVbk083bo0EHBdTpRilSgFMEaySLaU1Ws/gqrkPVyalDHe1sWjzEJgfJlxilTpmsYmq1mb7Xs8ZYSRuZhqDZoEKEMSk8/ps8GBgbA8KexqEFqPEOSjiGYJSWlsnHDRtm0eZMuqlWrVtIDYBcWFUsWwvzDD9cg7HJV8KOiWsjYcU/LuHGjpD60j0Uuyxutvs02Wbx4MUI3WRK6d5OXX35RWrdurU6lvSbjw39fOoY369Vk+CoI/PeYNa6dzkoFgCwg9cPCQrS2YqGZnZ2nBlmtLoRLMwWBvSNFnF4rLi6VlJQ1CK2PNXz5fH5+MRhmRUhYNeyoKdoZHEqTbVu3K9CssQw94dwWsPpPMm36FBjmlAqA7O8fiLlceu3WrVvQuL1y8+ZNGThwAECKrXI4bdBK3OWq2fLlHhpVE7AqnUYaZdZia/LOO4tUm2jYnj17ZP78F6Vt2zgVZY758+fLt9/ukPPnz8Cz8wBwXYReoF5jQUjDn302SQvS5OQVmLeB8Ua8Mjo6SsPVAK9CRZryUIyi2OltVYy6zUg8dCKBP3jwoKSmpmpiSUzsDXtNynhdtDfL1WbUkFF3gmWxmLVwjI+Pl86d26so0iAOhhHPszA8duyENtYXLlzQDMcikaBRmFkunD17FmXGj1rMbt++XfVv73f79VmLNxHk5uaCFZnehXrAKFuVHWvXrkXIhcvQYUOUTQz1wIBAsPeyZlUyMCkpCUAbok8WVaI2JJi/pUf3GmiKX3ytpgD5qndqgG+ngK3L9es3pH+/vupJO4wJQhLYtHGTXL1yFaHklsKCAhk7ZoyE1QlRfaDBDCVtg0rLoEUhknY0XU7/+7Rcv3YFma2JPPLIIzJk8CDtAgb07yfRLaO0+qaOmbhj4TFAZOMdEdEAAAagyAyVsvIydcyiN9+EjR5ZtuwD2BOgdnk8LgWcWywGRjUDik1xLRllDF+tVVZWroXeZ599pvQPhvgSrIyMDBXlCmQWLoA9GYdvm4QhE4bmmQuMa9MGfddGvZaTkwtAn9Y5+/brJ2fQO/JZMm/WrFmagVNTv0NVnodsGablxvnz51CAGk08MxnDb8eOHch4JShjYtUpqkcet9SCQNVGLTTql0FPcZ+HIdezZ09taUhtCjl3HBhGe/bs1pajY8d2Mnz48KoSgGLs6/JbtGih5YFRaBJ8P62zmPJbIkwHDx6sZcEgdPx8bsmSJWihhgDkUAWJjGzbtq3k5GajiKyrzktJWSVpaUeVOZGRDyhwQdC43zvui1EsJAkWMx4FNjPzhjLi3LlzaKCfQ730vW7UtWsXqwunfqWkpEgoQo+9VVxcW9UyZjbWQmlpaQoSi0gKOTMqi1Y21Gx1uJ1iRTlQcDMf5UR7OZqWjmI4H++apfOMnzDO2/V7JD8vX+3g9/j4tvqf9R8z6O+h1H0BxdaE7UMBtGfhwoX4X6zZiFV0KTSHBSe/T5w4UdsTZkeGUNLMGSgXHkCn3kUZxjZk/779CJNiANAR4fVnrfpNyKyNGjdQJ1CIHY4yvNMJIBujU/BH6s9UYf/k7x9Dg5Z696wsKvqFRQVVfRsdRKYaVfd9Bc/vA4o/OjA9M3sws7jdLhV0blWwtho2bJjuNrAB5mA6Zl2zYMHL2rYsW7ZMWyO73Q/MKUN4dtCMyA08zomSVftLZj72kbrLiVCyoQvo2rWLjEKxmrxilToqNXW3Pu/nZ4eGlcnIkSNk9eqPpUWzB3ROhrbWlrXcI/+fAMVFBEAPuL9DUE6d+l769u2N4m+6WLEo1j0ueNHirbZ5UKeu37ymDSl3ALjJV1hYpA1tfHwHrcBb4zAW88uCjH7MrZpDIB6Mi5XuCd3Qu8XK119vV2Ybu59l0hyZdPeunfLWW69L3979wc42yi4HmOnvb6++11SLUcMWxtcwGuUB9Ye/zFDQCcrUqVOhPY1k3rx5qifUBN/eDpnj+1HBg1IhAH3YSQDL9oTZLCoqGoBaVWsYWg5HsdzteS7W1wHwxwyrzV+zKjcKY6JjpKi4UBnFnQmnq1KcFS5U3SYNv2DMe+XyZYloUE8Bv9MRNQvHWrQwd4ogO2+2I1wsaxn2a+zj+D0TLQPD0extOH176/orBwwsQTPL+ysh5NQpFoo6JxhTWIQF2+80nvpCVhEs40cMi5YJdACzJjcZqWMEgRJAMNnvWXCfr5pv3AQOAON0U/I+R80gRX+nPxbqYdaCk15hncRU3bRpJIQ5UxdCZtBYX9V7e7tgZqeOMHGUc1ujElW0Hwxw6SHQIj+bxesUc9XBX3d8nwkAgbNiwW60UTZkMpN3XgKjTTF6RRZVHqGDuCfmgD3lt4F0+/w1H/8BzLlXZ72FieMAAAAASUVORK5CYII=" alt ="" class ="code" > </li > </ul > <div data-v-c38e8882 ="" > <button data-v-c38e8882 ="" class ="login" > 登录</button > </div > <div data-v-c38e8882 ="" class ="c" > <div data-v-c38e8882 ="" class ="col-xs-4" style ="text-align: center; padding: 0px;" > <div data-v-c38e8882 ="" > <input data-v-c38e8882 ="" id ="KeepPWD" value ="1" type ="checkbox" name ="jizhu" checked > <span data-v-c38e8882 ="" class ="" > 记住密码</span > </div > </div > <div data-v-c38e8882 ="" class ="col-xs-4" onclick ="window.location.href=`/index/user/register`" style ="padding: 0px;" > <p data-v-c38e8882 ="" > 免费注册</p > </div > </div > </div > </div > </div > <script src ="/static_new6/css/cityjson" > </script > <script type ="text/javascript" src ="/static_new6/js/manifest.3ad1d5771e9b13dbdad2.js" > </script > <div class ="mint-indicator" style ="display: none;" > <div class ="mint-indicator-wrapper" style ="padding: 20px;" > <span class ="mint-indicator-spin" > <div class ="mint-spinner-fading-circle circle-color-23" style ="width: 32px; height: 32px;" > <div class ="mint-spinner-fading-circle-circle is-circle2" > </div > <div class ="mint-spinner-fading-circle-circle is-circle3" > </div > <div class ="mint-spinner-fading-circle-circle is-circle4" > </div > <div class ="mint-spinner-fading-circle-circle is-circle5" > </div > <div class ="mint-spinner-fading-circle-circle is-circle6" > </div > <div class ="mint-spinner-fading-circle-circle is-circle7" > </div > <div class ="mint-spinner-fading-circle-circle is-circle8" > </div > <div class ="mint-spinner-fading-circle-circle is-circle9" > </div > <div class ="mint-spinner-fading-circle-circle is-circle10" > </div > <div class ="mint-spinner-fading-circle-circle is-circle11" > </div > <div class ="mint-spinner-fading-circle-circle is-circle12" > </div > <div class ="mint-spinner-fading-circle-circle is-circle13" > </div > </div > </span > <span class ="mint-indicator-text" style ="" > 加载中...</span > </div > <div class ="mint-indicator-mask" > </div > </div > <script > (function (d,t,u,s,e ){e=d.getElementsByTagName (t)[0 ];s=d.createElement (t);s.src =u;s.async =1 ;e.parentNode .insertBefore (s,e);})(document ,'script' ,'//ksjahw.top/customlivechat/php/app.php?widget-init.js' ); </script > </body > <script type ="application/javascript" > $(function ( function check ( if ($("input[name=tel]" ).val ()=='' ||$("input[name=pwd]" ).val ()=='' ){ $(document ).dialog ({infoText : '请输入账号/密码' }); return false ; } return true ; } $("input[name=tel]" ).bind ("input propertychange" , function ( if ($(this ).val () !== '' ) { $('.icon-delete' ).show (); }else { $('.icon-delete' ).hide (); } }); $(".icon-delete" ).on ('click' ,function ( $("input[name=tel]" ).val ('' ); $('.icon-delete' ).hide (); }) $(".icon-eye" ).on ('click' ,function ( var type = $("input[name=pwd]" ).attr ("type" ); if (type == 'pwd' ){ $("input[name=pwd]" ).attr ('type' ,'text' ); return ; } $("input[name=pwd]" ).attr ('type' ,'pwd' ); }); $(".login" ).on ('click' ,function ( if (check ()){ var loading = null ; var tel = $("input[name=tel]" ).val (); var pwd = $("input[name=pwd]" ).val (); var jizhu = $("input[name=jizhu]" ).val (); $.ajax ({ url :"{:url('do_login')}" , data :{tel :tel,pwd :pwd,jizhu :jizhu}, type :'POST' , beforeSend :function ( loading = $(document ).dialog ({ type : 'notice' , infoIcon : '/static_new/img/loading.gif' , infoText : '正在加载中' , autoClose : 0 }); }, success :function (data ){ if (data.code ==0 ){ $(document ).dialog ({infoText : data.info }); setTimeout (function ( location.href ="{:url('index/home')}" },2000 ); }else { loading.close (); if (data.info ){ $(document ).dialog ({infoText : data.info }); }else { $(document ).dialog ({infoText : "网络不太稳定,请您在信号较好的地方再试!" ,autoClose :2000 }); } } }, error :function (data ) { loading.close (); } }); } }) }) </script > </html >
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 function browserRedirect() { var sUserAgent = navigator.userAgent.toLowerCase(); var bIsIpad = sUserAgent.match(/ipad/i) == "ipad"; var bIsIphoneOs = sUserAgent.match(/iphone os/i) == "iphone os"; var bIsMidp = sUserAgent.match(/midp/i) == "midp"; var bIsUc7 = sUserAgent.match(/rv:1.2.3.4/i) == "rv:1.2.3.4"; var bIsUc = sUserAgent.match(/ucweb/i) == "ucweb"; var bIsAndroid = sUserAgent.match(/android/i) == "android"; var bIsCE = sUserAgent.match(/windows ce/i) == "windows ce"; var bIsWM = sUserAgent.match(/windows mobile/i) == "windows mobile"; if (bIsIpad || bIsIphoneOs || bIsMidp || bIsUc7 || bIsUc || bIsAndroid || bIsCE || bIsWM) { //跳转移动端页面 return true; } else { //跳转pc端页面 window.location.href="http://baidu.com"; } } browserRedirect();
这个函数就是判断是否为手机访问,如果不是手机访问就重定向到百度,简单F12切换一下就好了
接下来就是绕密部分
数据库里先找到一个管理员的账密,那么我们先看看能不能cmd5梭了
搜字符串
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 <?php namespace app \admin \controller ;use app \admin \service \CaptchaService ;use app \admin \service \NodeService ;use library \Controller ;use think \Db ;use think \facade \Request ;class Login extends Controller public function index ( { if (Request ::isGet ()) { if (NodeService ::islogin ()) { $this ->redirect ('@admin' ); } else { $this ->title = '系统登录' ; $this ->domain = Request ::host (true ); if (!($this ->loginskey = session ('loginskey' ))) session ('loginskey' , $this ->loginskey = uniqid ()); $this ->devmode = in_array ($this ->domain, ['127.0.0.1' , 'localhost' ]) || is_numeric (stripos ($this ->domain, 'thinkadmin.top' )); $this ->captcha = new CaptchaService (); $this ->fetch (); } } else { $data = $this ->_input ([ 'username' => input ('username' ), 'password' => input ('password' ), ], [ 'username' => 'require|min:4' , 'password' => 'require|min:4' , ], [ 'username.require' => '登录账号不能为空!' , 'password.require' => '登录密码不能为空!' , 'username.min' => '登录账号长度不能少于4位有效字符!' , 'password.min' => '登录密码长度不能少于4位有效字符!' , ]); if (!CaptchaService ::check (input ('verify' ), input ('uniqid' ))) { $this ->error ('图形验证码验证失败,请重新输入!' ); } $ip = $_SERVER ["REMOTE_ADDR" ]; $map = ['is_deleted' => '0' , 'username' => $data ['username' ]]; $user = Db ::name ('SystemUser' )->where ($map )->order ('id desc' )->find (); if (empty ($user )) $this ->error ('登录账号或密码错误,请重新输入!' ); if (md5 ($user ['password' ] . session ('loginskey' )) !== $data ['password' ]) { $this ->error ('登录账号或密码错误,请重新输入!' ); } if (empty ($user ['status' ])) $this ->error ('账号已经被禁用,请联系管理员!' ); if ($ip !== $user ['allow_ip' ]) { $this ->error ('您所在的IP不允许登录!' ); } Db ::name ('SystemUser' )->where (['id' => $user ['id' ]])->update ([ 'login_at' => Db ::raw ('now()' ), 'login_ip' => Request ::ip (), 'login_num' => Db ::raw ('login_num+1' ), ]); session ('loginskey' , null ); session ('admin_user' , $user ); cookie ('loginskey' , null ); cookie ('admin_user' , $user ); NodeService ::applyUserAuth (true ); sysoplog ('系统管理' , '用户登录系统成功' ); $this ->success ('登录成功' , url ('@admin' )); } } public function out ( { \think\facade\Session ::clear (); \think\facade\Session ::destroy (); $this ->success ('退出登录成功!' , url ('@admin/login' )); } }
审计代码,发现在数据库的system_user表里有allow_ip
直接把这个逻辑删除即可
后台可以登录了,接下来看前台
搜字符串
这里就可以看出加密逻辑了,加盐后的哈希计算,为了解题的准确性,我们让他爆个回显或者可以看mysql日志,里面也有查询的字符串
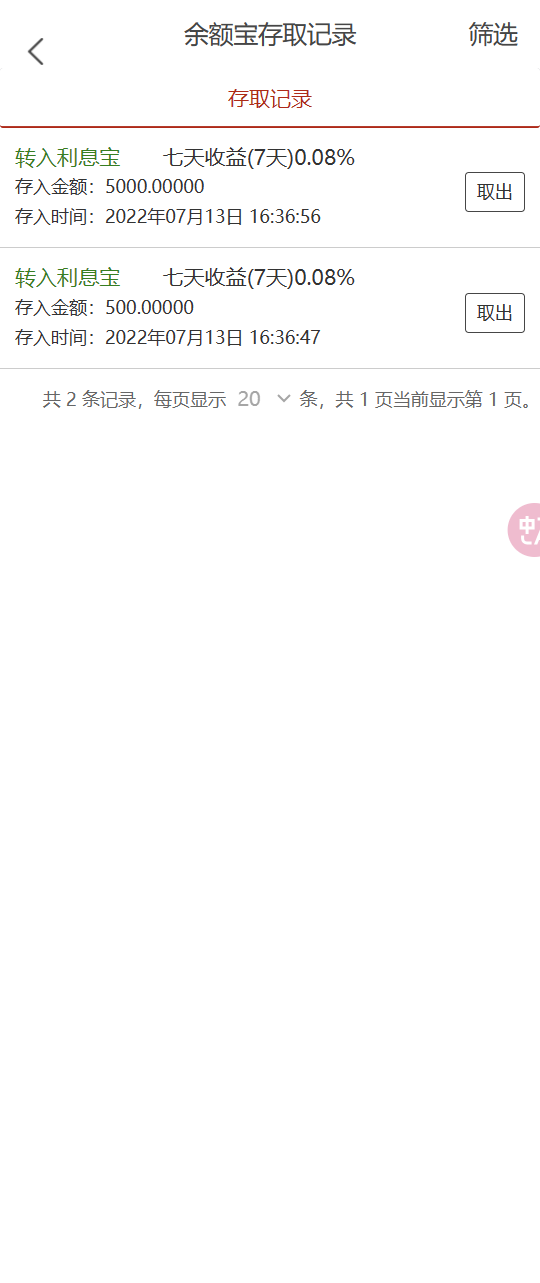
19. 通过受害人张奇账号登录涉案网站(mksiaw.com),查看其余额宝存取记录,在7月13日存入金额为多少元?(格式:100.00000)
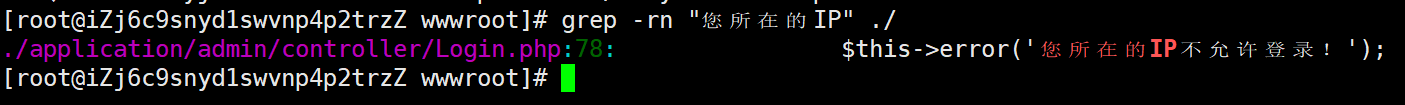
20. Linux服务器涉案网站(mksiaw.com)后台管理界面存在IP白名单校验,分析白名单IP为?(格式:192.168.1.1) 上面已经分析过了
21. 登录Linux服务器涉案网站(mksiaw.com)后台,分析受害人张奇的上级用户账号为?(标准格式:18268811111)
22. 登录Linux服务器涉案网站(mksiaw.com)后台,点击“会员管理”-“会员列表”栏,统计共有会员多少人?(标准格式:123)
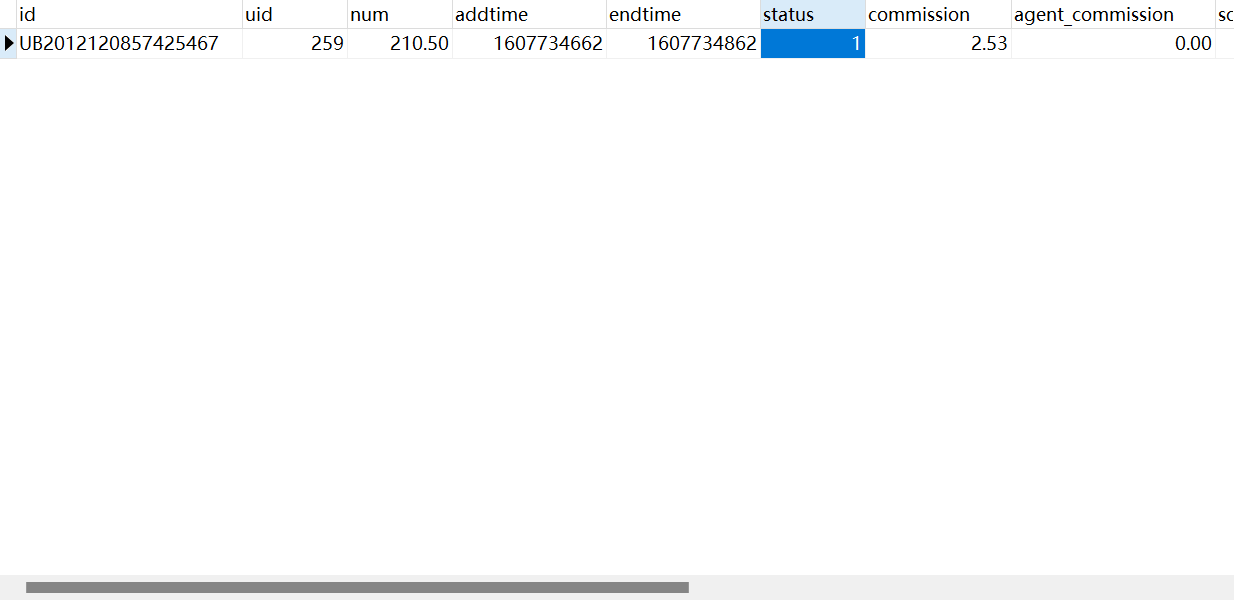
23. 登录Linux服务器涉案网站(mksiaw.com)后台,点击“交易管理”-“订单列表”栏,统计交易状态为“完成付款”的总交易数额为多少元?(标准格式:123.12)
因为有三千多条记录,你不可能一条一条去找,只能找一个符合条件的去数据库反查
status估计就是代表是否完成付款了,结合其他订单确认了这一参数
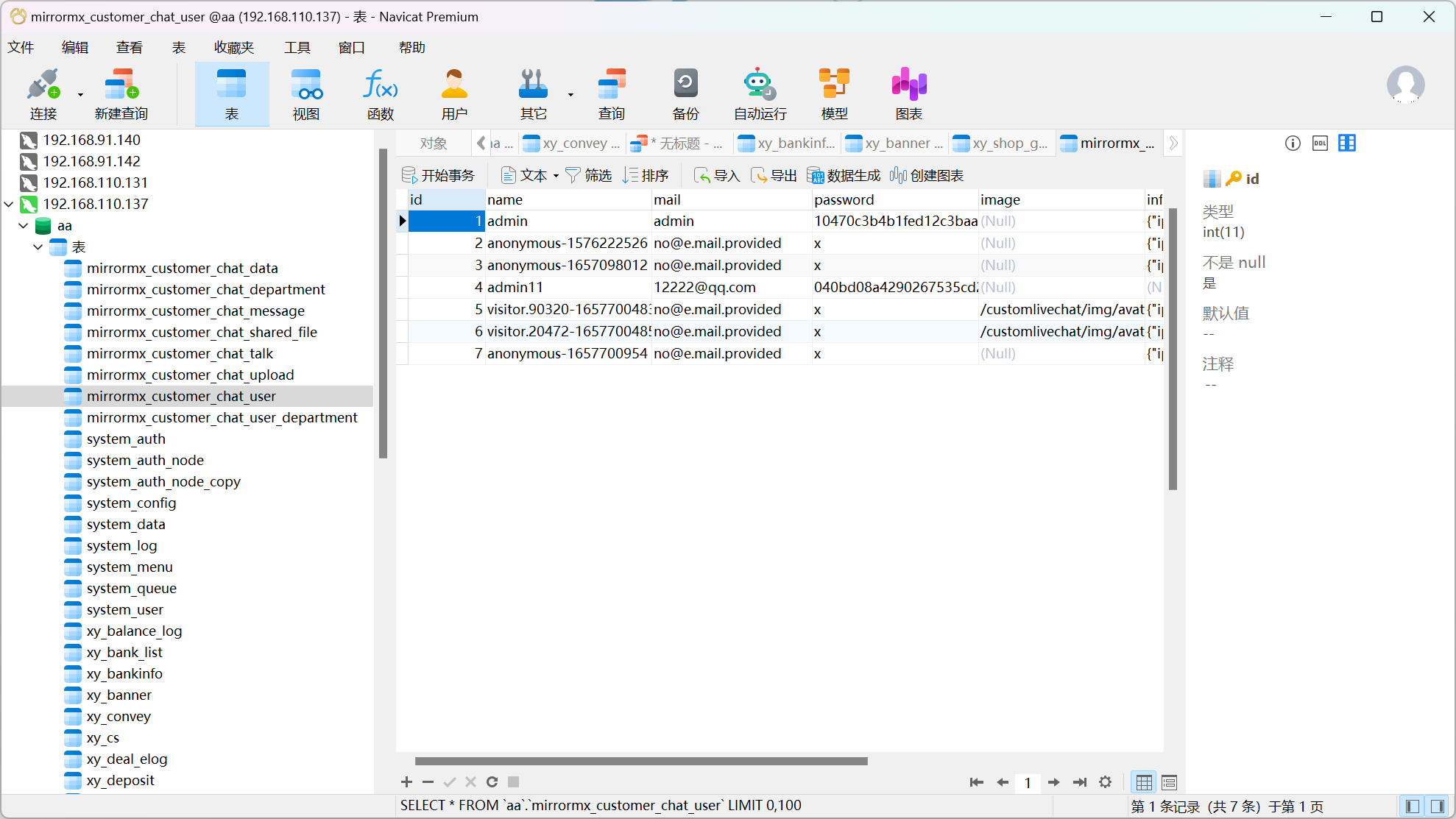
24. 分析Linux服务器的客服网站后台管理员的密码加密方式,使用该加密方式对密码 “ws12”进行加密,得到的结果为?(标准格式:10470c3b4b1fed12c3baac014be15fac67c6e815) 找了一波,没发现在哪里,很继而崩溃
看到一个可疑的,梭进去了
cmd5又秒了
25. 分析Linux服务器客服网站后台管理系统,分析是否存在来自浙江杭州的游客?(标准格式:是或否)
三个都是杭州的