2024年第二届盘古石杯全国电子数据取证大赛技能赛初赛
服务器取证
先对网站进行重构
1 | [root@study ~]# docker ps |
需要绕密,dockerhub找一下dockerfile
1 | # Copyright (c) 2016-present Mattermost, Inc. All Rights Reserved. |
1 | [root@study ~]# docker inspect 64 |
进数据库
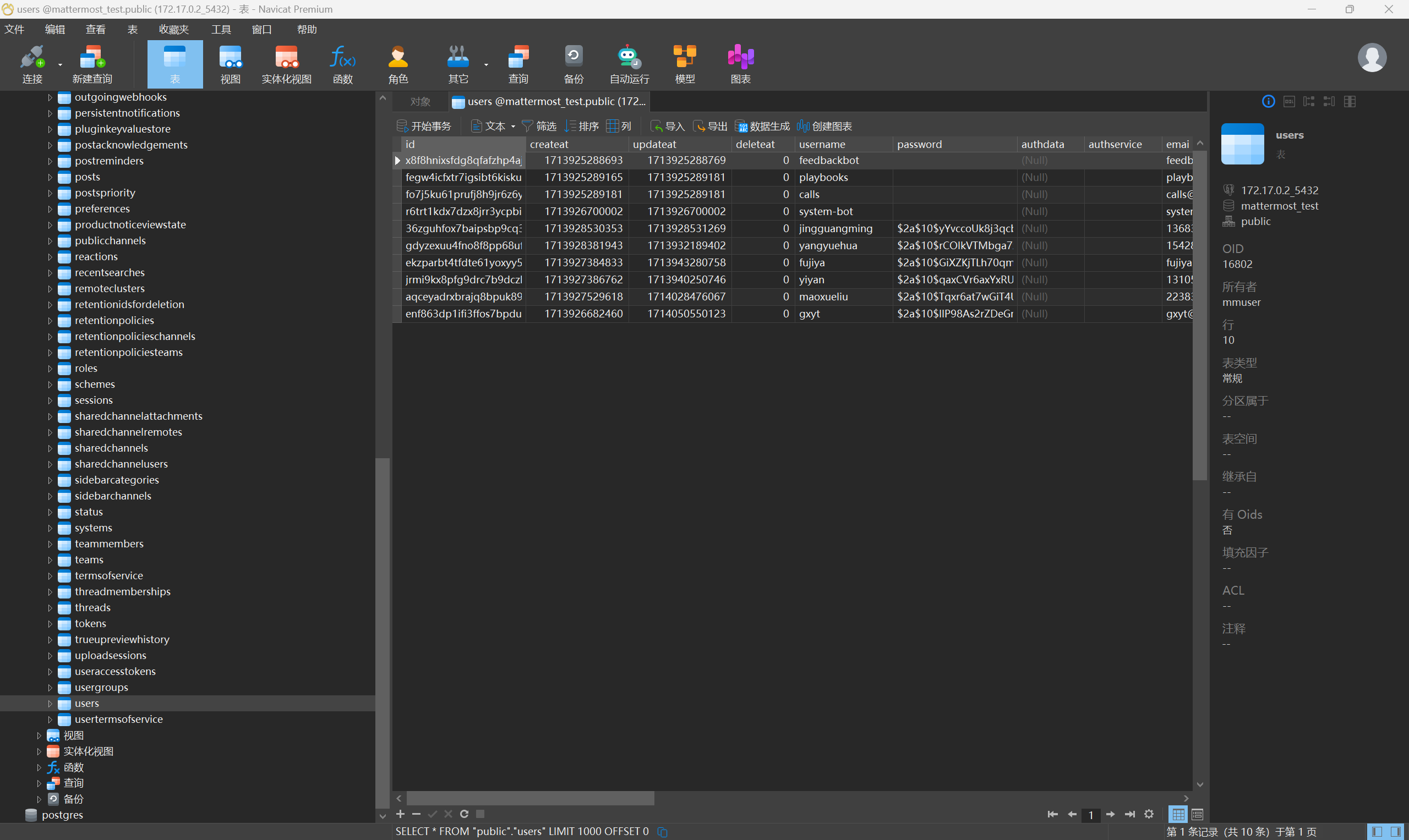
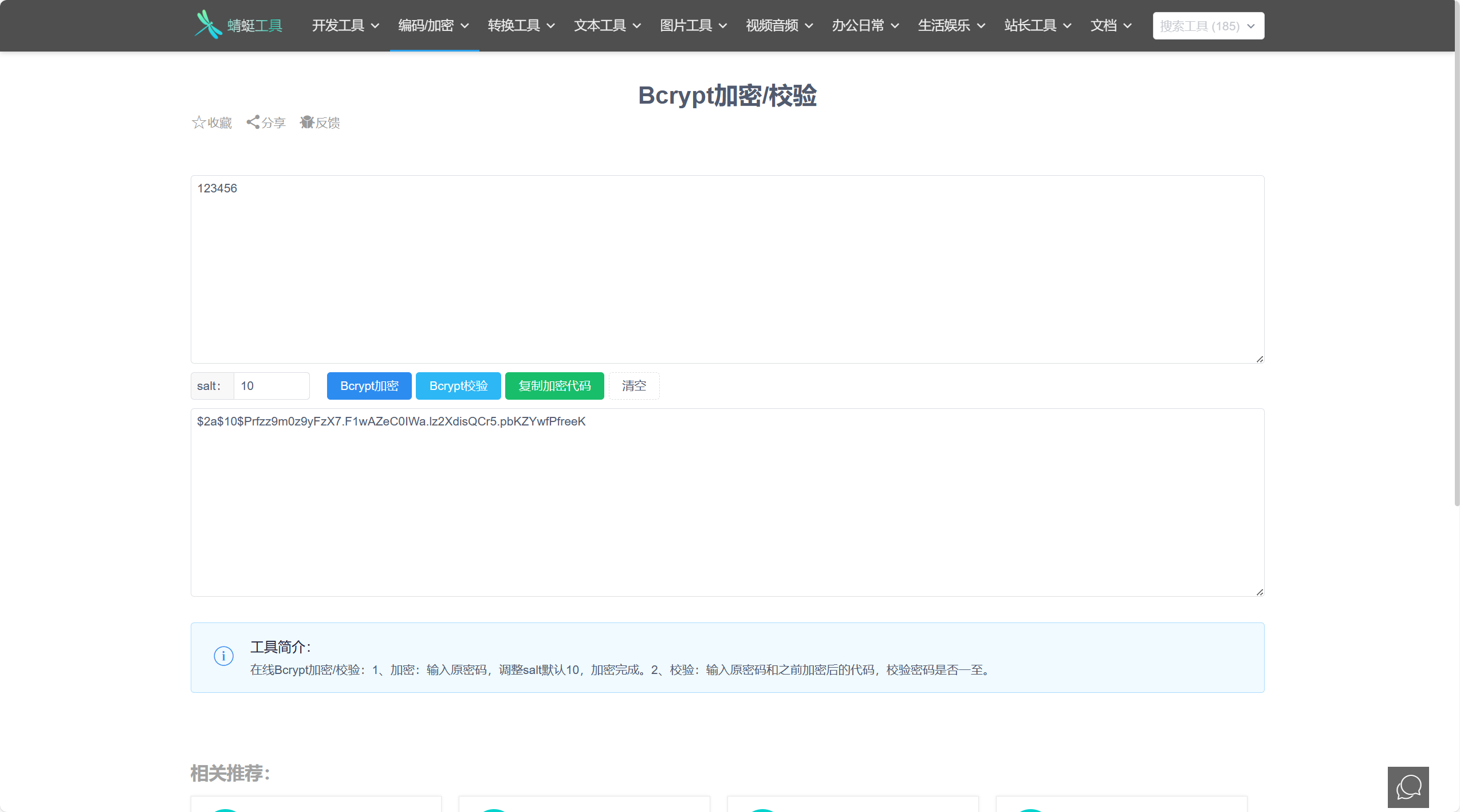
这似曾相识的密码,bcrypt
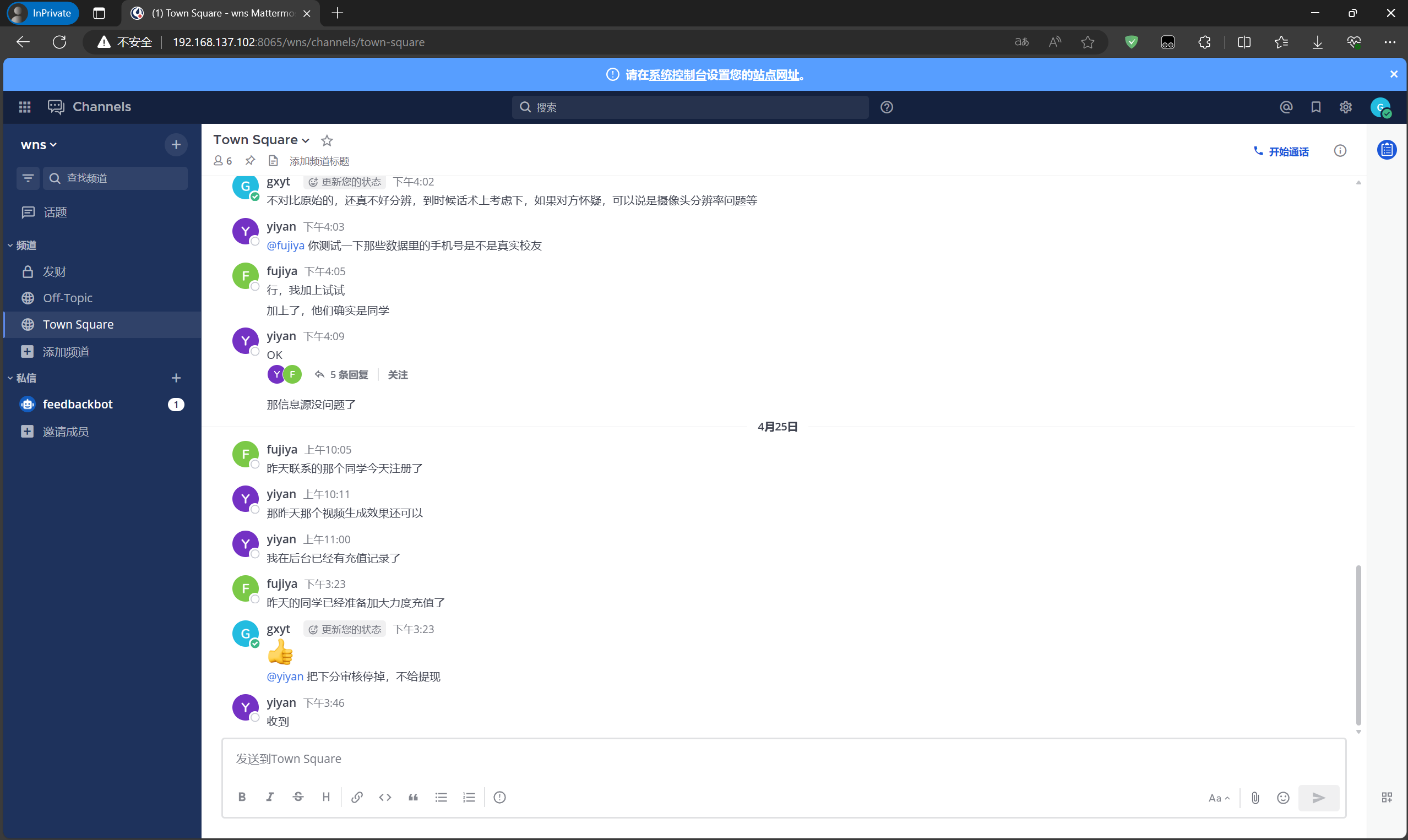
至此IM服务器重构成功,接着重构web服务器
加个hosts直接访问
但是数据库没东西,看后面题目知道做了备份
1 | [root@wns ~]# crontab -l |
/root/backup.sh
1 |
|
稍微修改一下
1 |
|
1 | [root@wns backup]# openssl des3 -d -salt -k "IvPGP/8vfTLtzQfJTmQhYg==" -in 2828.sql.gz -out 2828_decrypted.sql.gz |
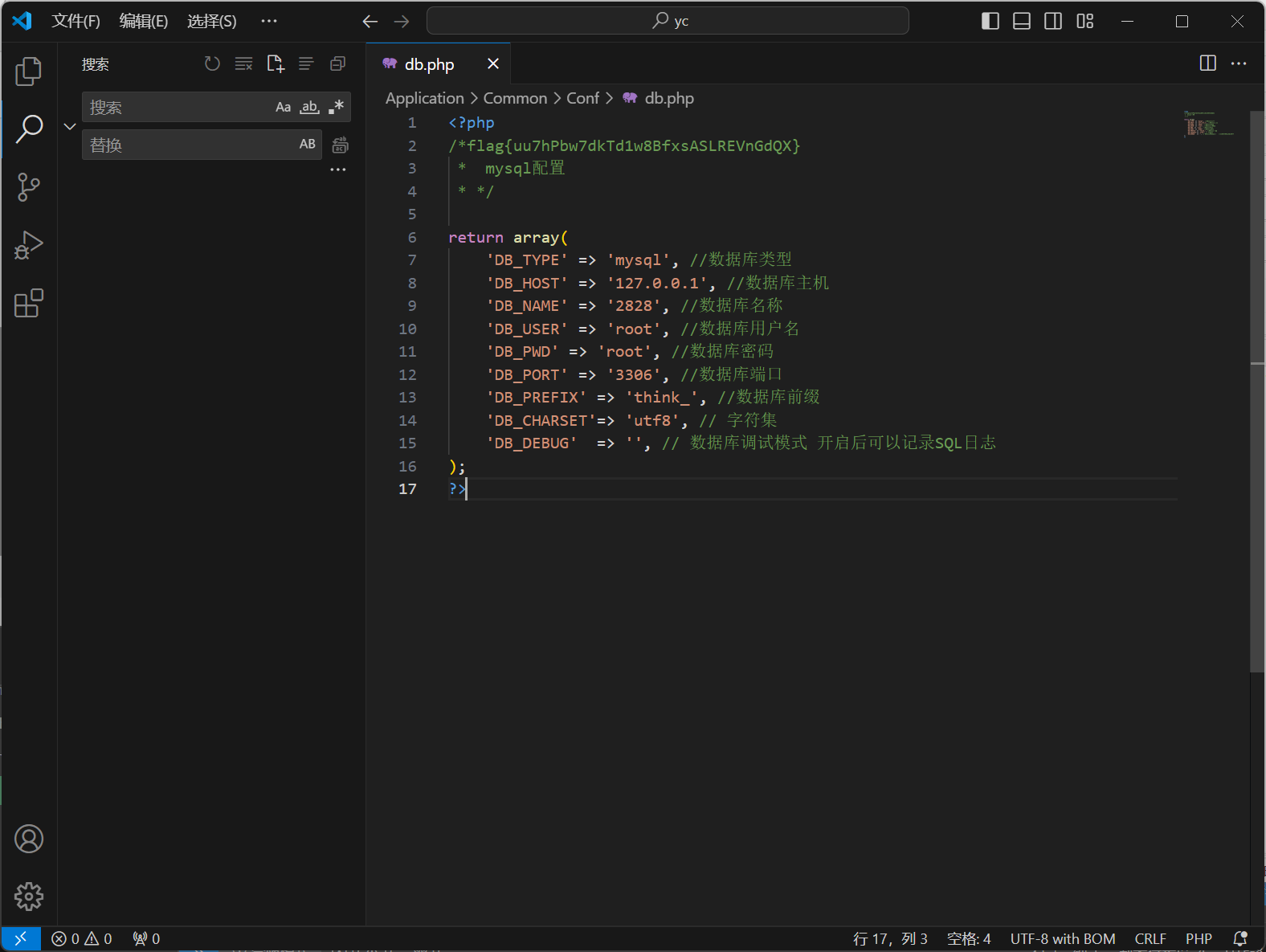
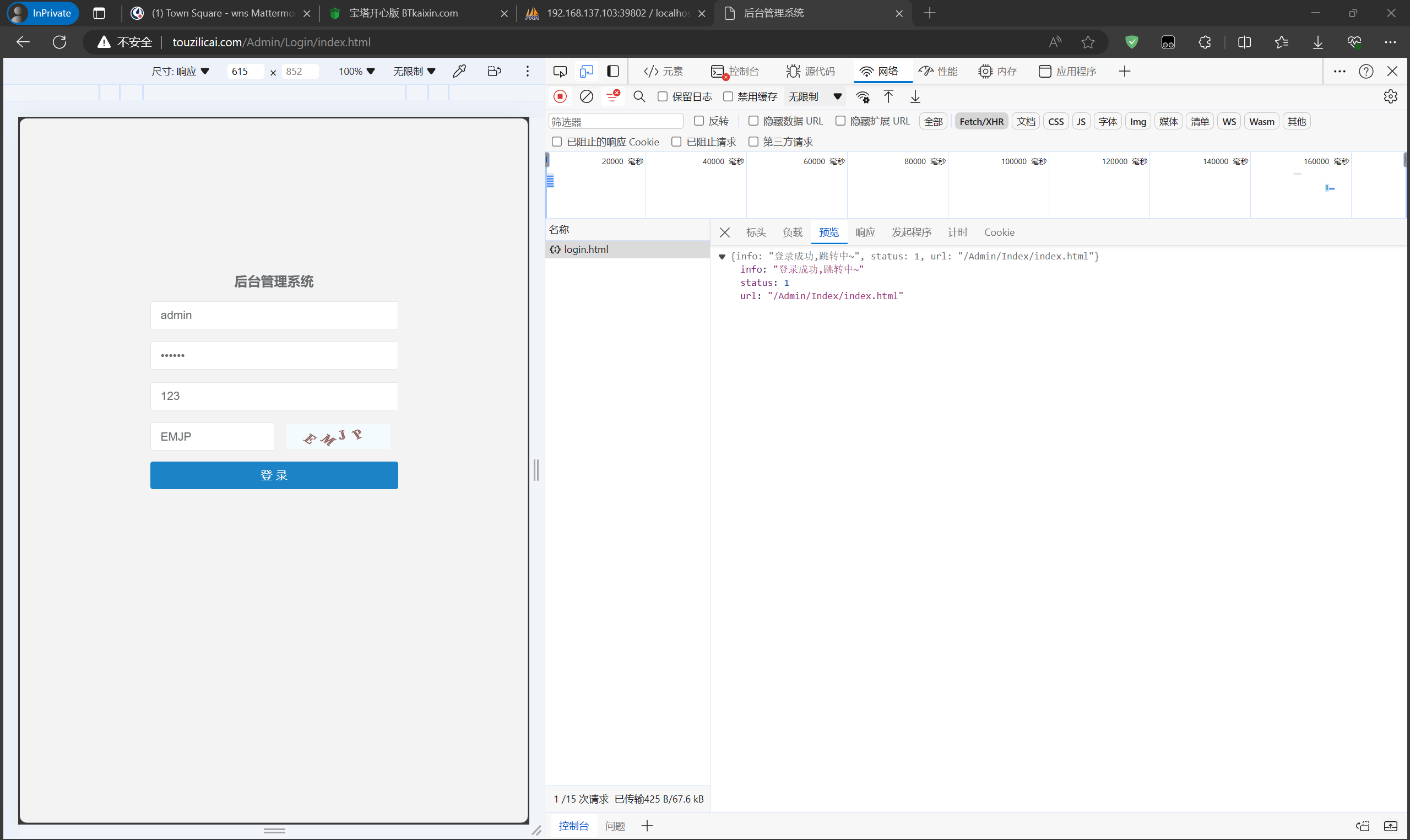
常规后台绕密
自己手动重定向一下
这两个服务器都重构好了
分析内部IM服务器检材,在搭建的内部即时通讯平台中,客户端与服务器的通讯端口是:[答案格式:8888][★☆☆☆☆]
1 | [root@study ~]# docker inspect 643626ab3d8b | grep -i port |
分析内部IM服务器检材,该内部IM平台使用的数据库版本是: [答案格式:12.34][★★☆☆☆]
1 | [root@study ~]# docker inspect 643626ab3d8b | grep -i version |
分析内部IM服务器检材,该内部IM平台中数据库的名称是:[答案格式:小写][★★☆☆☆]
1 | [root@study ~]# docker inspect 643626ab3d8b | grep -i db |
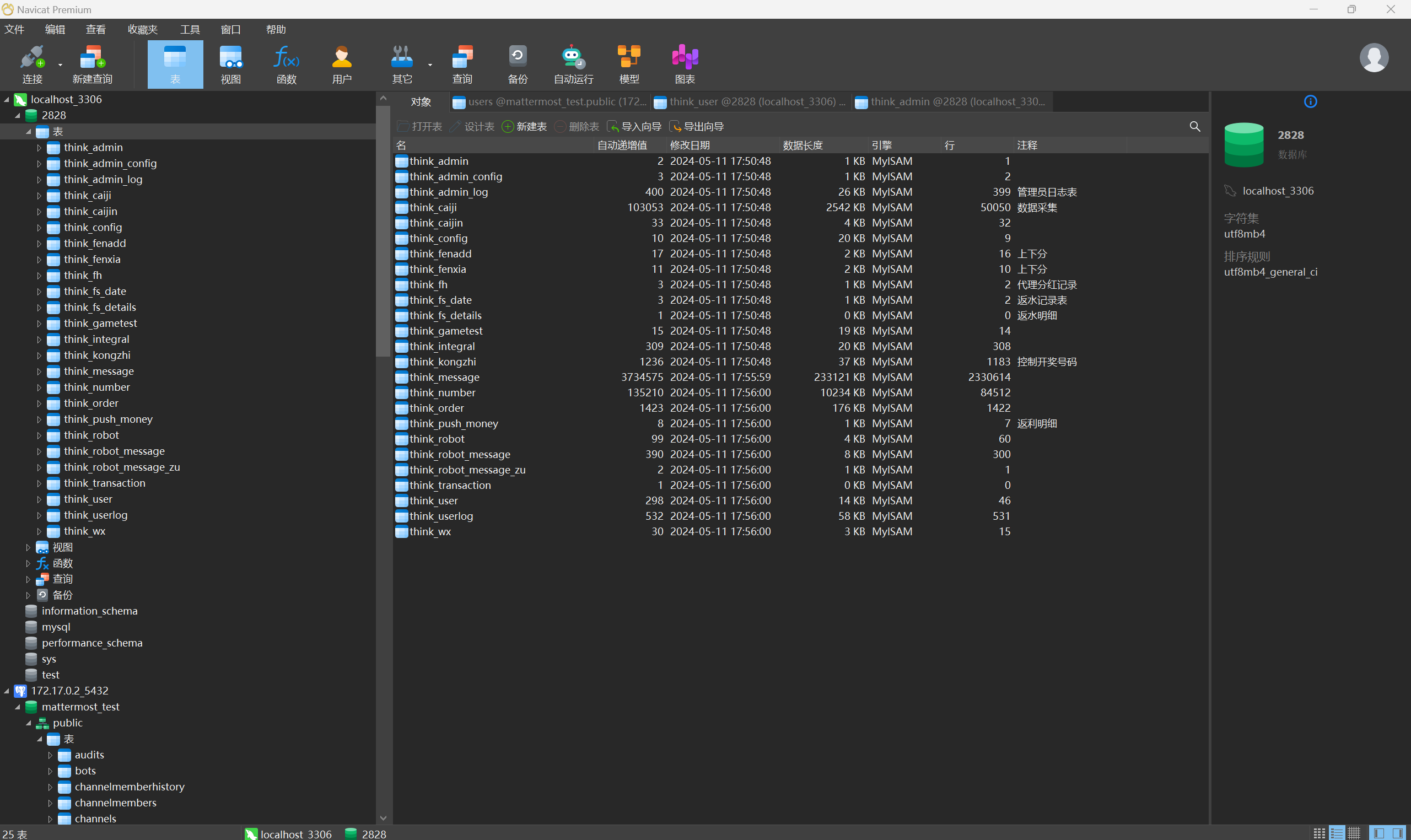
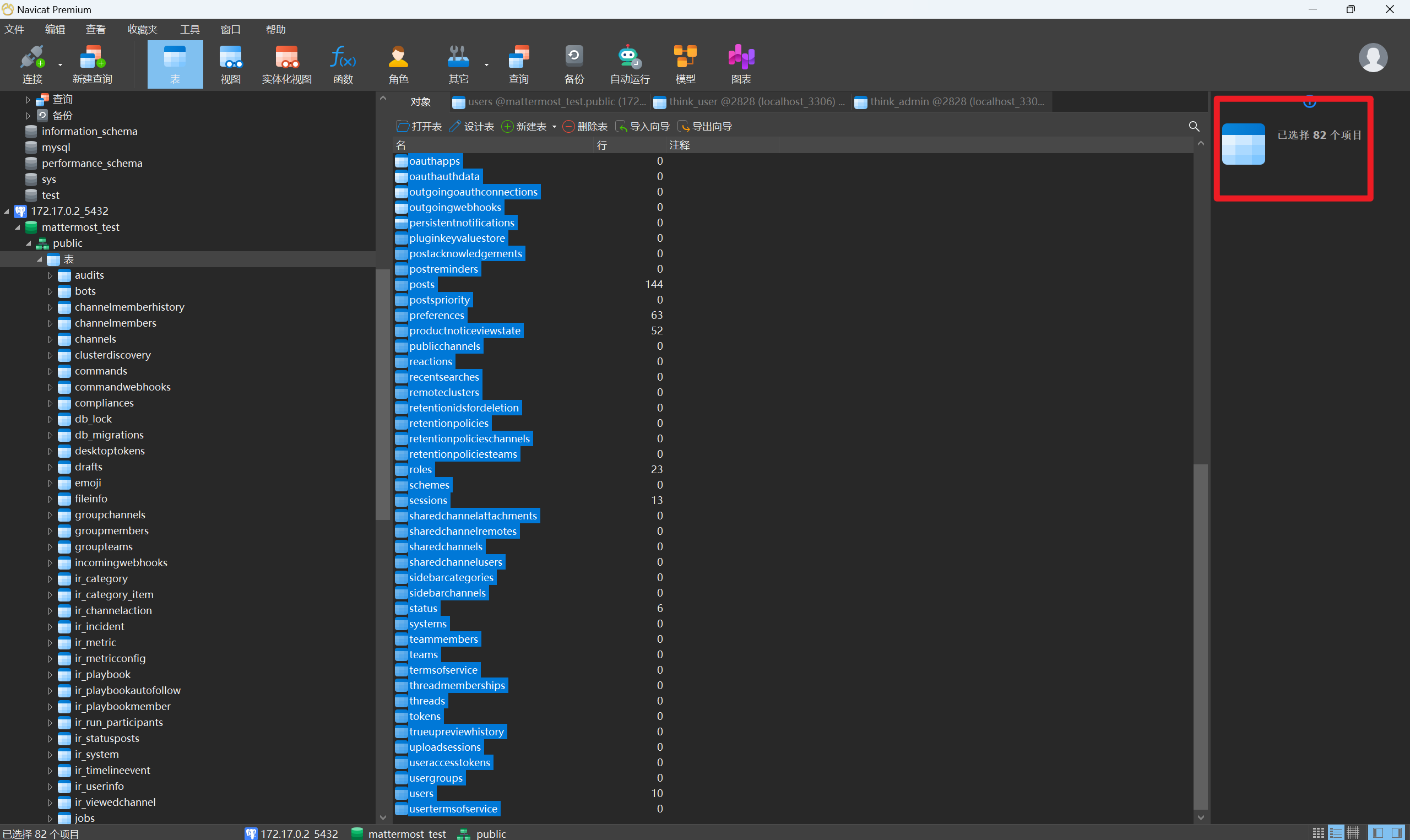
分析内部IM服务器检材,该内部IM平台中当前数据库一共有多少张表:[答案格式:1][★★☆☆☆]
分析内部IM服务器检材,员工注册的邀请链接中,邀请码是:[答案格式:小写数字字母][★★★☆☆]
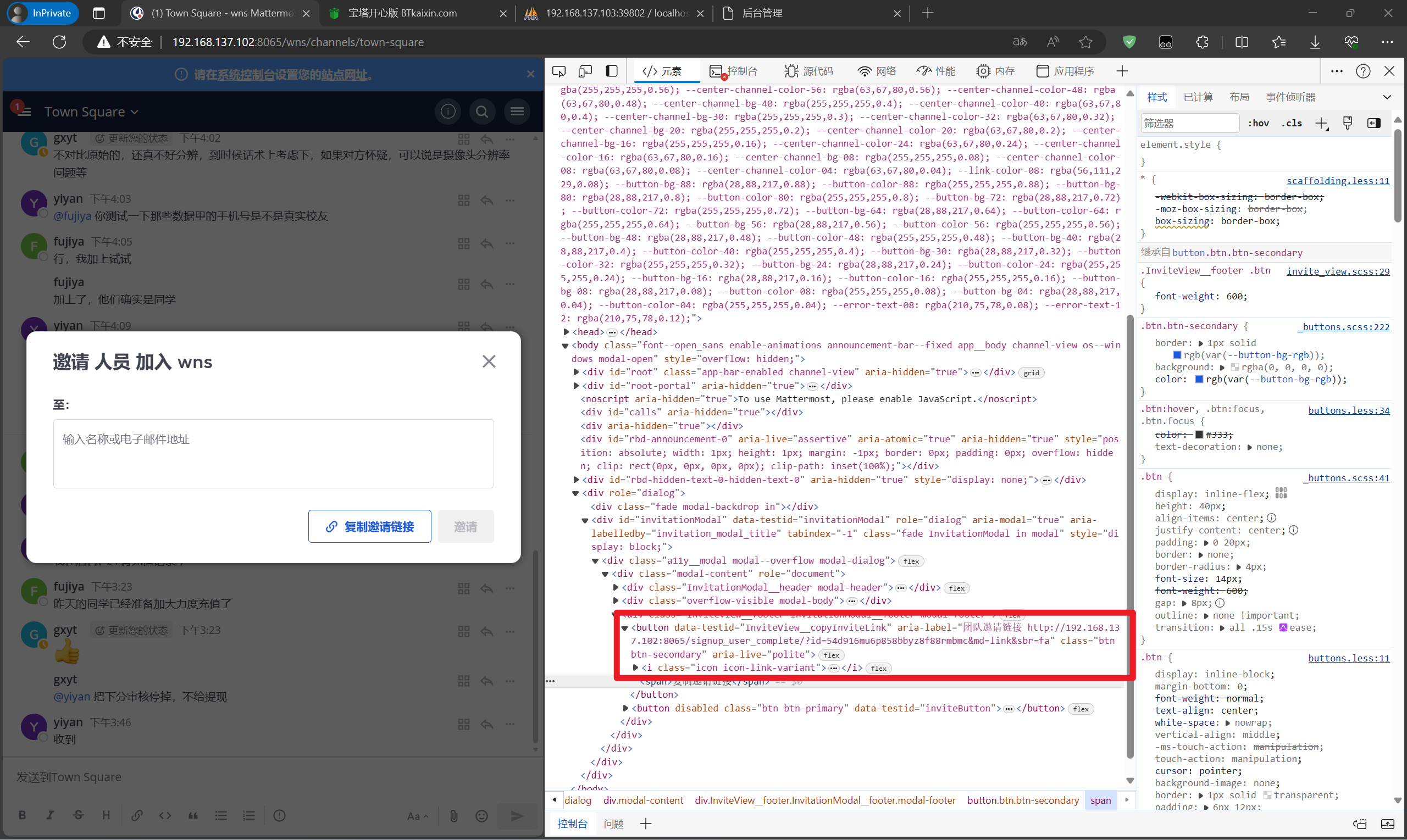
分析内部IM服务器检材,用户yiyan一共给fujiya发送了几个视频文件:[答案格式:数字][★★★☆☆]
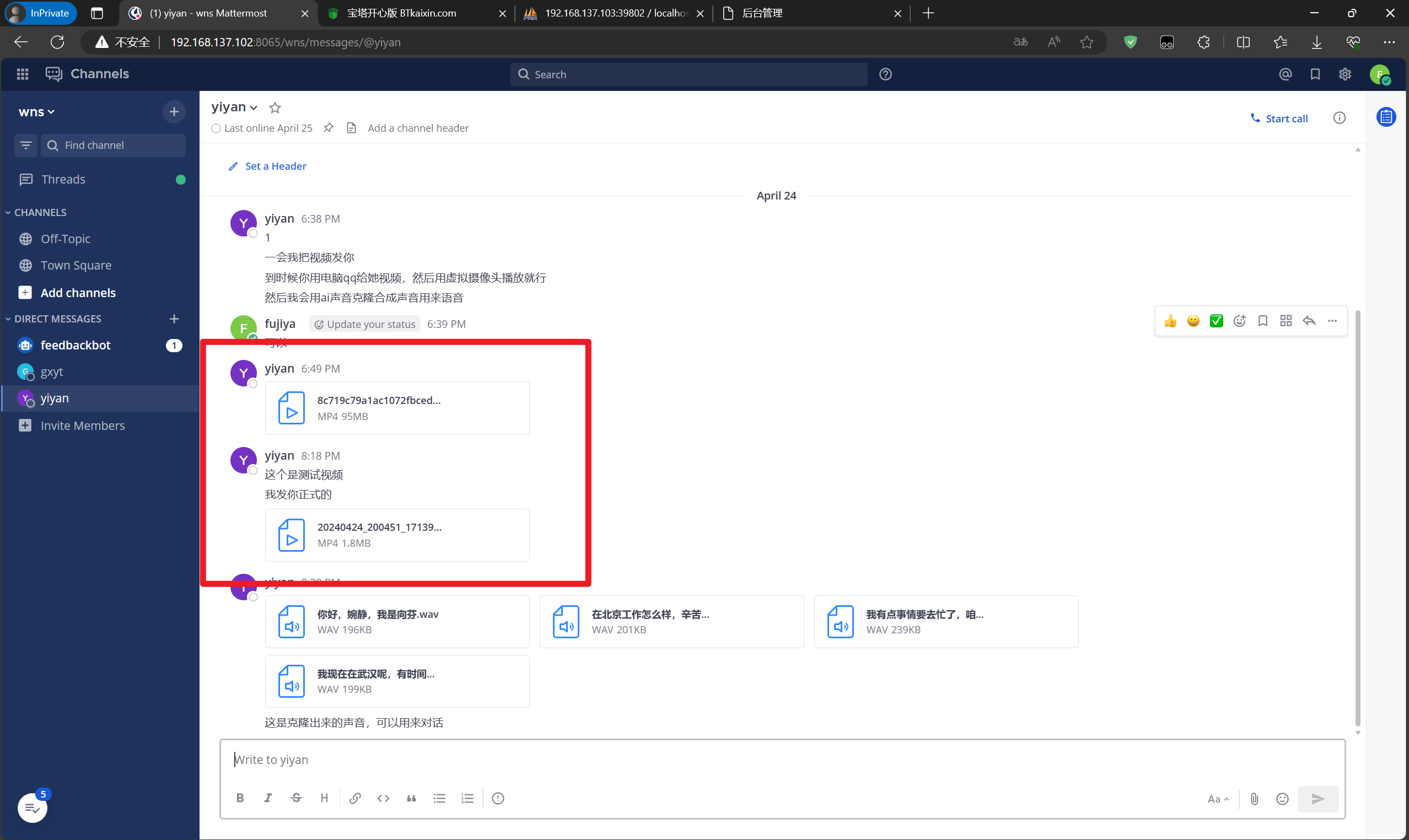
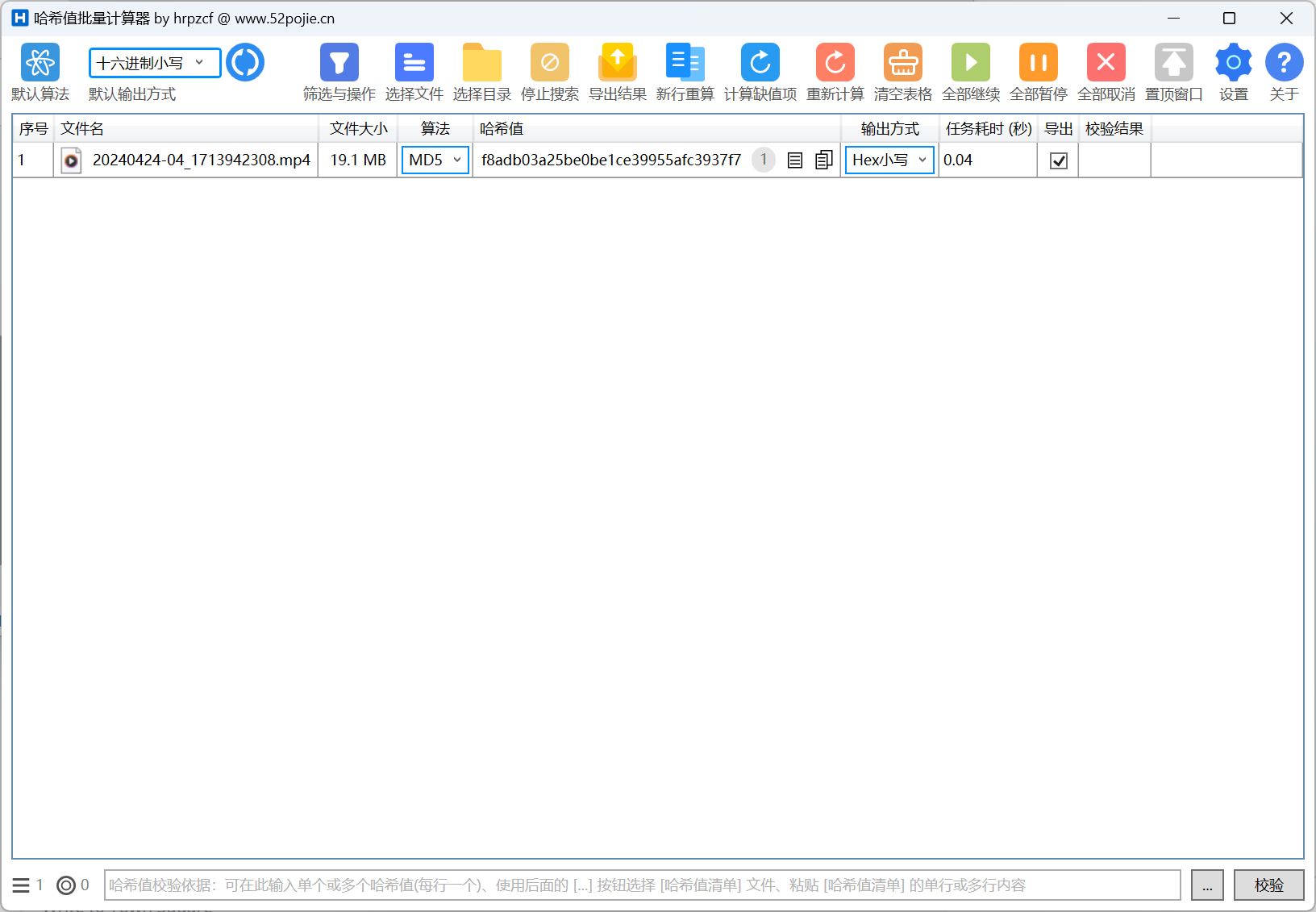
分析内部IM服务器检材,用户yiyan在团队群组中发送的视频文件的MD5值是:[答案格式:小写][★★★☆☆]
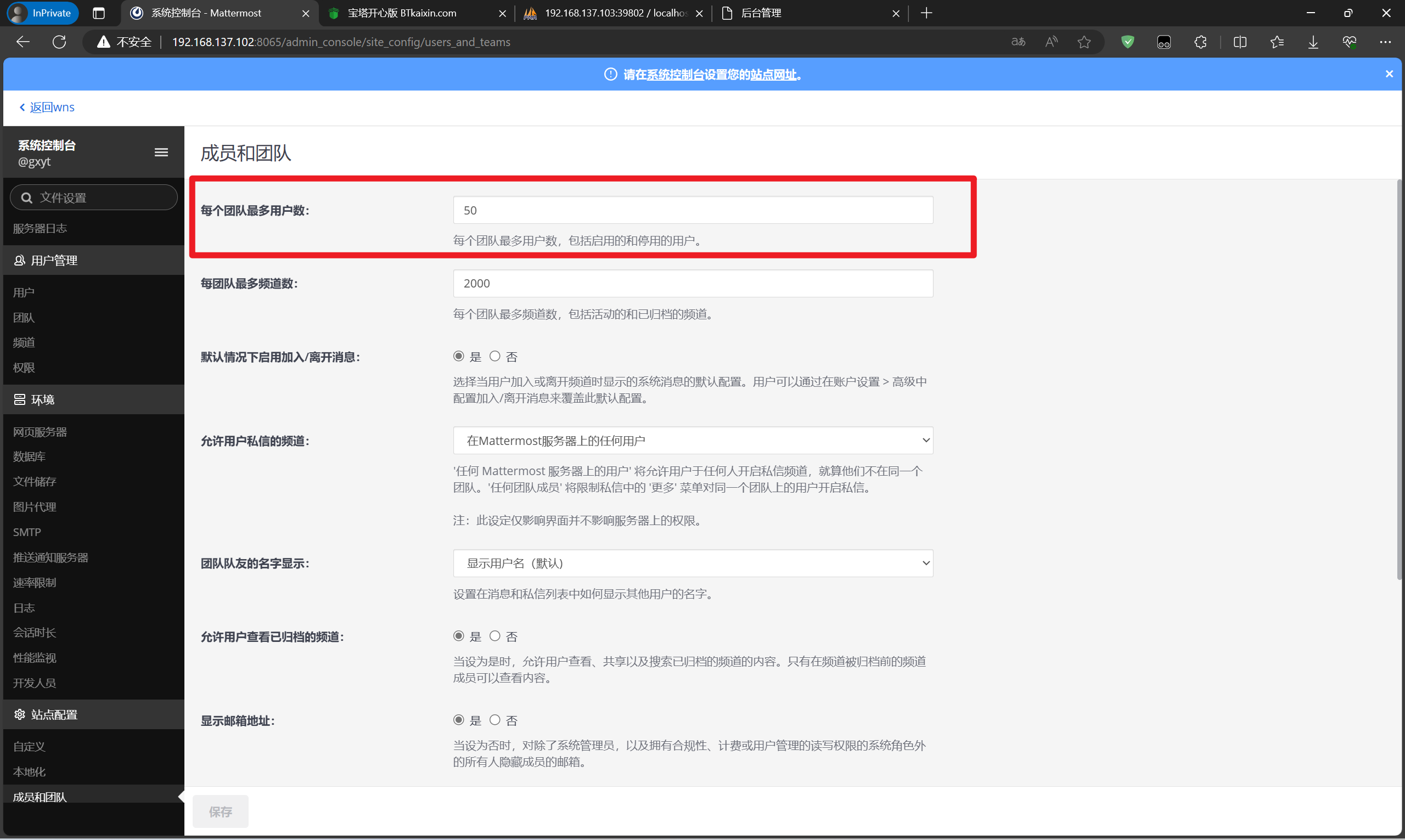
分析内部IM服务器检材,一个团队中允许的最大用户数是:[答案格式:数字][★★★★☆]
分析内部IM服务器检材,黑客是什么时候开始攻击:[答案格式:2024-01-01-04-05][★★★☆☆]
分析网站服务器检材,网站搭建使用的服务器管理软件当前版本是否支持32位系统:[答案格式:是/否][★☆☆☆☆]
1 | [root@wns ~]# cat install.sh | grep 32位 |
分析网站服务器检材,数据库备份的频率是一周多少次:[答案格式:1][★★☆☆☆]
1 | [root@wns ~]# crontab -l |
分析网站服务器检材,数据库备份生成的文件的密码是:[答案格式:admin][★★☆☆☆]
1 | [root@wns ~]# sh backup.sh |
分析网站服务器检材,网站前台首页的网站标题是:[答案格式:百度][★★★☆☆]
分析网站服务器检材,受害人第一次成功登录网站的时间是:[答案格式:2024-01-01-04-05][★★★☆☆]
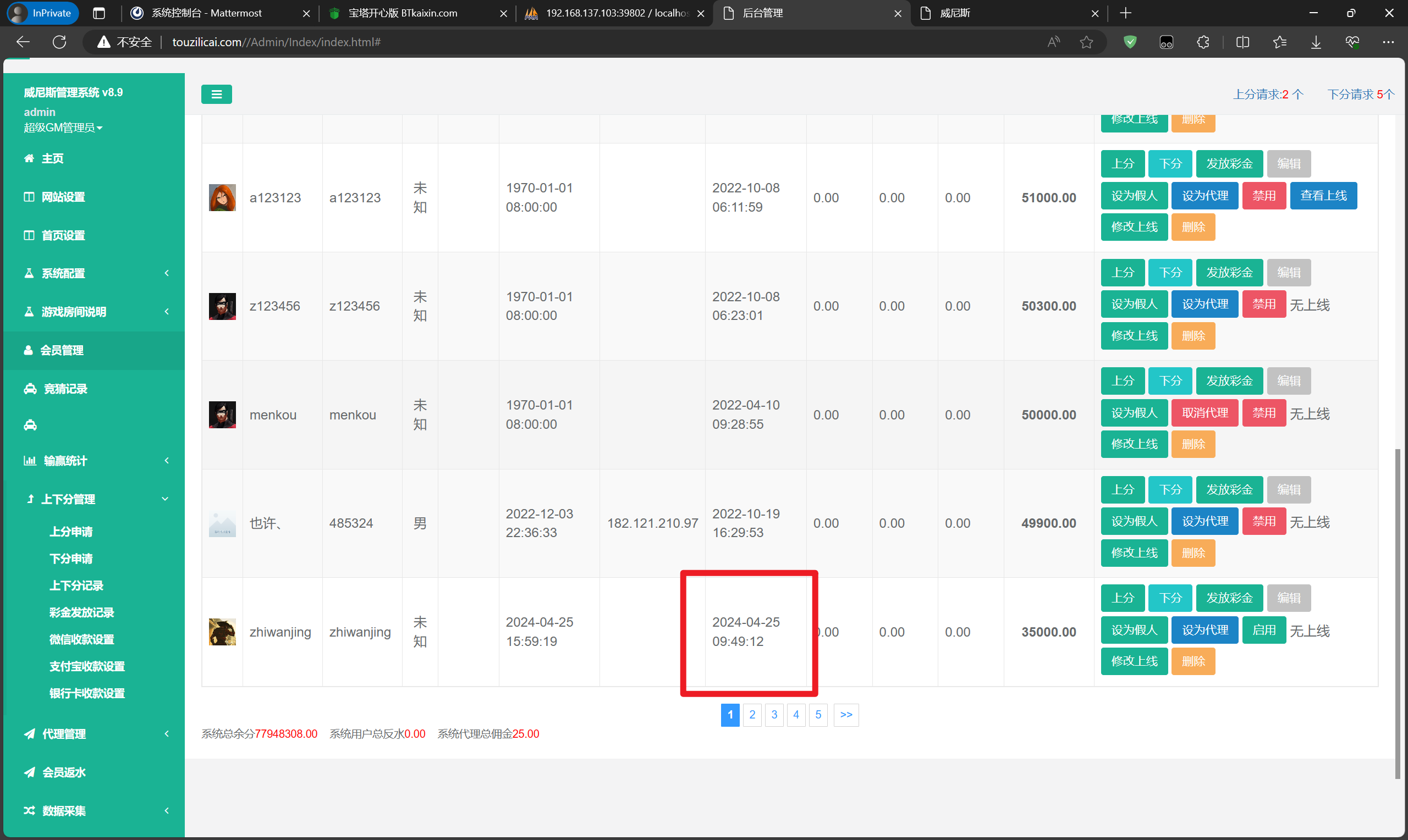
分析网站服务器检材,前台页面中,港澳数字竞猜游戏中,进入贵宾厅最低点数是:[答案格式:1234][★★★☆☆]
找个用户,密码哈希替换一下
分析网站服务器检材,受害人在平台一共盈利了多少钱:[答案格式:12][★★☆☆☆]
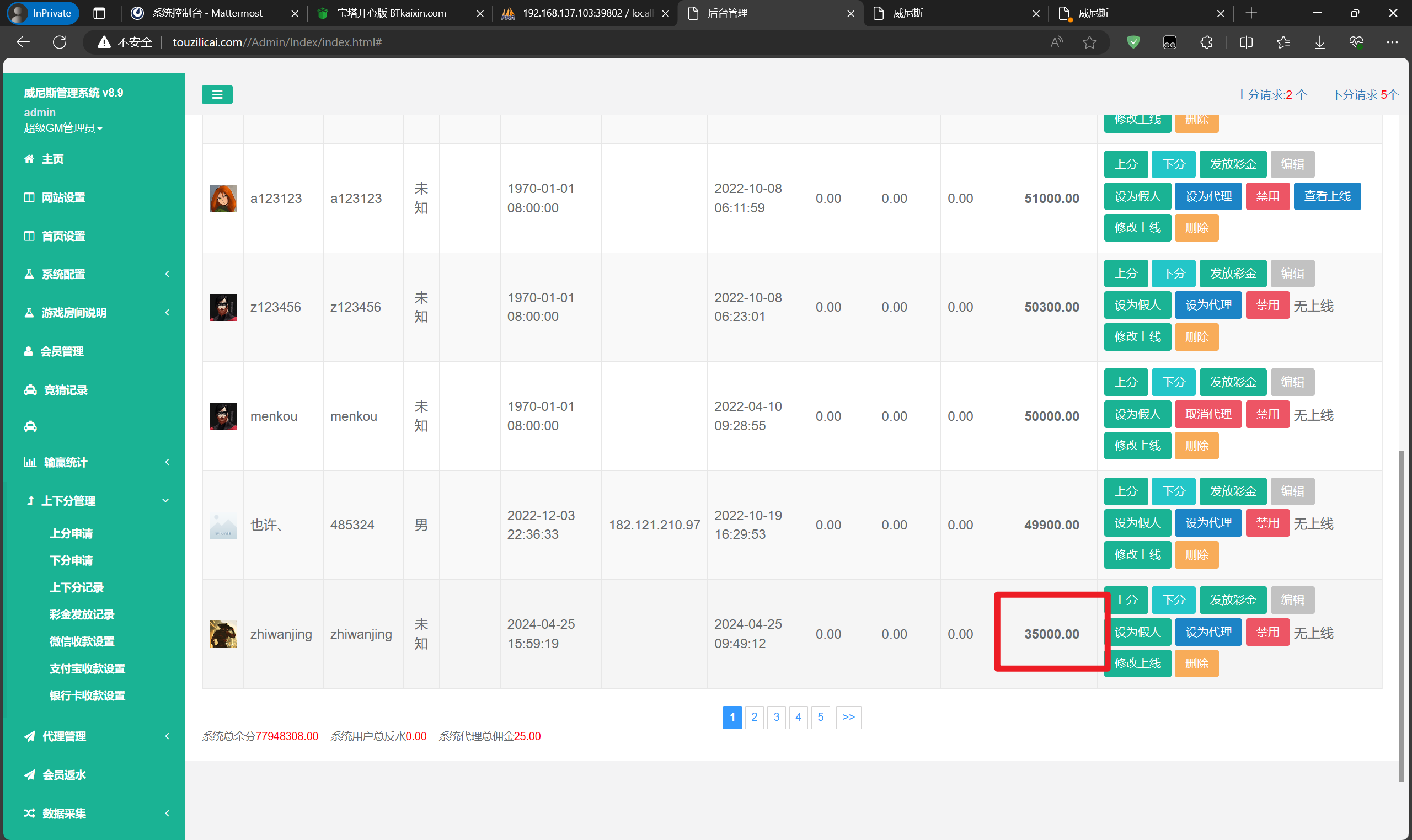
分析网站服务器检材,网站根目录下,哪个路径存在漏洞:[答案格式:/Admin/User/register.php][★★★☆☆]
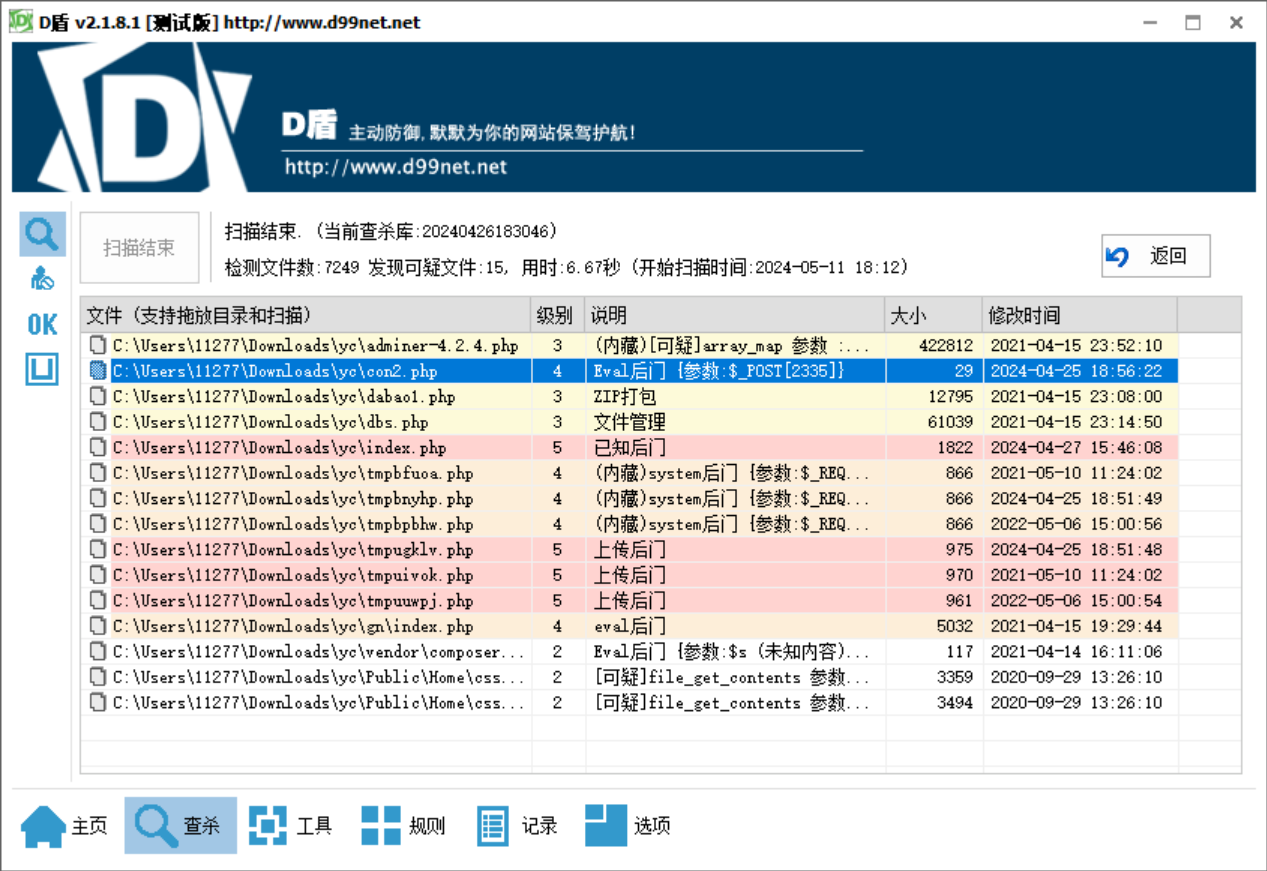
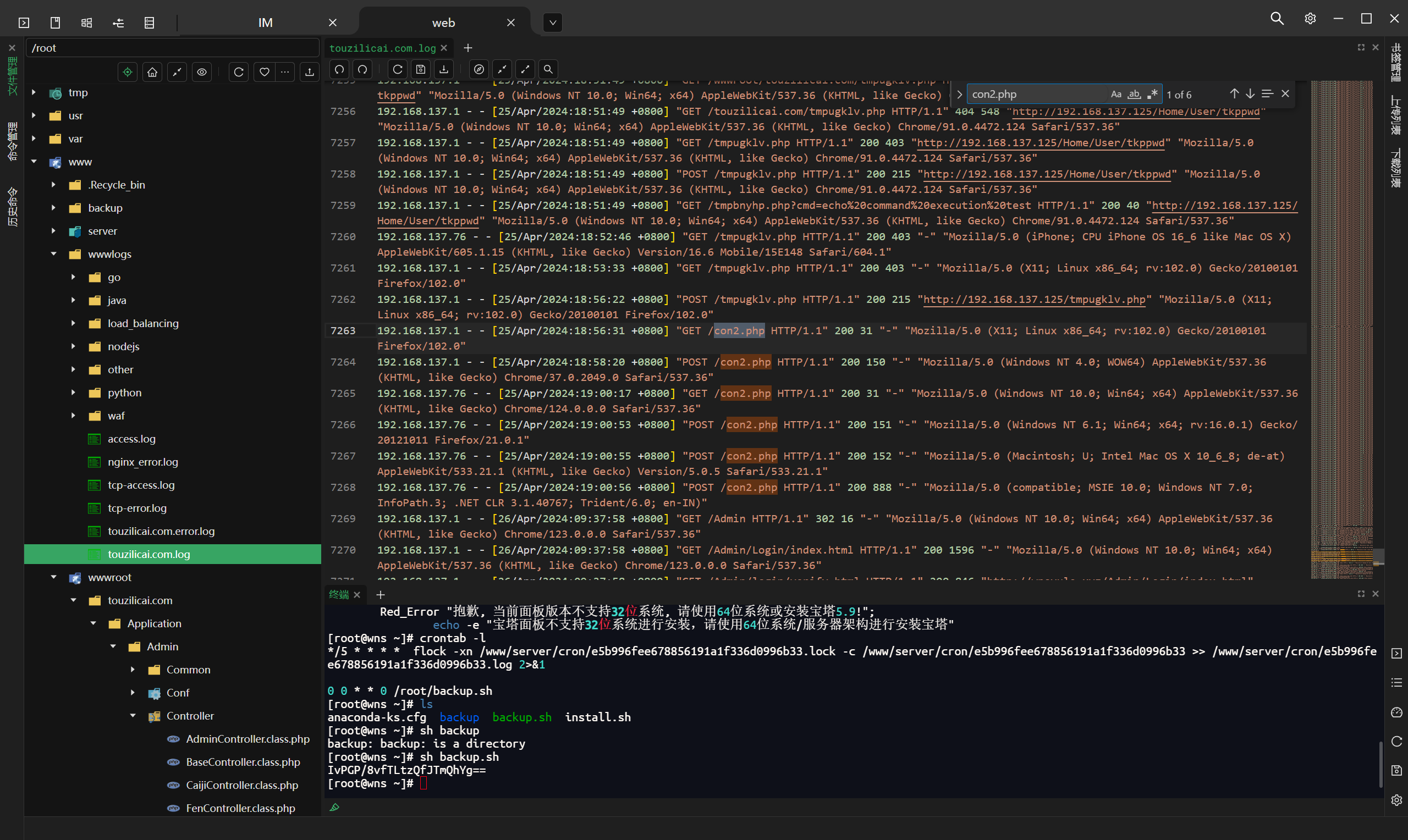
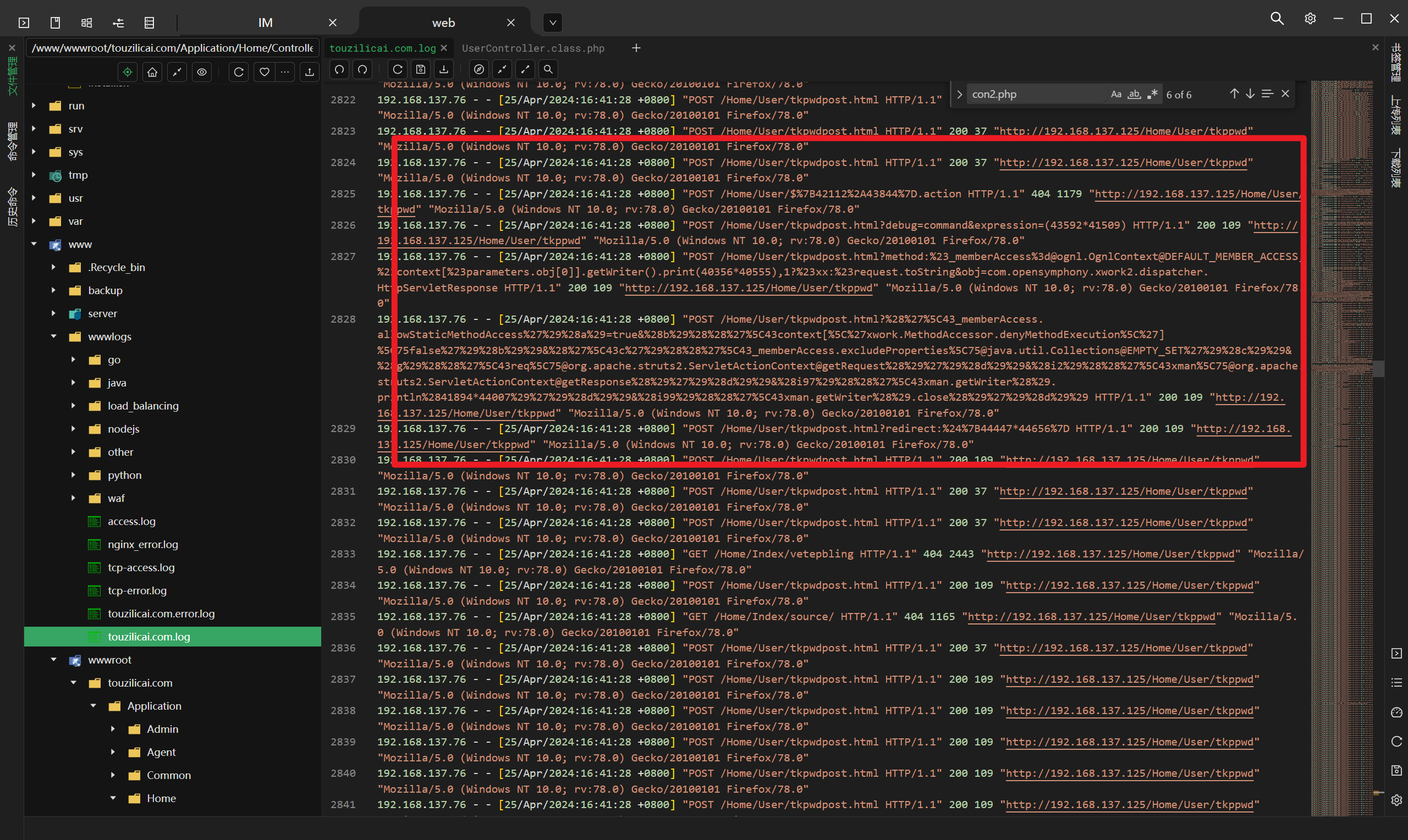
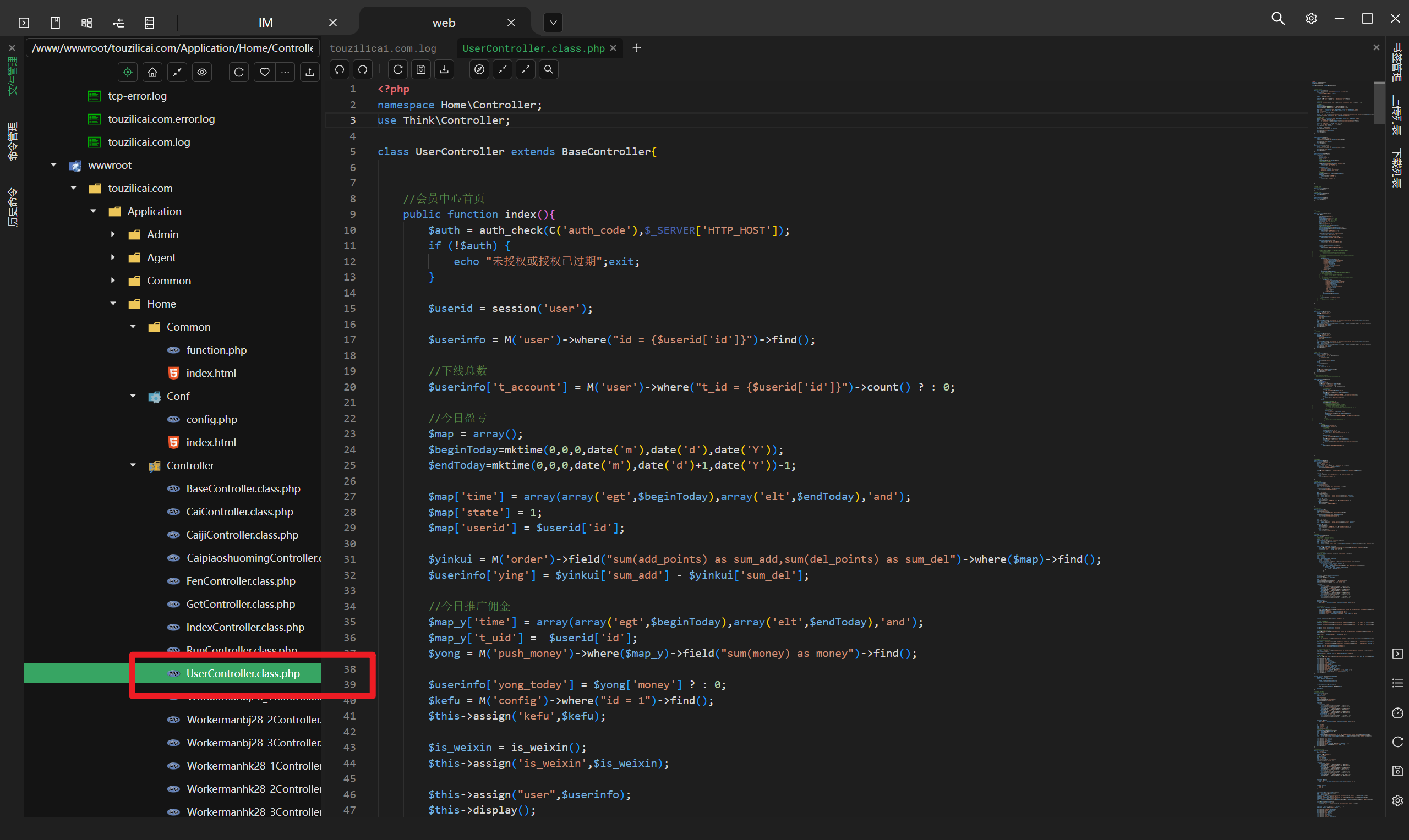
分析网站服务器检材,黑客通过哪个文件上传的木马文件:[答案格式:test.php][★☆☆☆☆]
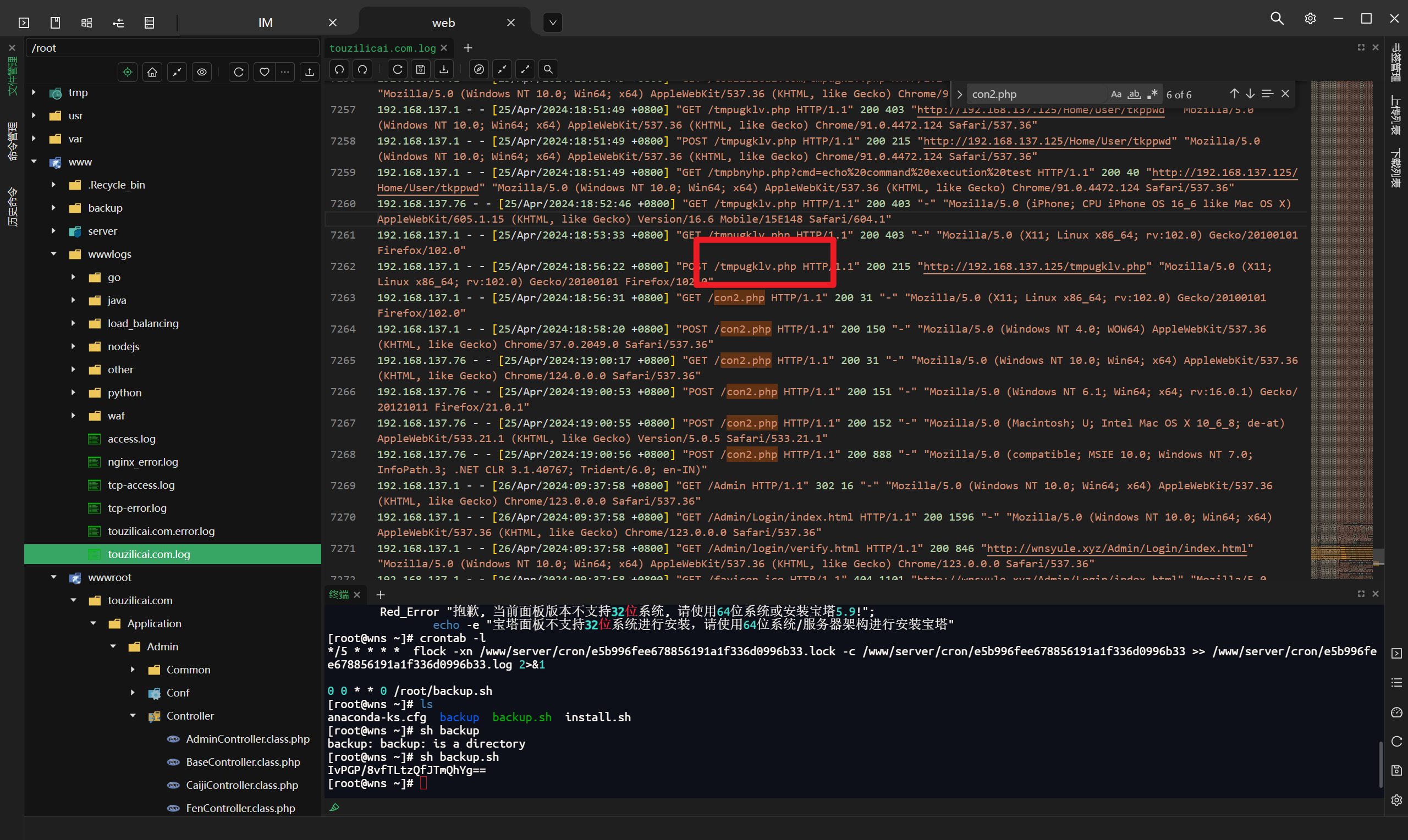
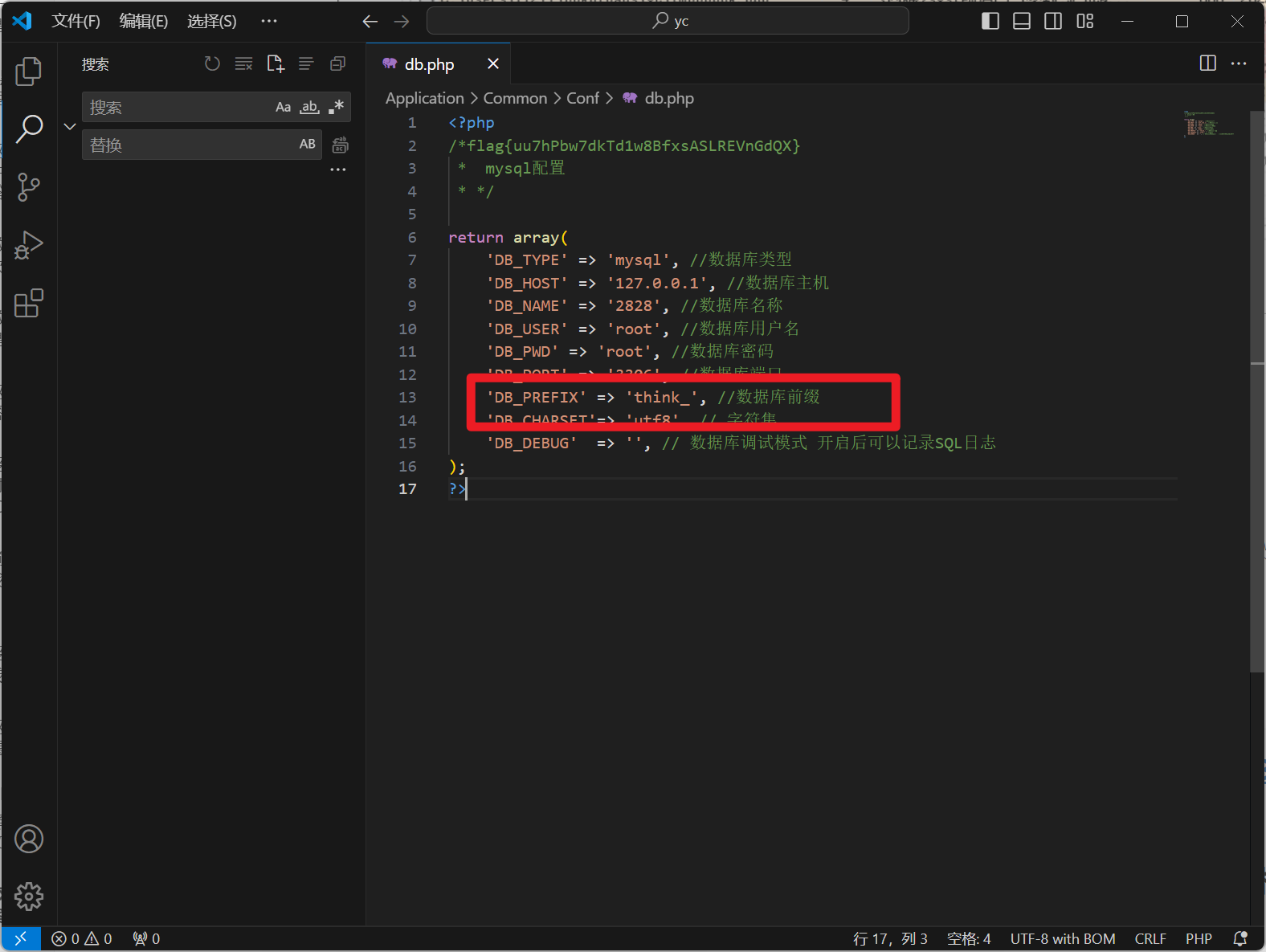
分析网站服务器检材,网站使用的数据库前缀是:[答案格式:test_][★☆☆☆☆]
分析网站服务器检材,木马文件的密码是:[答案格式:123] [★☆☆☆☆]
d盾那里有
人工智能取证
本系列题需要bitlocker解开后才能作答
GPT-SoVITS整合包部署及使用教程 - 哔哩哔哩 (bilibili.com)
拿到后粗略看一眼,GPT是换声音的,Rope是换脸的,里面还有个secret是一个爆炸策划


软件里面有个encrypt.exe加密后的文件后面会带-cn

分析义言的计算机检材,一共训练了多少个声音模型:[答案格式:123][★★☆☆☆]

每一个点进去都是由train.log的

分析义言的计算机检材,声音模型voice2,一共训练了多少条声音素材:[答案格式:123][★★☆☆☆]
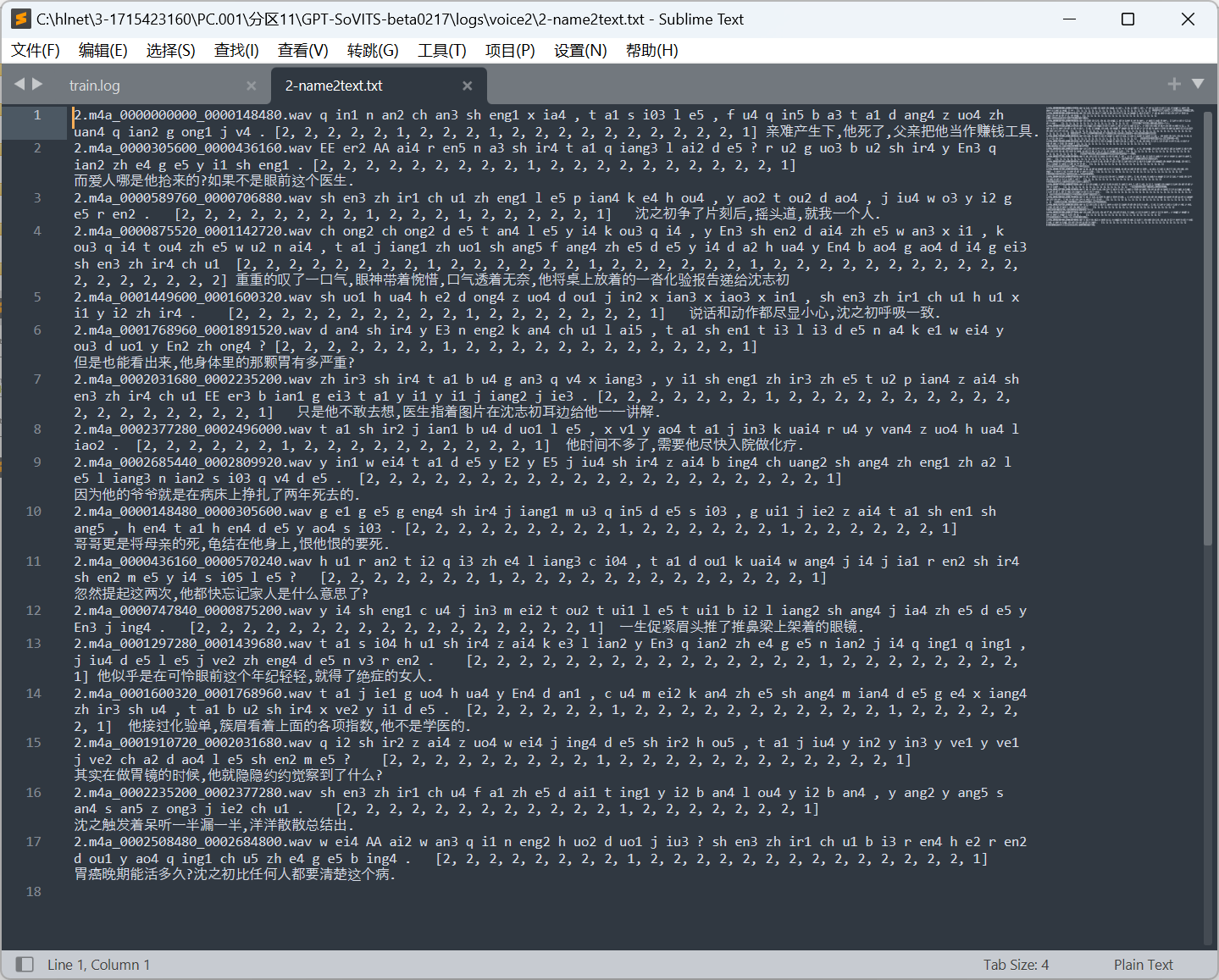
分析义言的计算机检材,声音模型voice3,一共训练了多少轮:[答案格式:123][★★★☆☆]
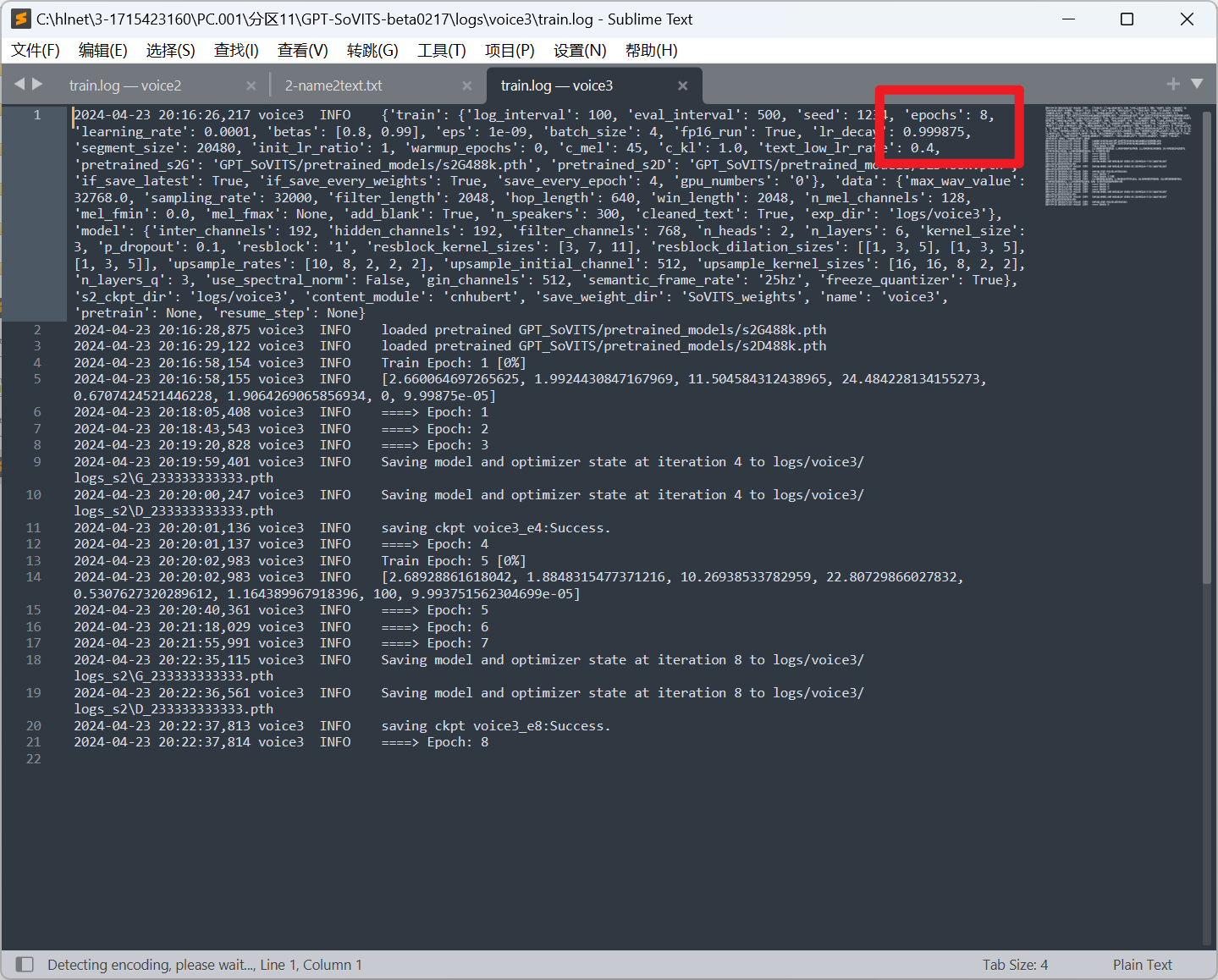
分析义言的计算机检材,声音克隆工具推理生成语音界面的监听端口是:[答案格式:1234][★★★★☆]
分析义言的计算机检材,电脑中视频文件有几个被换过脸:[答案格式:10][★★★★★]
分析义言的计算机检材,换脸AI程序默认换脸视频文件名是:[答案格式:test.mp4][★★☆☆☆]
分析义言的计算机检材,换脸AI程序默认换脸图片的文件名称:[答案格式:abc.abc][★★☆☆☆]
分析义言的计算机检材,换脸AI程序模型文件数量是多少个:[答案格式:10][★★☆☆☆]
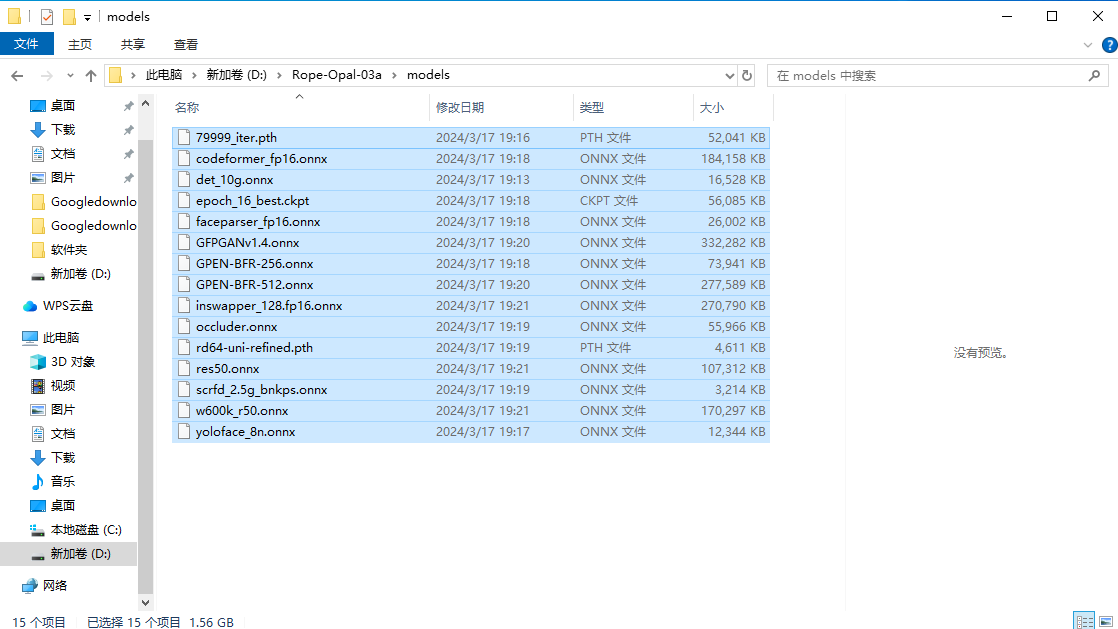
计算机取证
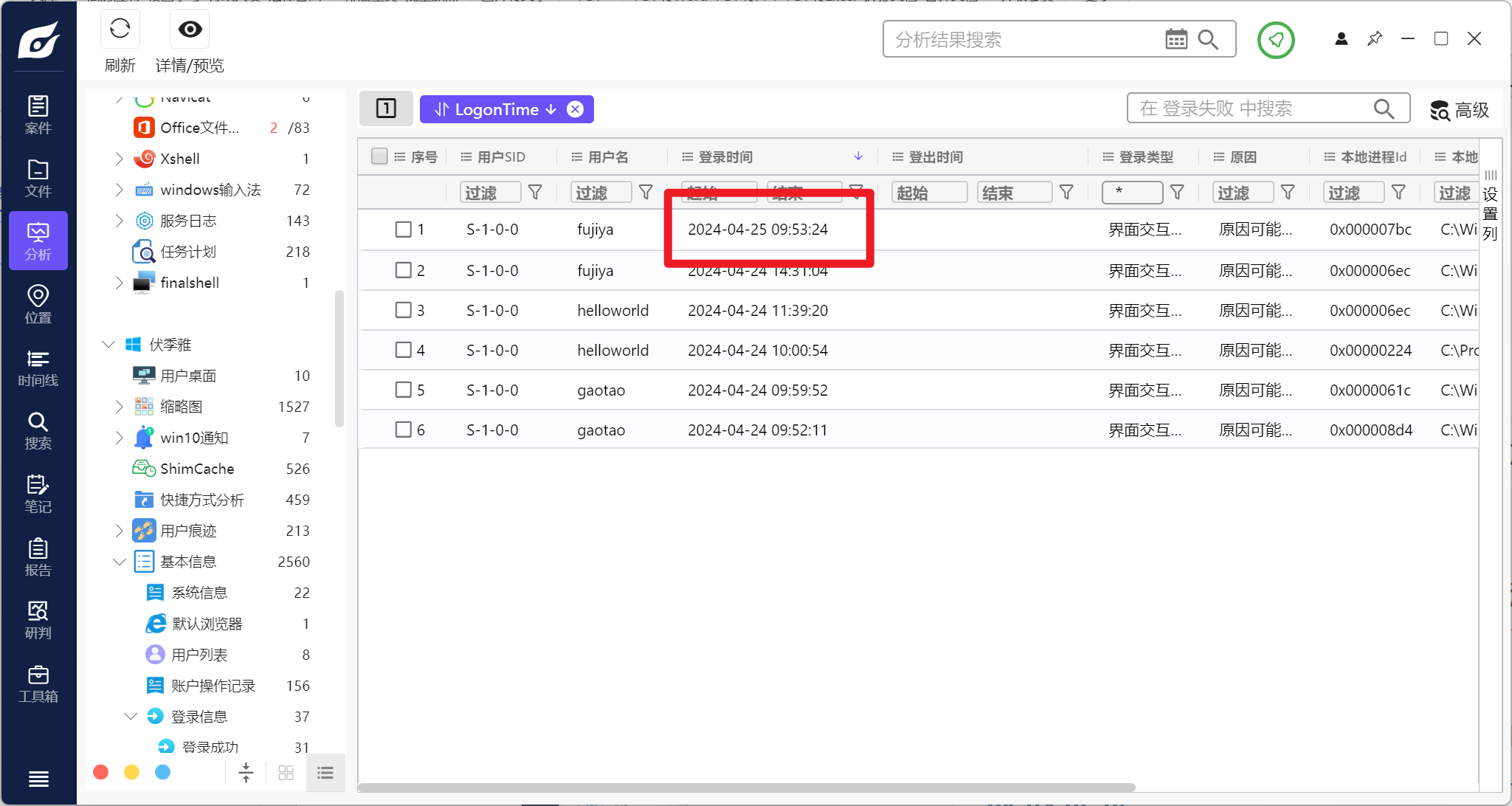
分析伏季雅的计算机检材,计算机最后一次错误登录时间是:[答案格式:2024-01-01-04-05-06][★☆☆☆☆]
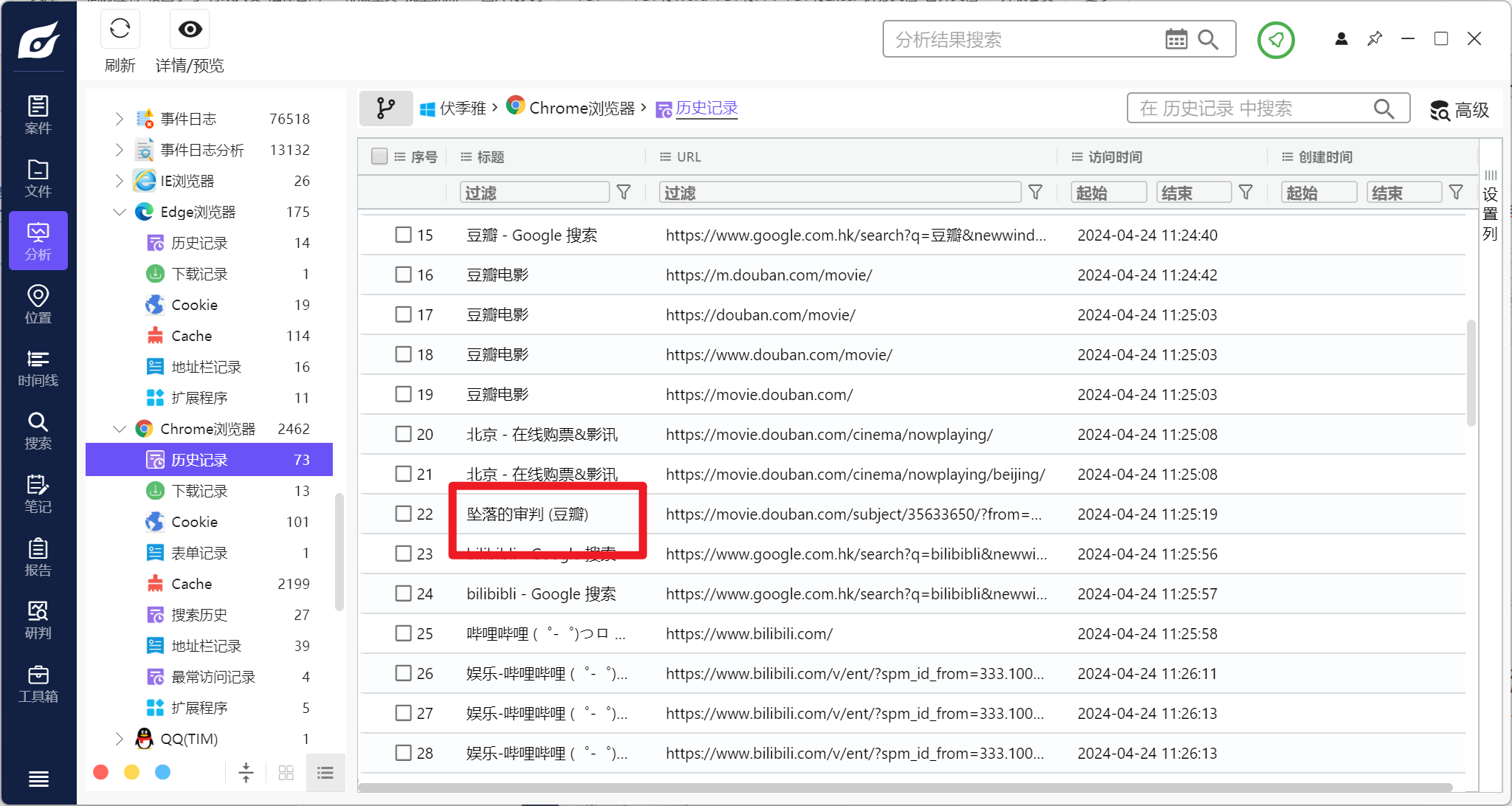
分析伏季雅的计算机检材,计算机中曾经浏览过的电影名字是:[答案格式:《奥本海默》] [★☆☆☆☆]
分析伏季雅的计算机检材,计算机中团队内部即时通讯软件的最后一次打开的时间是:[答案格式:2024-01-01-04-05-06][★☆☆☆☆]
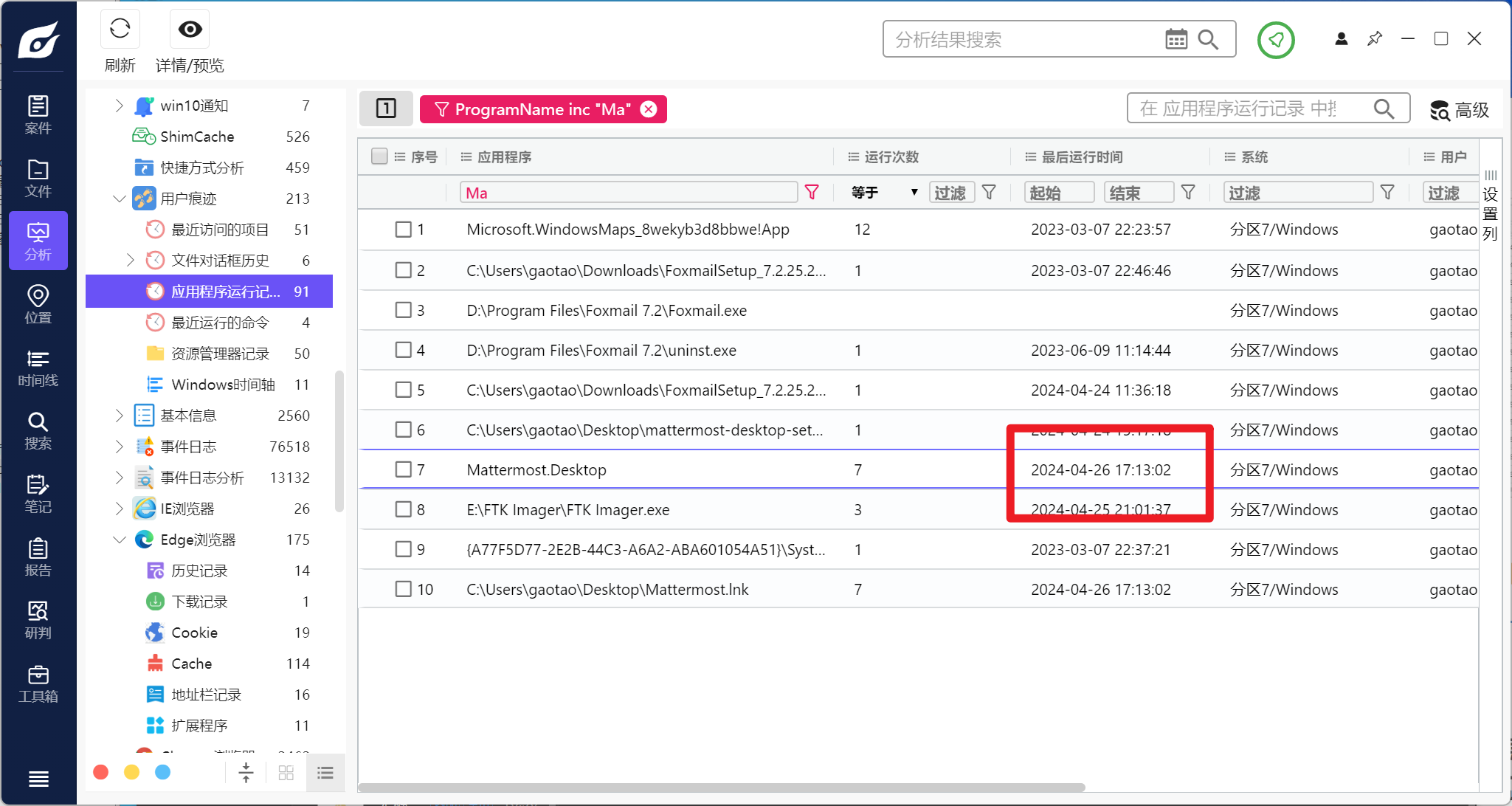
分析伏季雅的计算机检材,计算机中有一款具备虚拟视频功能的软件,该软件合计播放了多少个视频:[答案格式:3][★☆☆☆☆]
接上题,该软件的官网地址是:[答案格式:https://www.baidu.com][★☆☆☆☆]

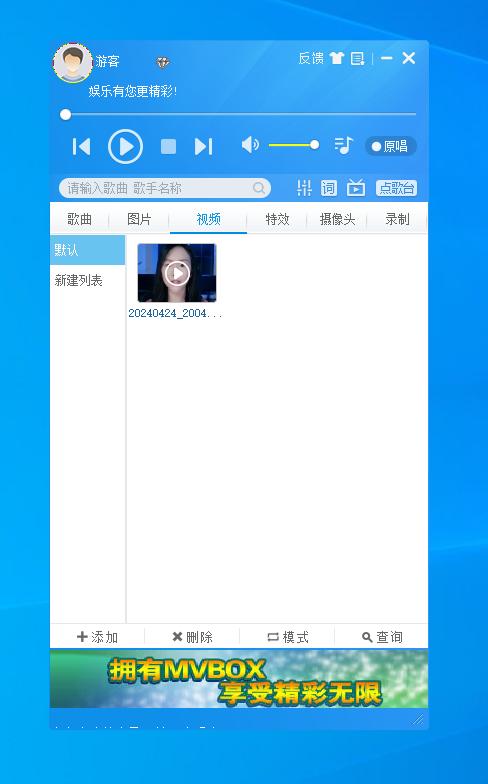
接上题,该软件录制数据时,设置的帧率是:[答案格式:20][★☆☆☆☆]
分析伏季雅的计算机检材,在团队内部使用的即时通讯软件中,其一共接收了多少条虚拟语音:[答案格式:2][★☆☆☆☆]

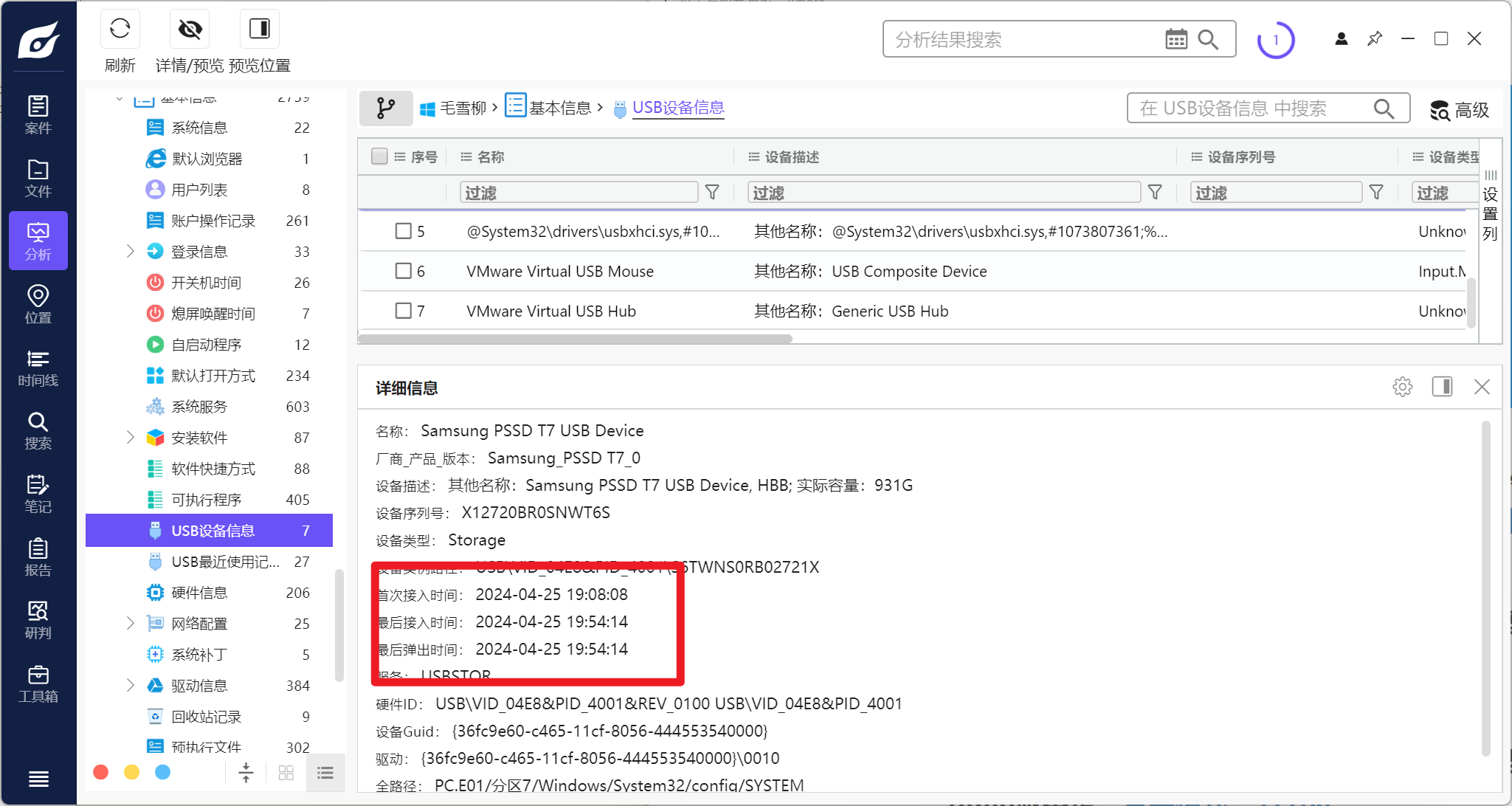
分析毛雪柳的计算机检材,计算机插入三星固态盘的时间是:[答案格式:2024-01-01-04-05-06][★☆☆☆☆]
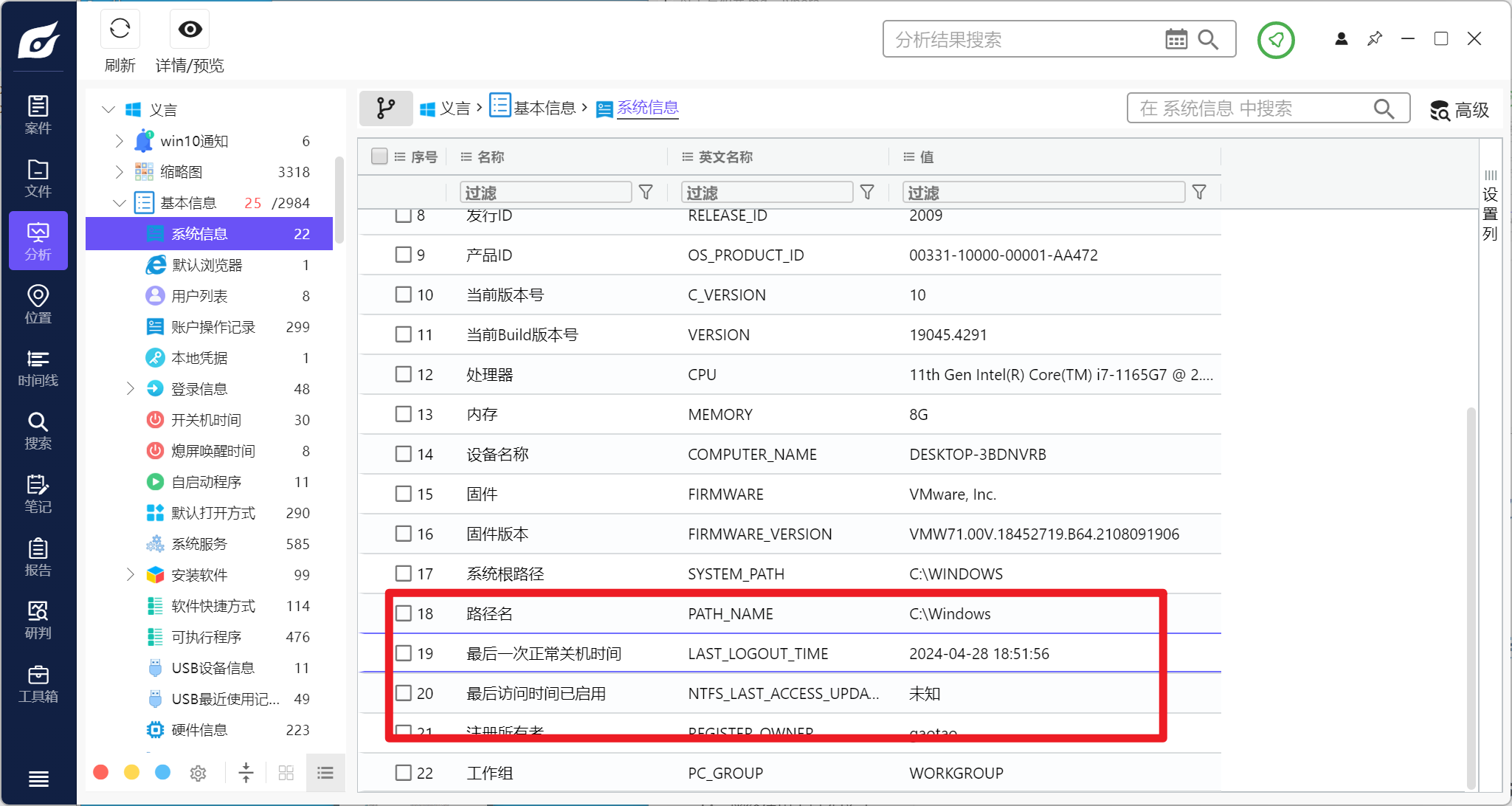
分析毛雪柳的计算机检材,计算机操作系统当前的Build版本是:[答案格式:17786][★☆☆☆☆]
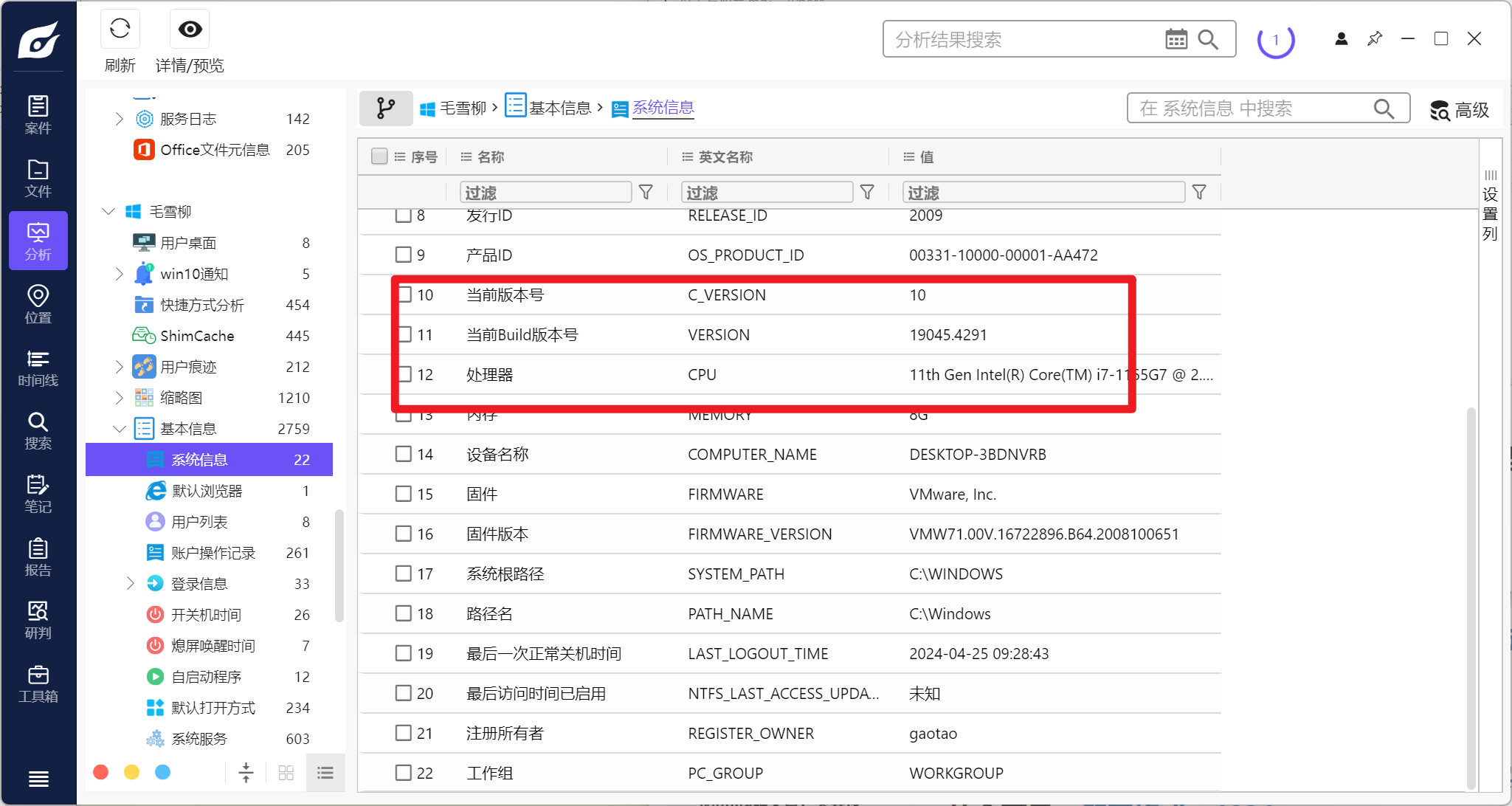
分析毛雪柳的计算机检材,团队内部使用的即时通讯软件在计算机上存储日志的文件名是:[答案格式:log.log,区分大小写][★☆☆☆☆]
分析毛雪柳的计算机检材,伏季雅一月份实发工资的金额是:[答案格式:1234][★★★☆☆]
回收站里有一个密码一个账本,密码.doc是假的

输错两次后会提示梭哈,尝试了各种隐写之后发现。。。真正的密码在毛雪柳的手机的图片里

共有5个sheet

分析毛雪柳的计算机检材,该团伙三月份的盈余多少:[答案格式:1234][★★★☆☆]

分析义言的计算机检材,计算机连接过的三星移动硬盘T7的序列号是:[答案格式:大写字母和数字][★☆☆☆☆]
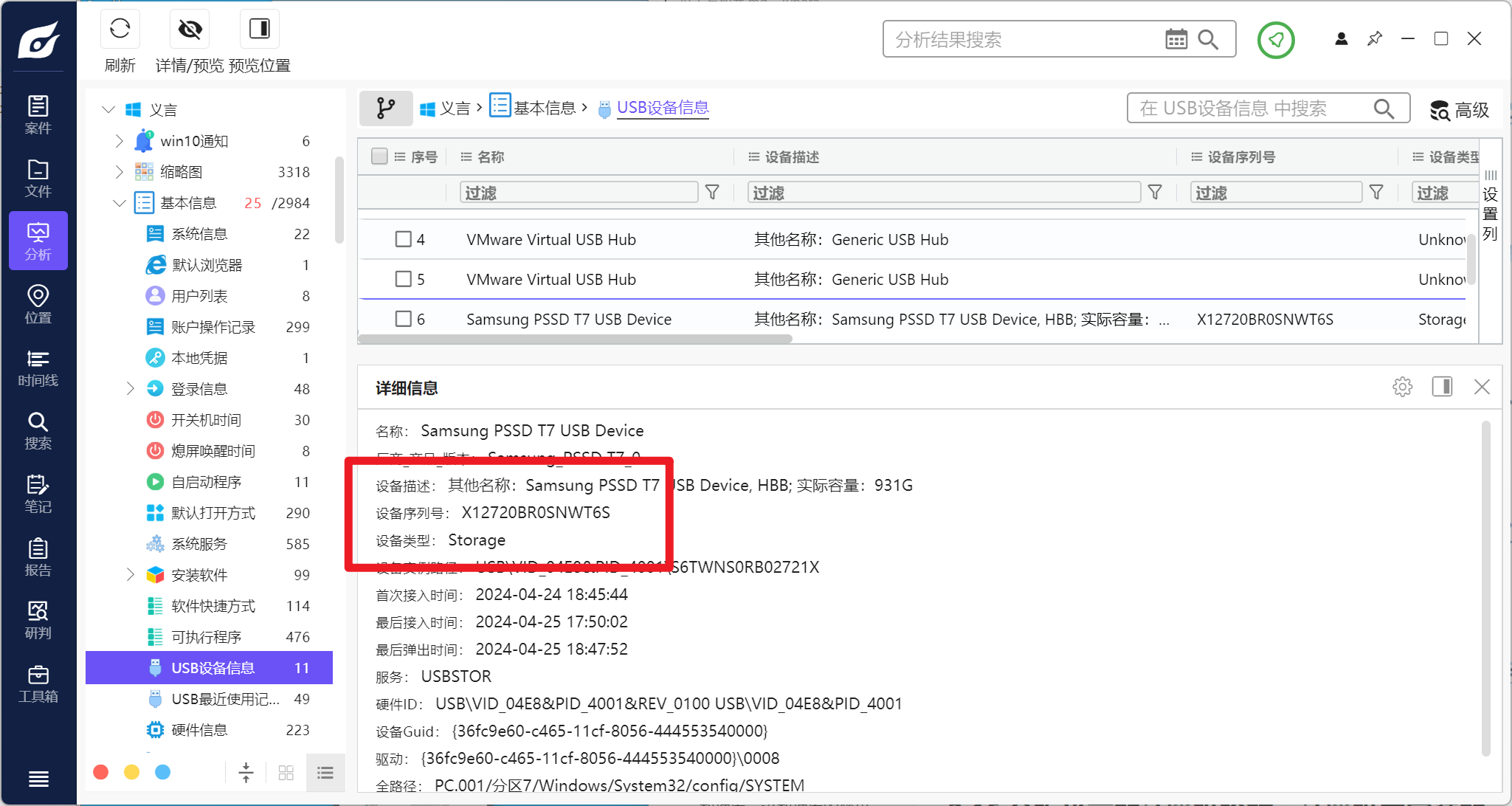
分析义言的计算机检材,计算机的最后一次正常关机时间是:[答案格式:2024-01-01-04-05-06][★☆☆☆☆]
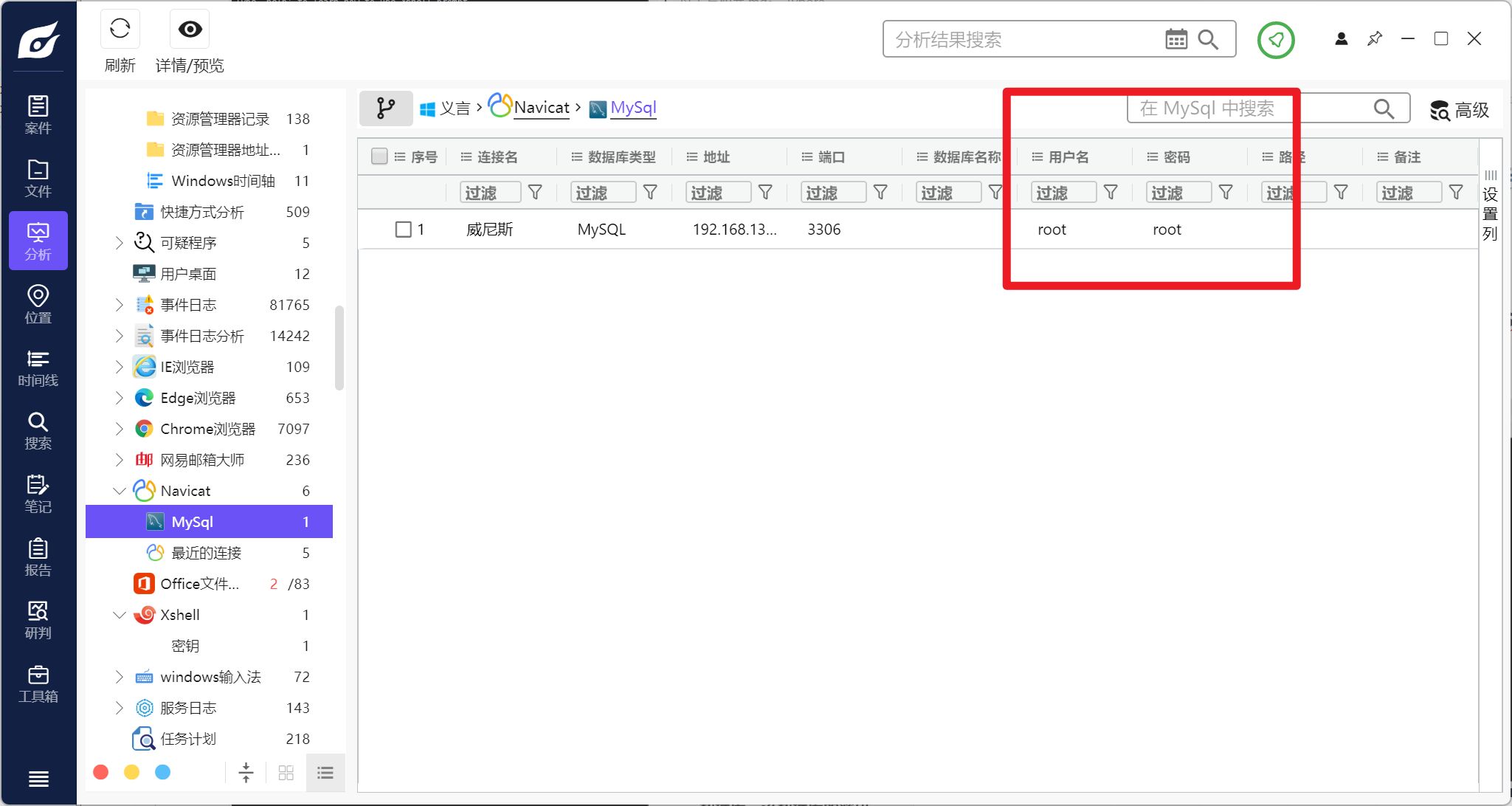
分析义言的计算机检材,曾经使用工具连接过数据库,该数据库的密码是:[答案格式:admin][★☆☆☆☆]
分析义言的计算机检材,计算机中安装的xshell软件的版本号是:[答案格式:Build-0000][★☆☆☆☆]
分析义言的计算机检材,曾使用shell工具连接过服务器,该服务器root用户的密码是:[答案格式:admin][★★★☆☆]
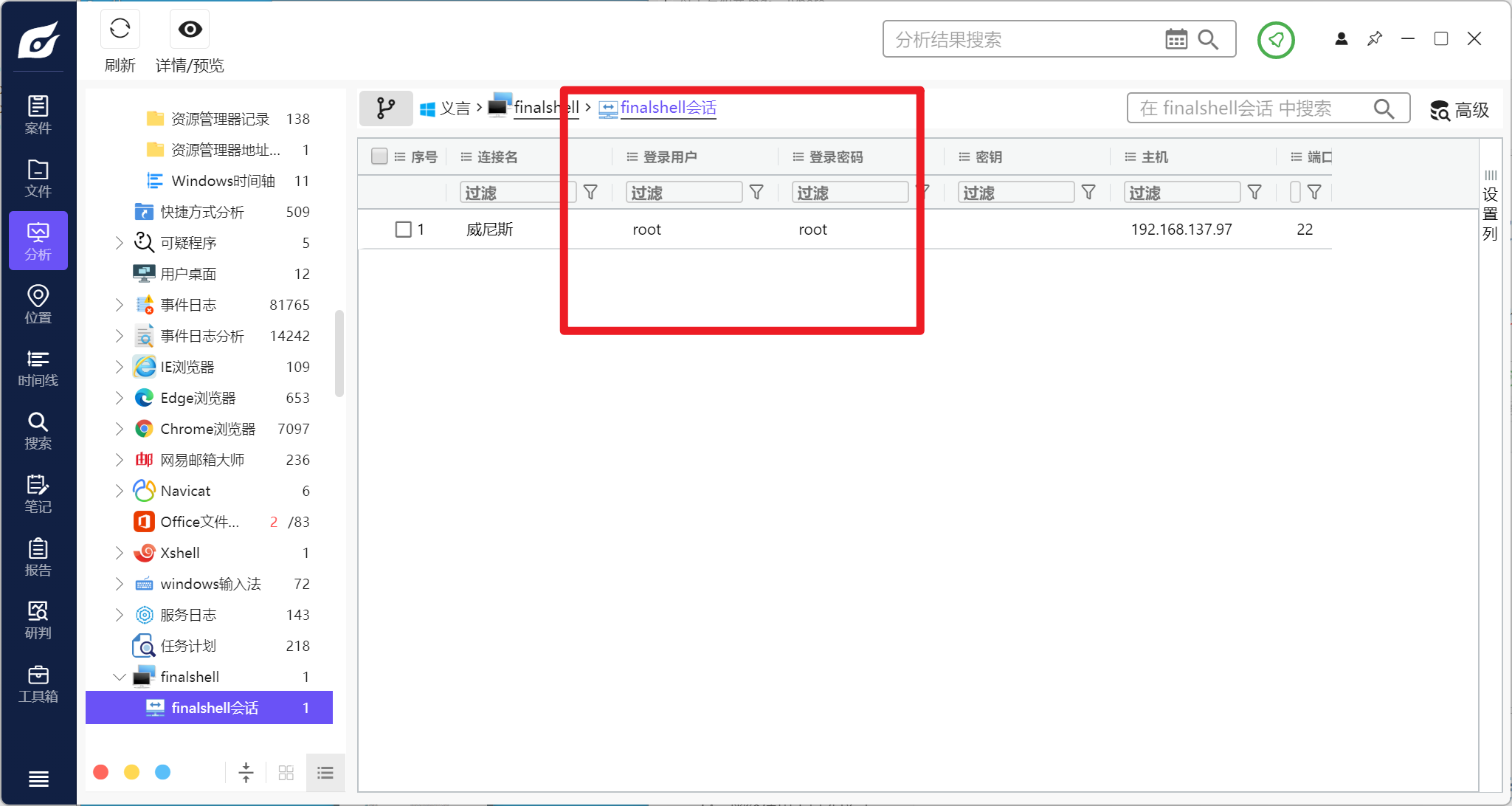
还有一种手工方法
FinalShell默认配置文件地址:
1 | %userprofile%\AppData\Local\finalshell\conn\xxx.json |
工具下载地址:https://github.com/passer-W/FinalShell-Decoder

分析义言的计算机检材,计算机曾接收到一封钓鱼邮件,该邮件发件人是:[答案格式: abc@abc.abc][★★☆☆☆]
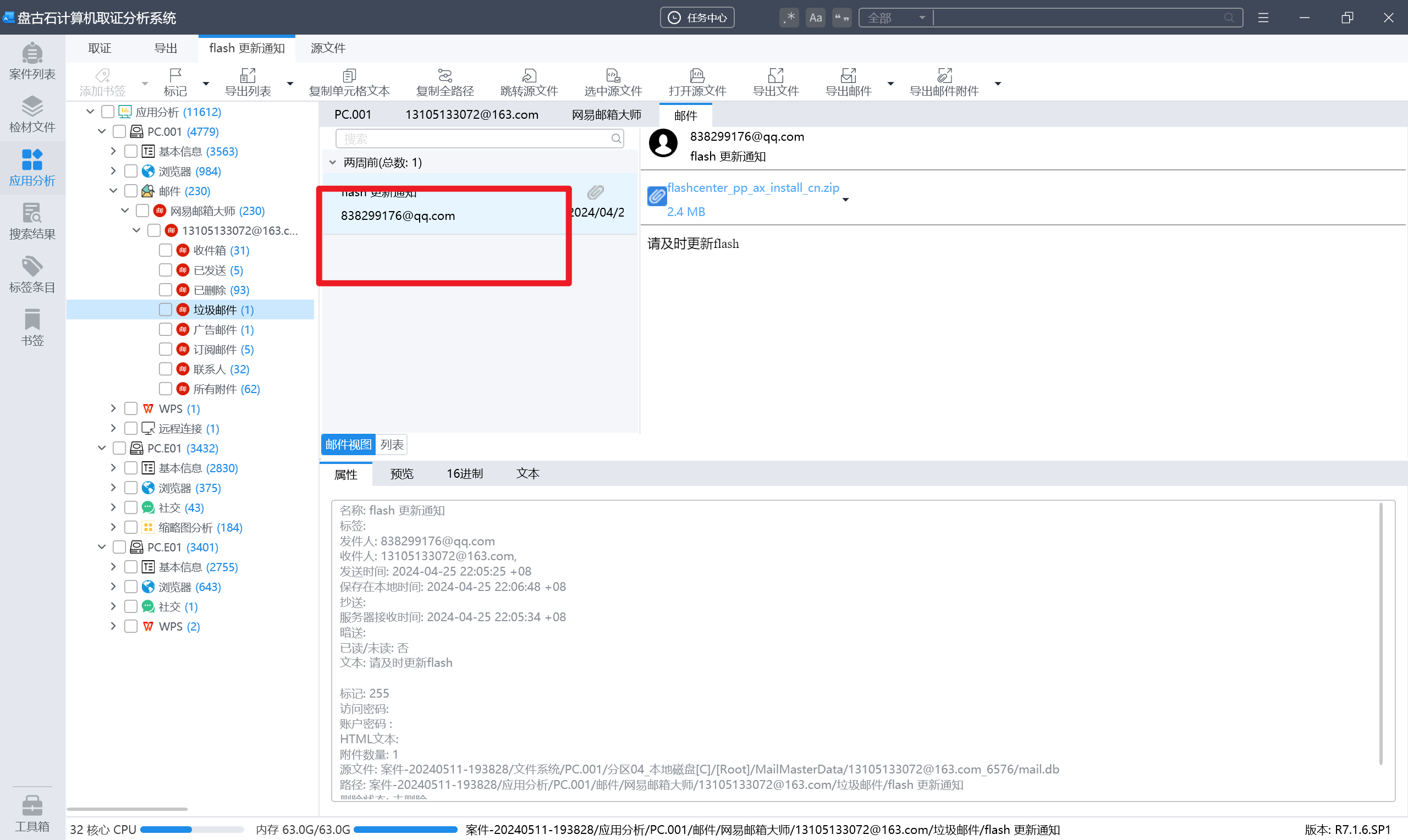
接上题,钓鱼邮件中附件的大小是多少MB:[答案格式:12.3][★★☆☆☆]
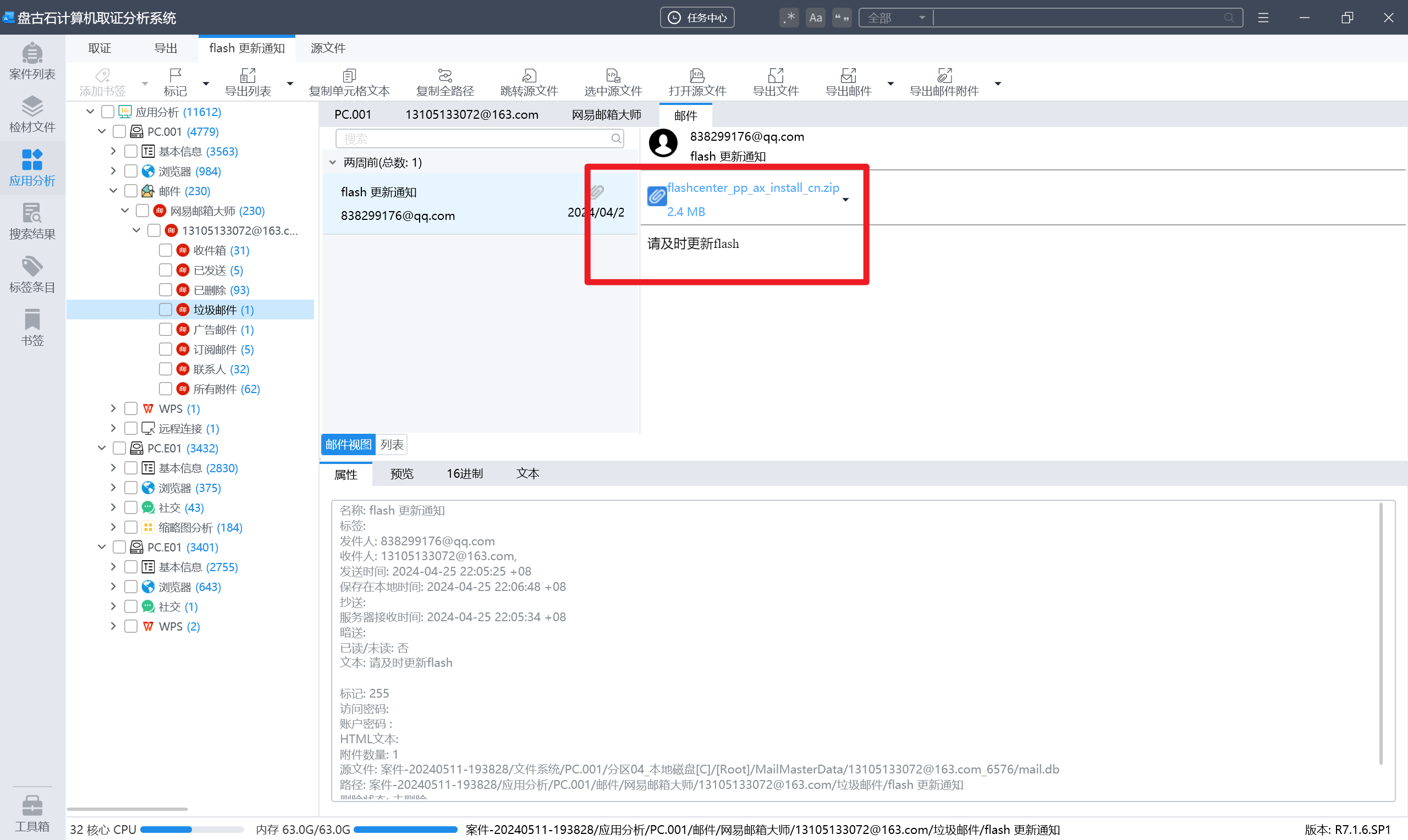
接上题,上述附件解压运行后,文件的释放位置是:[答案格式:D:\Download\test][★★☆☆☆]
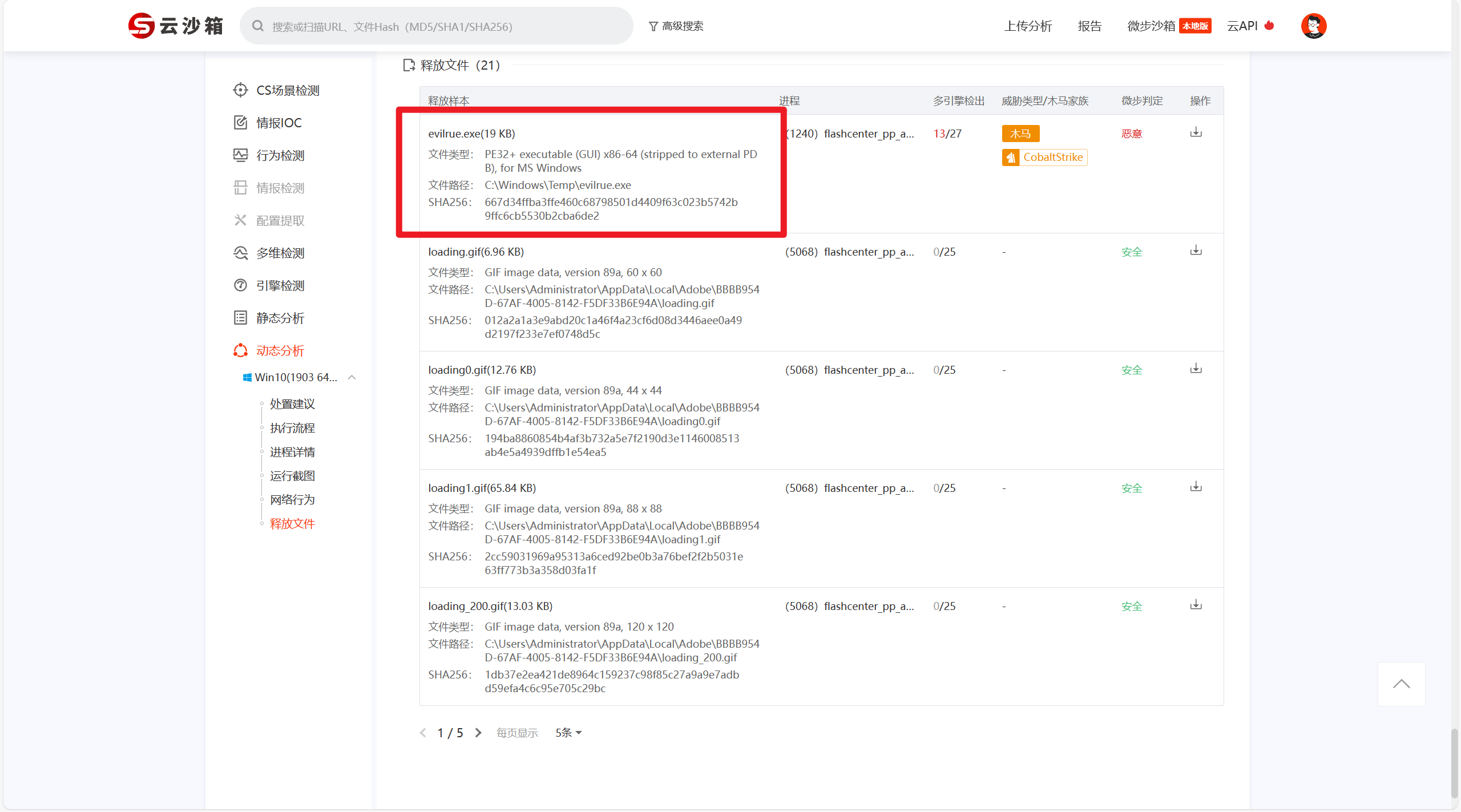
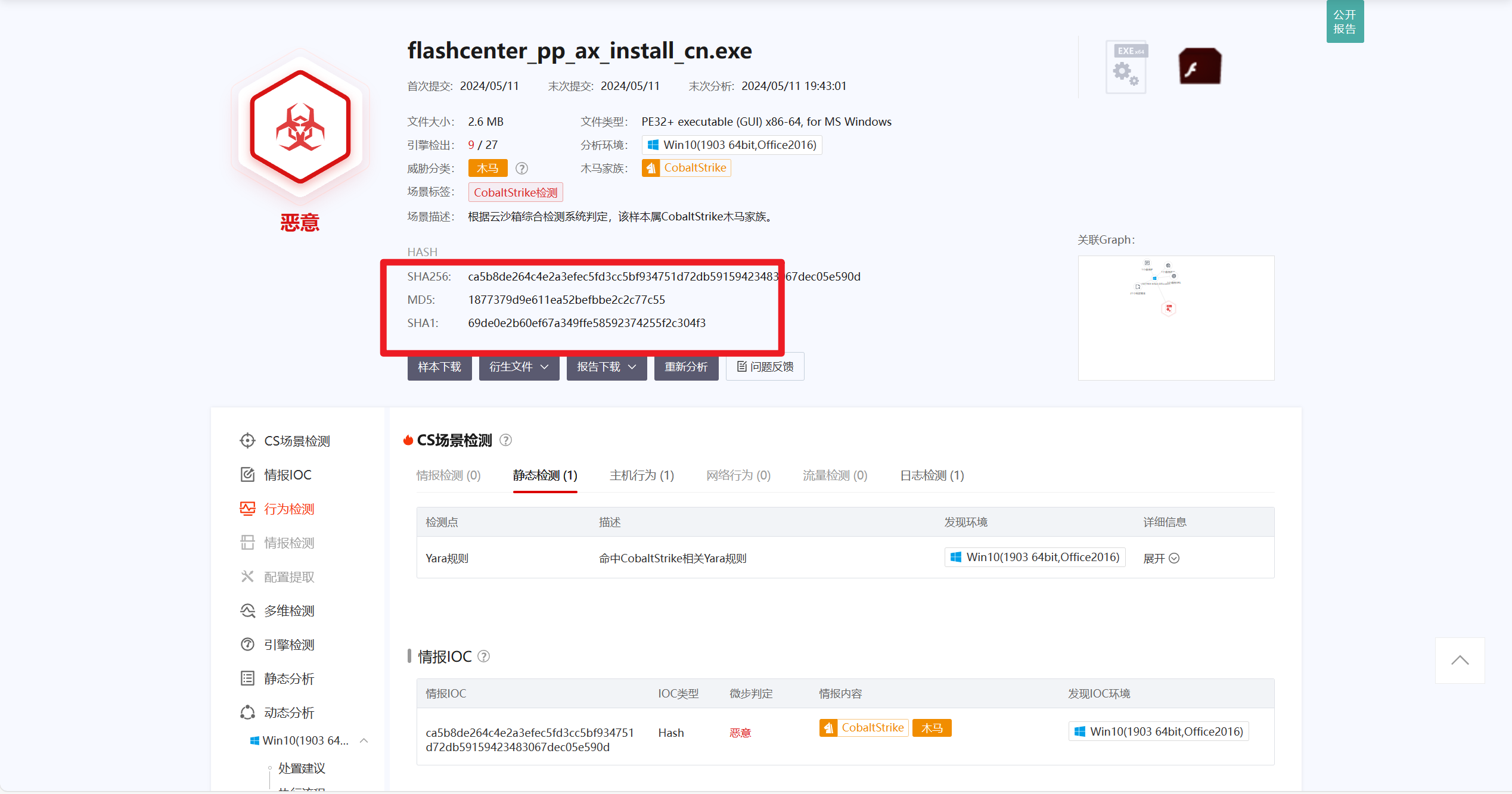
接上题,恶意木马文件的MD5 值是:[答案格式:小写][★★☆☆☆]
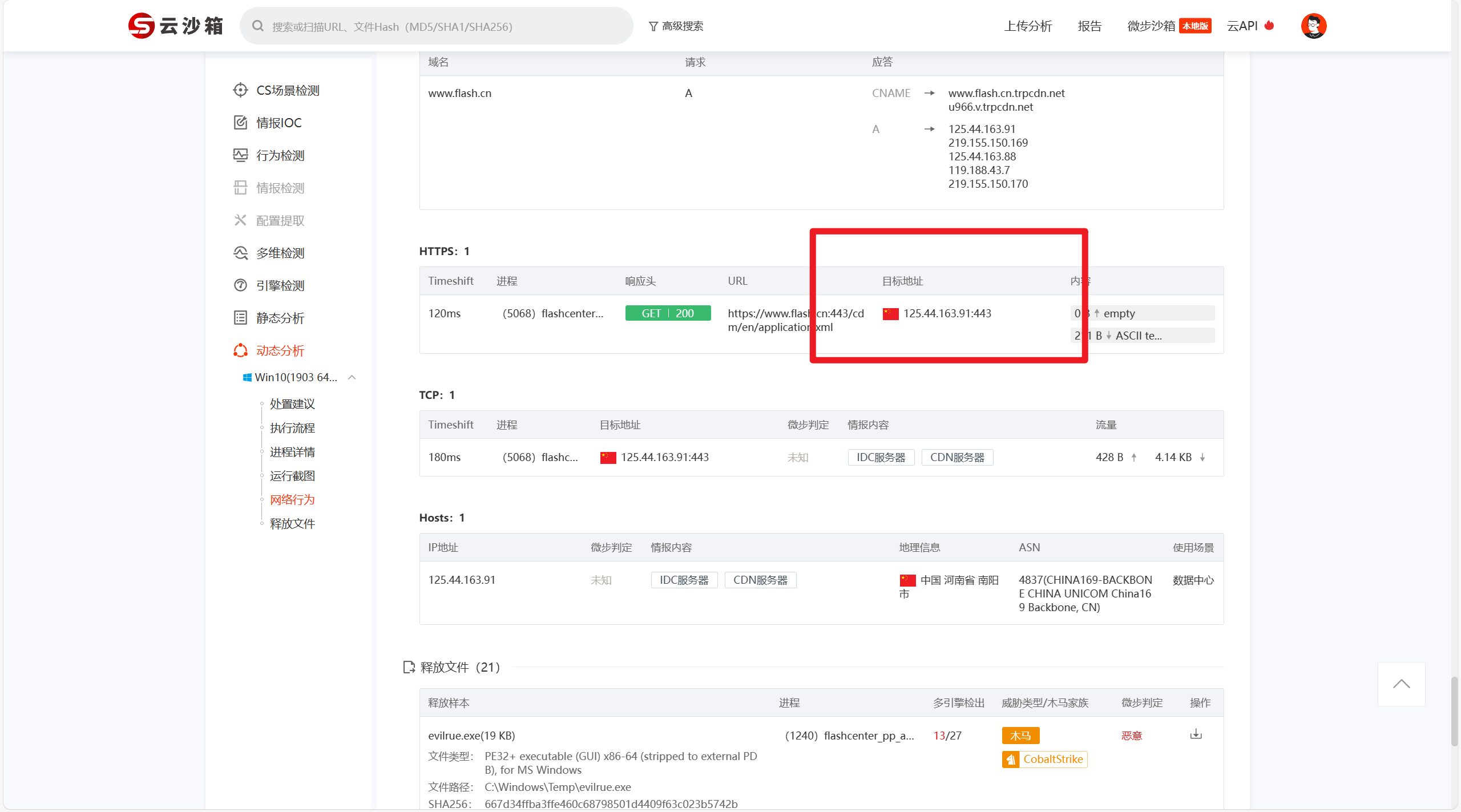
接上题,恶意木马文件的回连IP地址是:[答案格式:127.0.0.1][★★☆☆☆]
分析伏季雅的计算机检材,计算机中团队内部即时通讯软件的最后一次打开的时间是:[答案格式:2024-01-01-04-05-06][★☆☆☆☆]
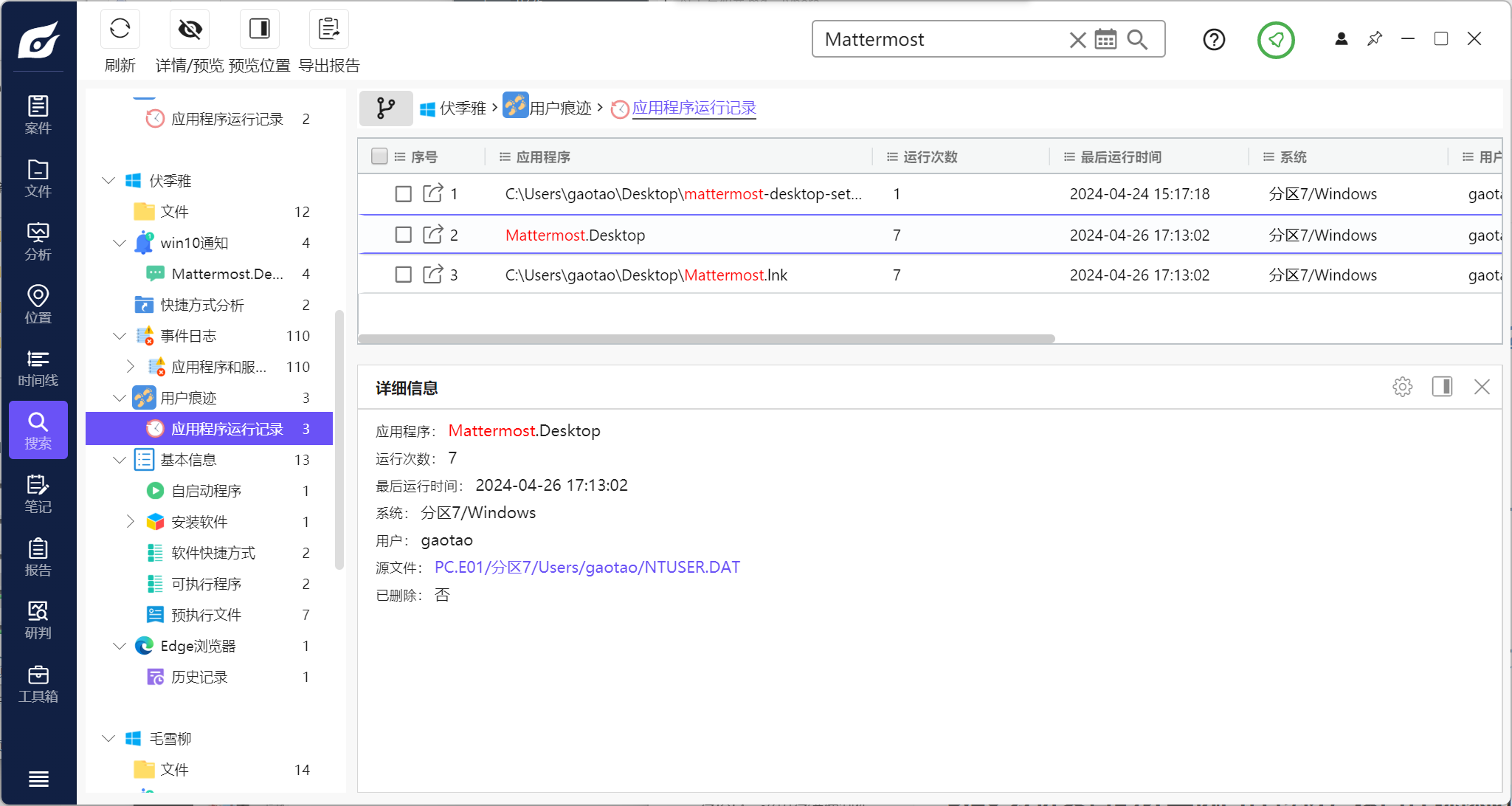
分析义言的计算机检材,计算机中保存的有隐写痕迹的文件名:[答案格式:abc.abc][★★★☆☆]
bitlocker解开后重新跑一次取证

分析义言的计算机检材,保存容器密码的文件大小是多少字节:[答案格式:123][★★★☆☆]
回收站有个lsb隐写工具
在本地测试后隐写后的图片会变成bmp格式

提取

火眼爆搜bmp格式,从大往下,有几个感觉比较可疑

导出后解密

解密vc

里面都是encrypt.exe里加密过的
答案

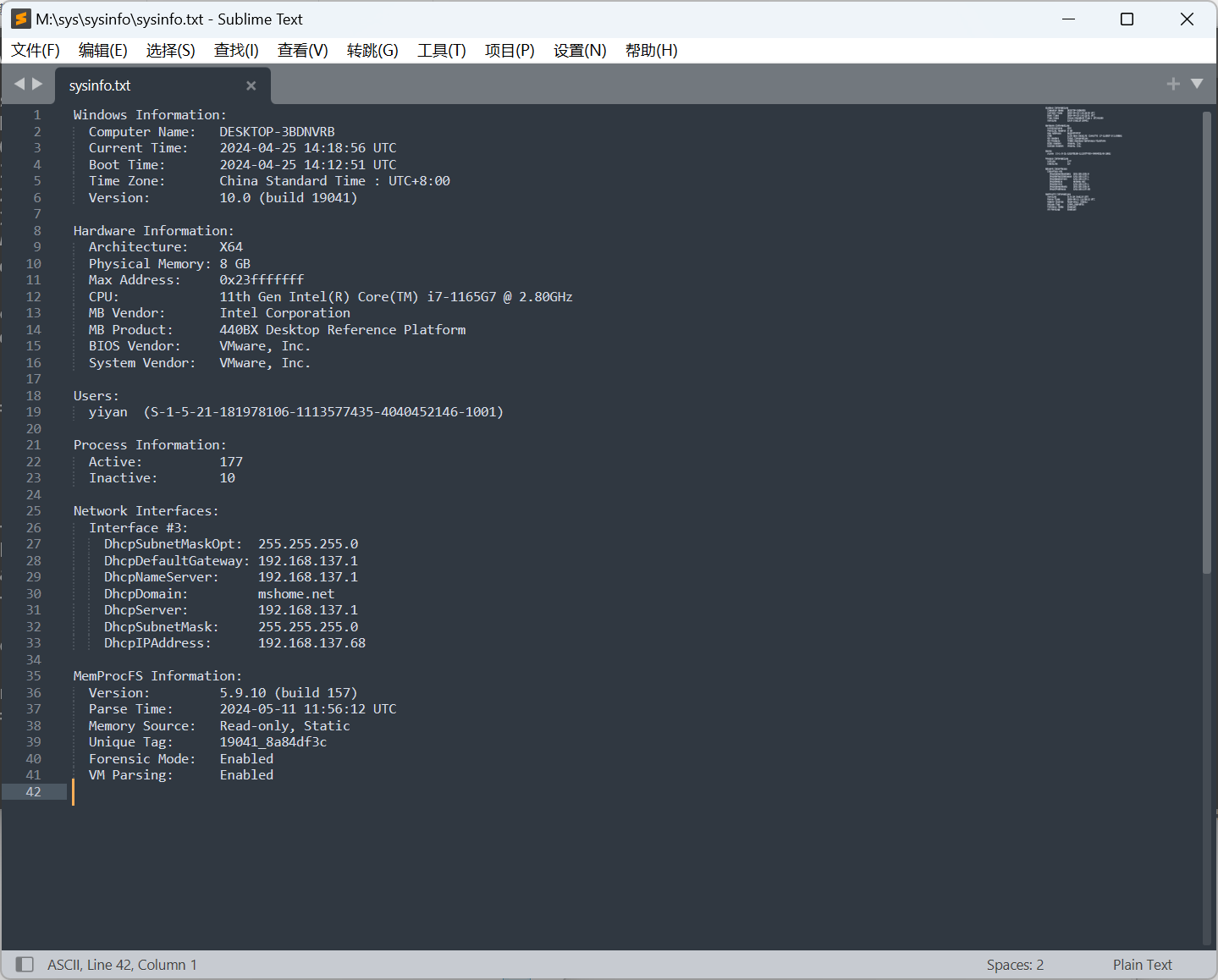
分析义言的计算机内存检材,该内存镜像制作时间(UTC+8)是:[答案格式:2024-01-01-04-05][★★☆☆☆]
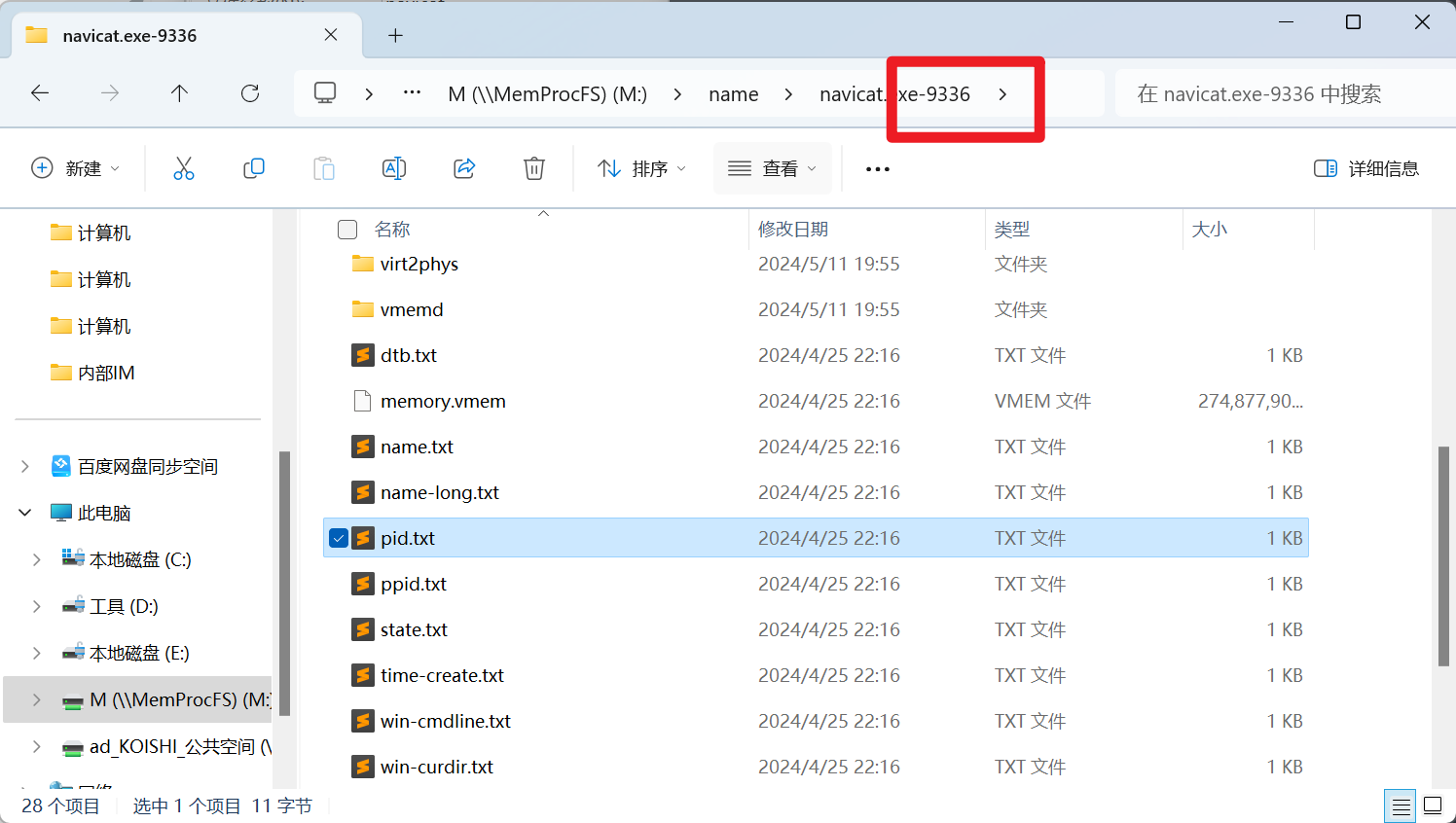
分析义言的计算机内存检材,navicat.exe的进程ID是:[答案格式:123][★★☆☆☆]
IPA取证
分析毛雪柳的手机检材,记账APP存储记账信息的数据库文件名称是:[答案格式:tmp.db,区分大小写][★★★★☆]
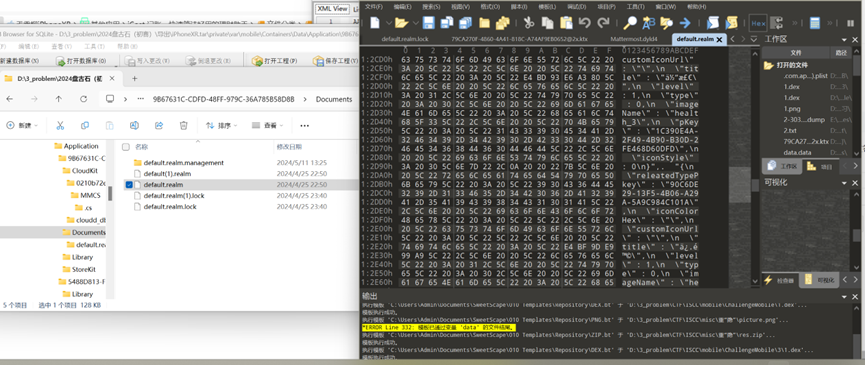
分析毛雪柳的手机检材,记账APP中,2月份总收入金额是多少:[答案格式:1234][★★★★★]
这个文件需要用realm studio打开
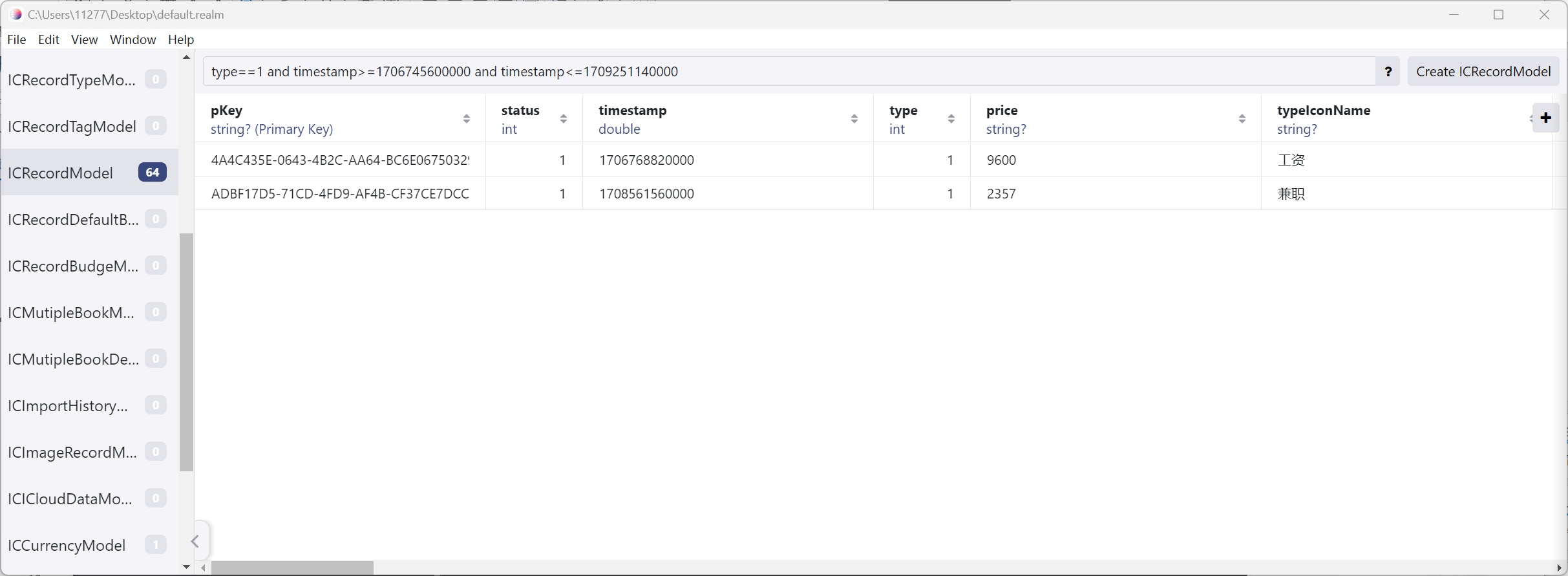
分析毛雪柳的手机检材,手机中团队内部使用的即时通讯软件中,团队老板的邮箱账号是:[答案格式:abc@abc.com][★★★☆☆]
服务器顺下来就知道,也不用看数据库
接上题,该内部即时通讯软件中,毛雪柳和老板的私聊频道中,老板加入私聊频道的时间是:[答案格式:2024-01-01-04-05-06][★★★☆☆]
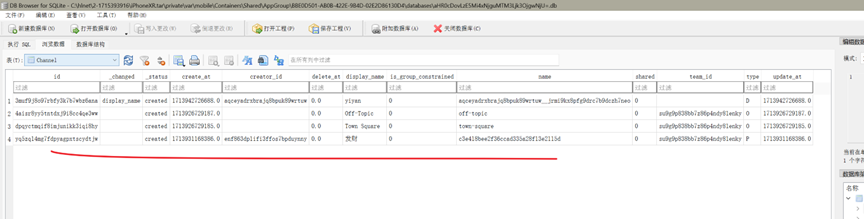
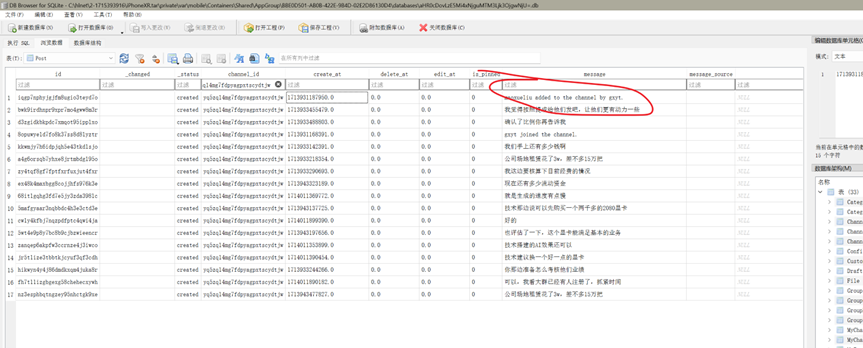
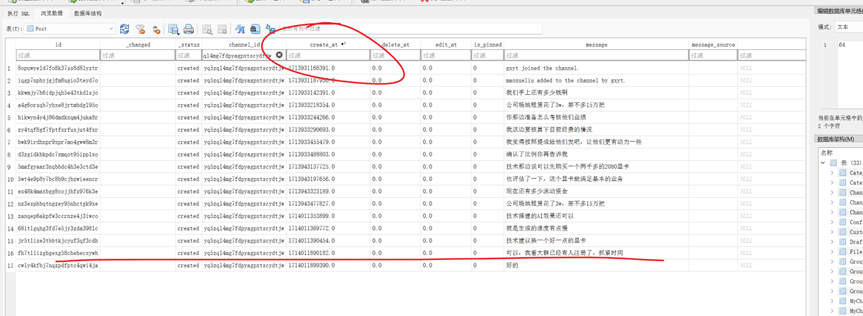
接上题,该私聊频道中,老板最后一次发送聊天内容的时间是:[答案格式:2024-01-01-04-05-06][★★★☆☆]
APK取证
分析伏季雅的手机检材,手机中诈骗APP的包名是:[答案格式:abc.abc.abc,区分大小写][★☆☆☆☆]
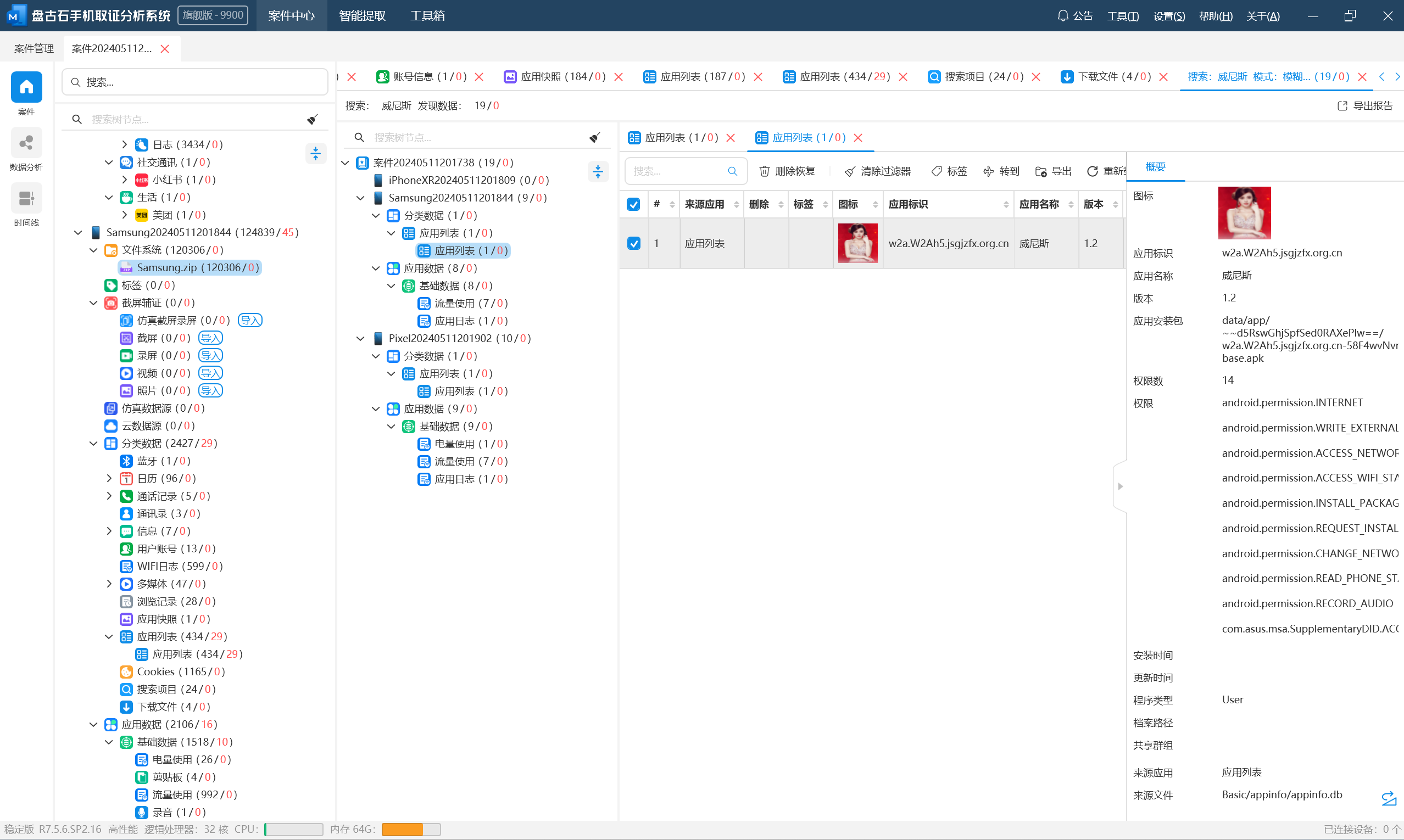
分析伏季雅的手机检材,手机中诈骗APP连接的服务器地址是:[答案格式:127.0.0.1][★☆☆☆☆]
别的忽略,,,我们校园网的包
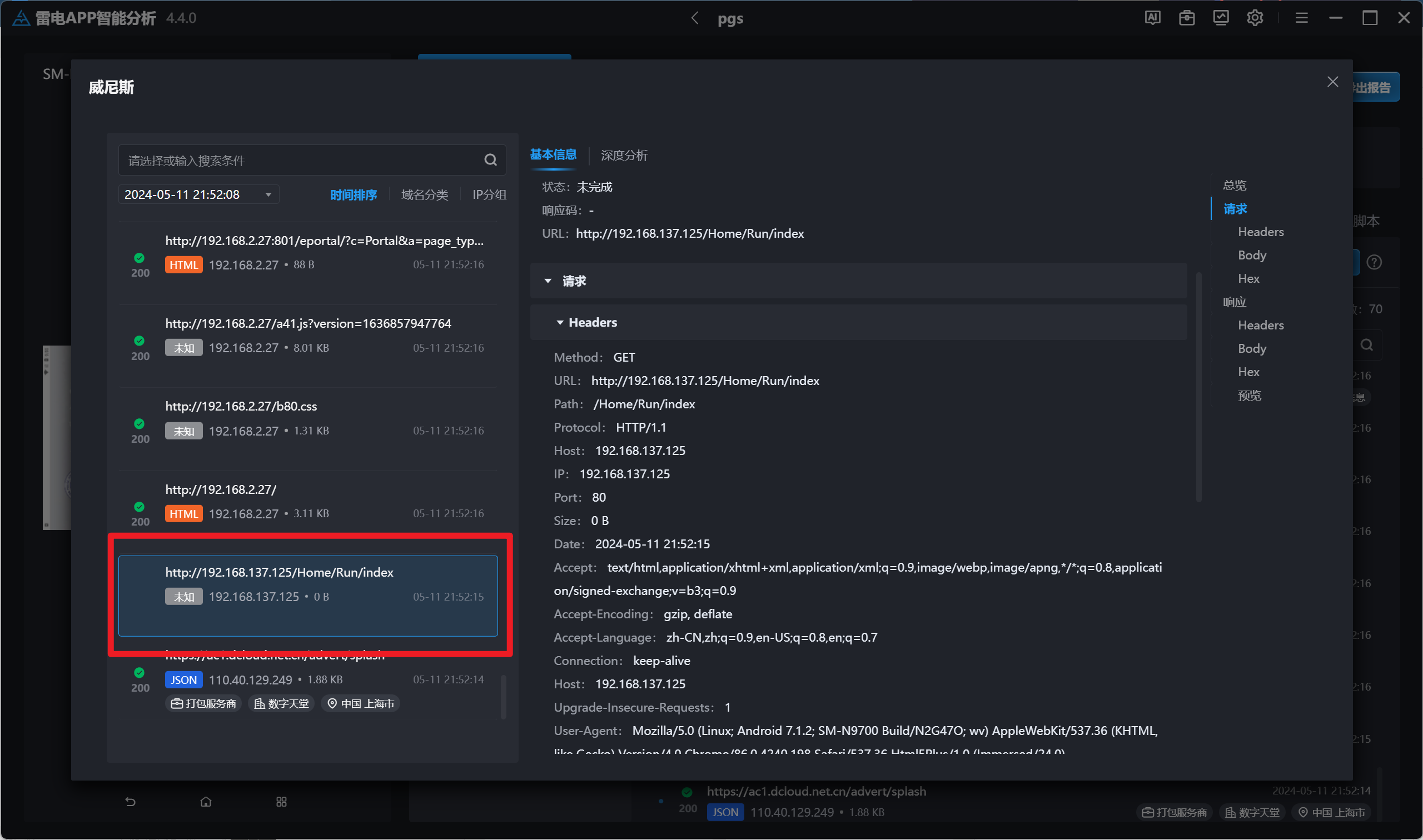
分析伏季雅的手机检材,手机中诈骗APP的打包ID是:[答案格式:_abc_abc.abc,区分大小写][★☆☆☆☆]
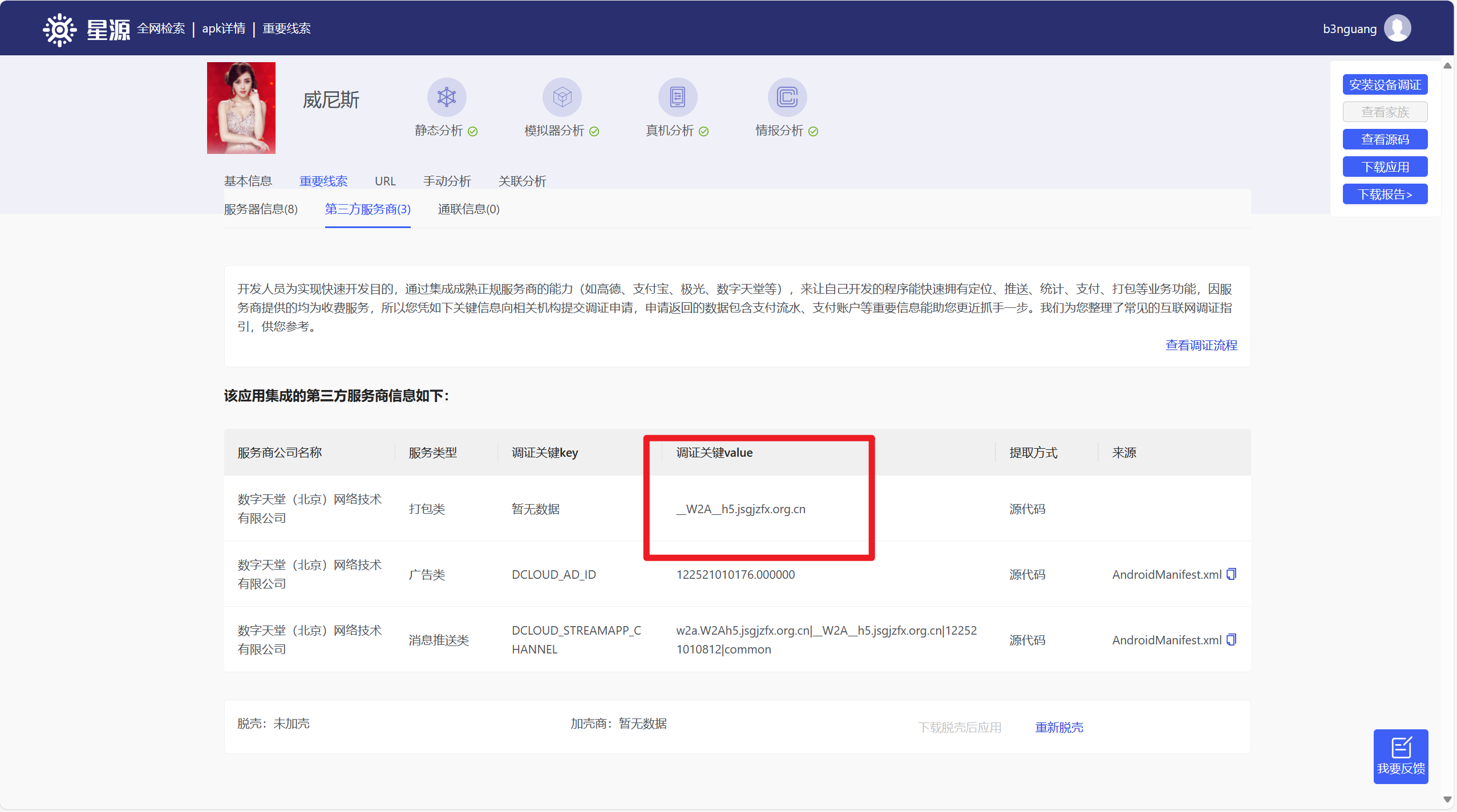
分析伏季雅的手机检材,手机中诈骗APP的主启动项是:[答案格式:abc.abc.abc,区分大小写][★☆☆☆☆]
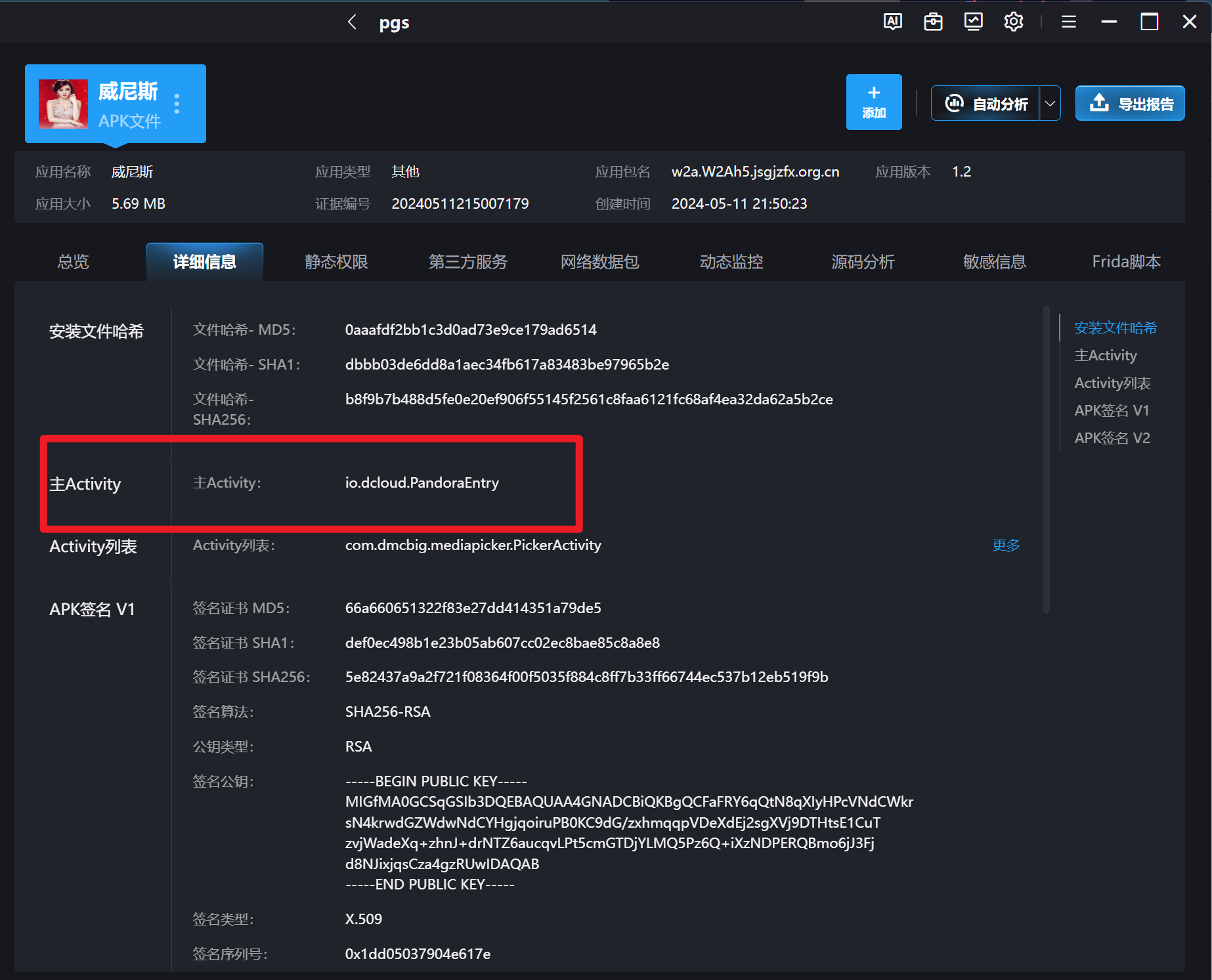
分析义言的手机检材,分析团队内部使用的即时通讯软件,该软件连接服务器的地址是:[答案格式:127.0.0.1][★★☆☆☆]
IM服务器的ip地址:192.168.137.97
接上题,该软件存储聊天信息的数据库文件名称是:[答案格式:abc.abc,区分大小写][★★☆☆☆]
接上题,该即时通讯软件中,团队内部沟通群中,一共有多少个用户:[答案格式:1][★★☆☆☆]
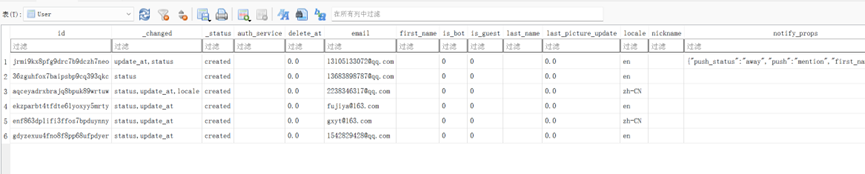
接上题,该即时通讯应用的版本号是:[答案格式:1.1.1][★★☆☆☆]
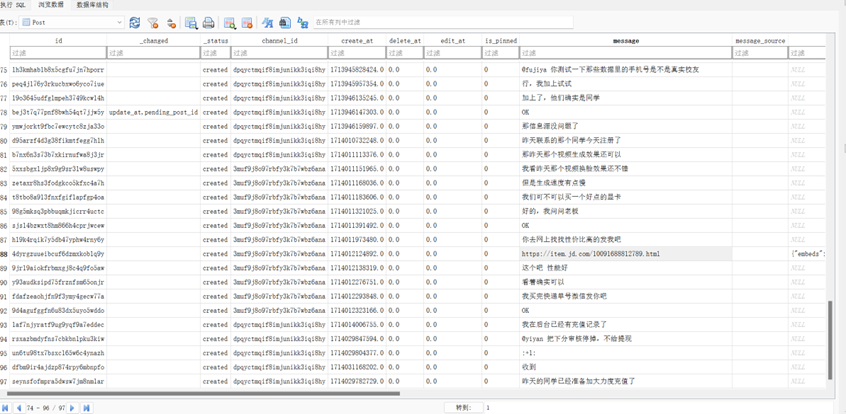
接上题,该即时通讯应用中,团队内部沟通中曾发送了一个视频文件,该视频文件发送者的用户名是:[答案格式:abc][★★★★☆]
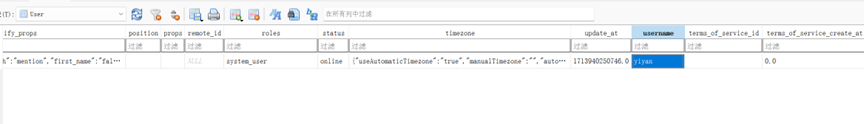
yiyan
file表格里面,每个文件都有对应的发送id
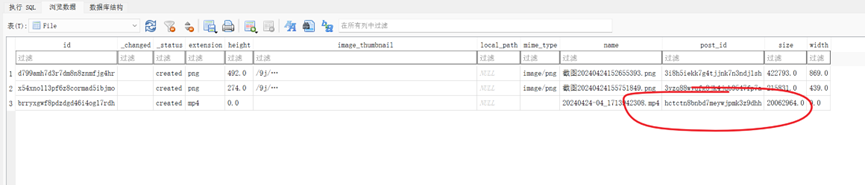
带着post_id到post表里面去查,找到对应消息记录的user_id
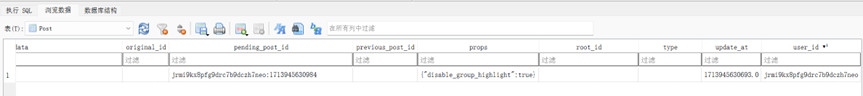
带着user_id去user表里面去查,得到username
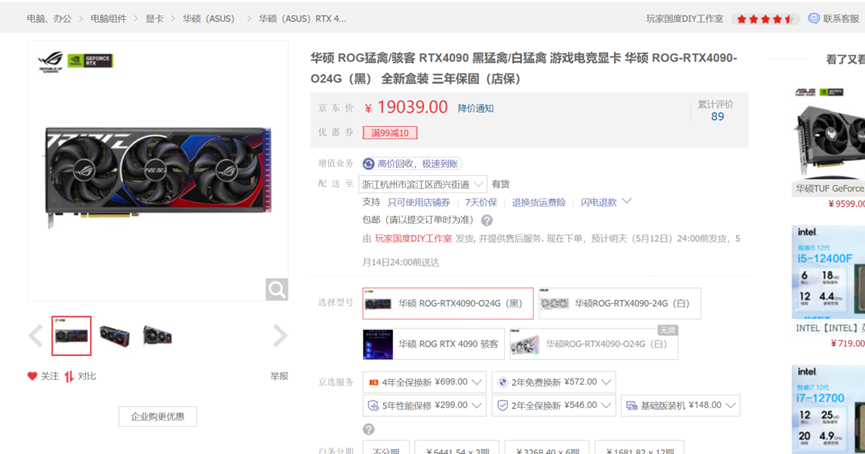
接上题,分析该即时通讯的聊天记录,团队购买了一个高性能显卡,该显卡的显存大小是:[答案格式:20G][★★☆☆☆]
分析义言的手机检材,手机中装有一个具备隐藏功能的APP,该APP启动设置了密码,设置的密码长度是多少位:[答案格式:5][★★★★☆]
这边是搜包名的时候运气好碰到老外的分析记录,直接把其成果拿来用了
https://theincidentalchewtoy.wordpress.com/2021/12/07/decrypting-the-calculator-apps/
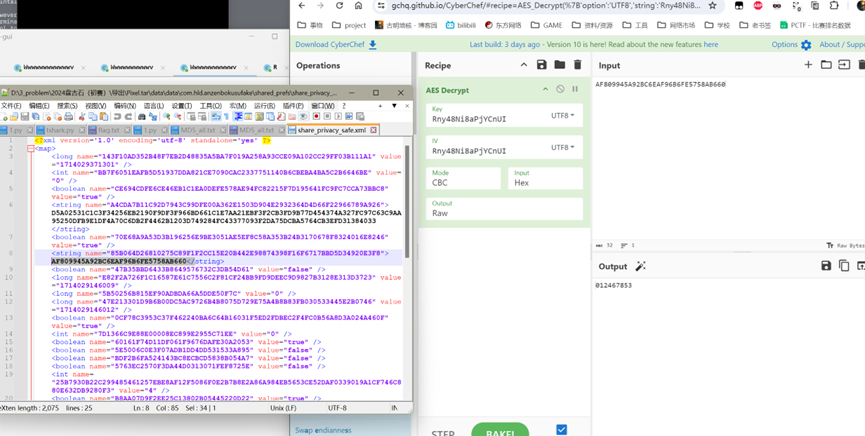
实际上有更明了的做法——直接hook安卓加密库,然后就能发现几乎所有的字符串都是使用AES(而且是使用同一个密钥和iv解的)
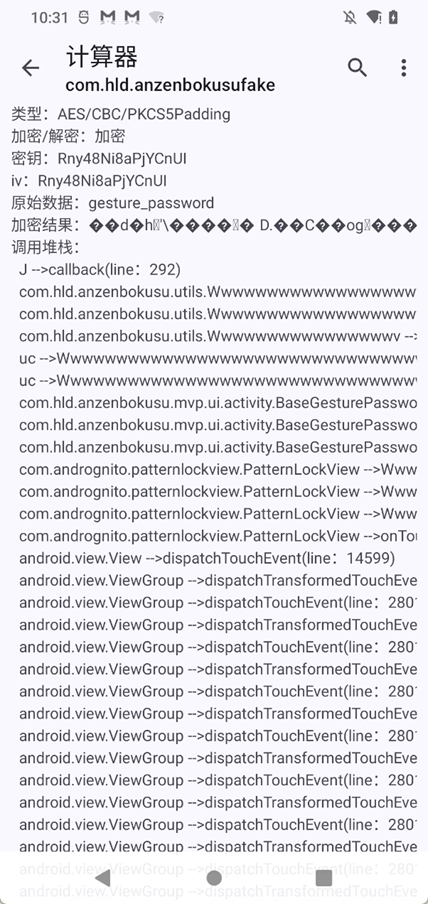
除此之外,hook文件操作方法,还有大量对/data/user/0/com.hld.anzenbokusufake/shared_prefs/share_privacy_safe.xml的写入操作
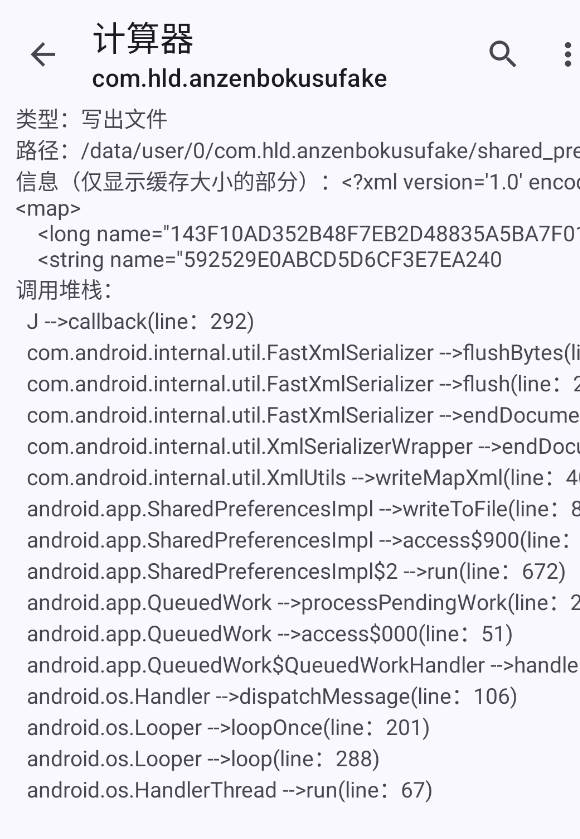
所以可以定位到share_privacy_safe.xml这个文件,把里面的字符串进行解密即可
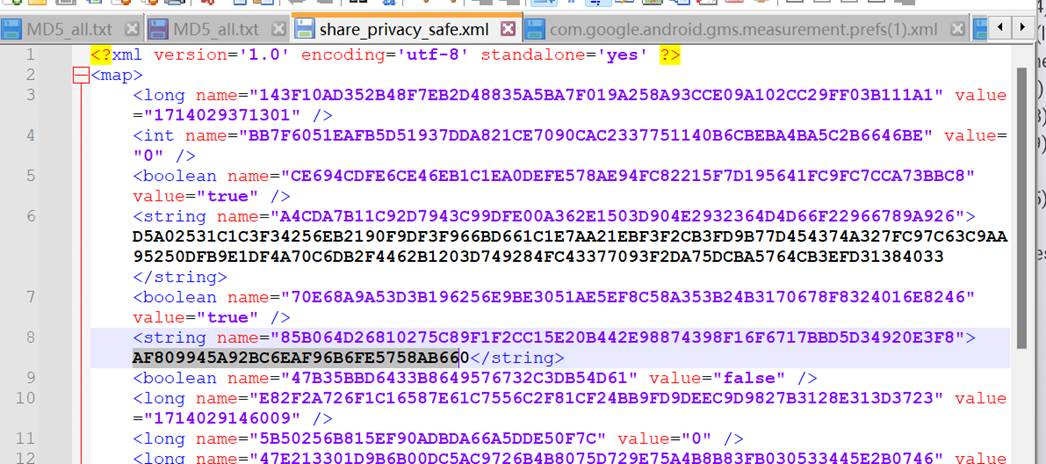
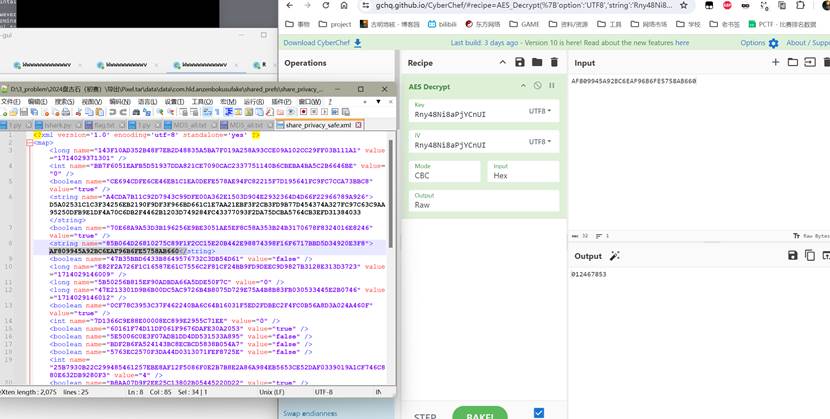
接上题,分析上述隐藏功能的APP,一共隐藏了多少个应用:[答案格式:1][★★★★☆]
这里是文章里面没有的。静态分析因为强混淆所以不是很好搞,这里继续hook文件操作方法,随便加密几个文件之后就能hook到写出文件的路径了——/storage/emulated/0/.privacy_safe
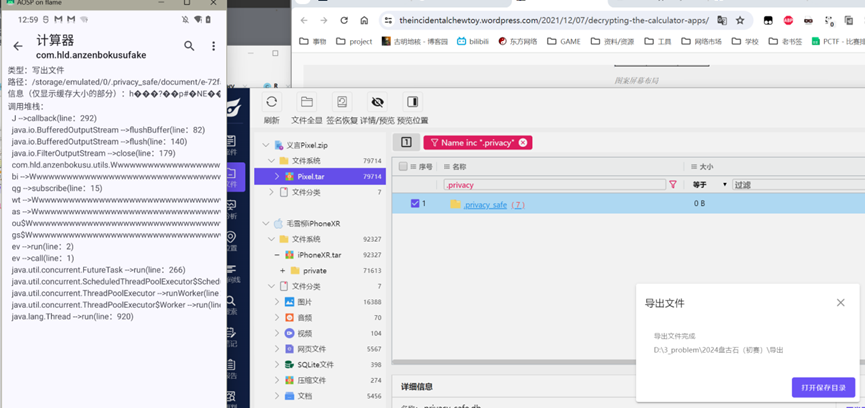
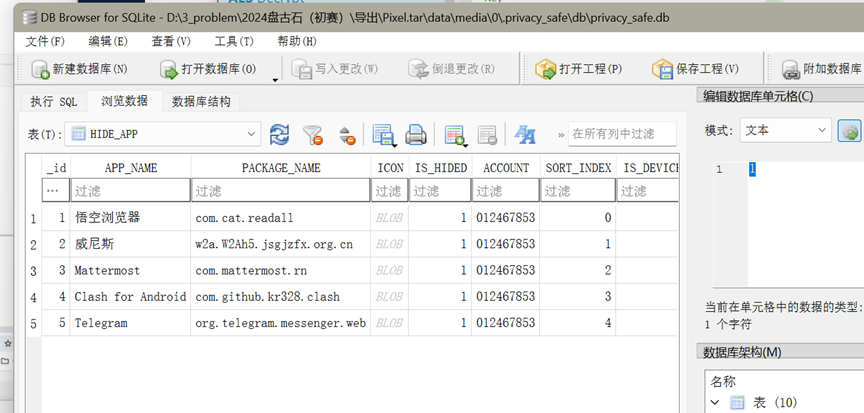
接上题,分析上述隐藏功能的APP,该APP一共加密了多少个文件:[答案格式:][★★★★☆]
数据库是加密的,需要使用DB Browser for SQLCipher.exe加上密码Rny48Ni8aPjYCnUI去打开这个db文件
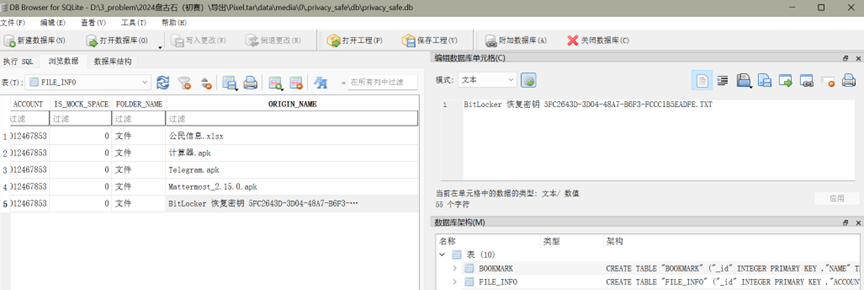
接上题,分析上述隐藏功能的APP,该APP加密了一份含有公民隐私信息的文件,该文件的原始名称是:[答案格式:abc.txt][★★★★☆]
公民信息.xlsx
分析义言的手机检材,马伟的手机号码是:[答案格式:13012341234][★★★★☆]
解密也是使用Rny48Ni8aPjYCnUI加上AES算法即可
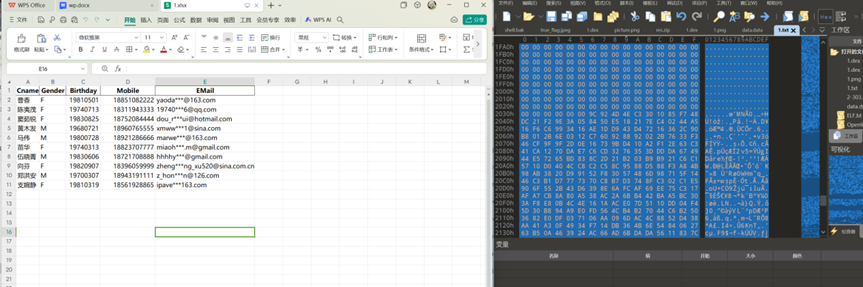
分析义言的手机检材,手机中存有一个BitLocker恢复密钥文件,文件已被加密,原始文件的MD5值是:[答案格式:小写字母和数字][★★★★☆]
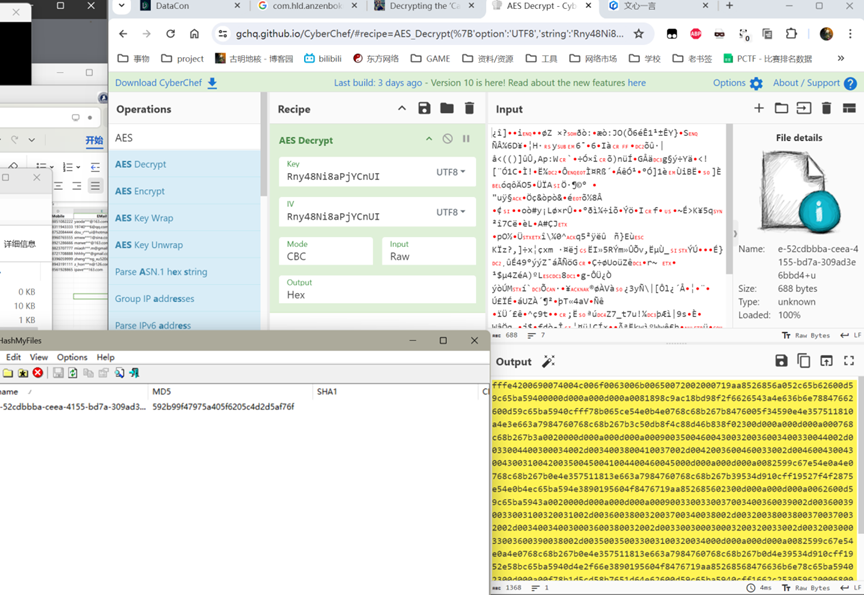
解出来的结果里是gb2312编码存储的bitlocker文件
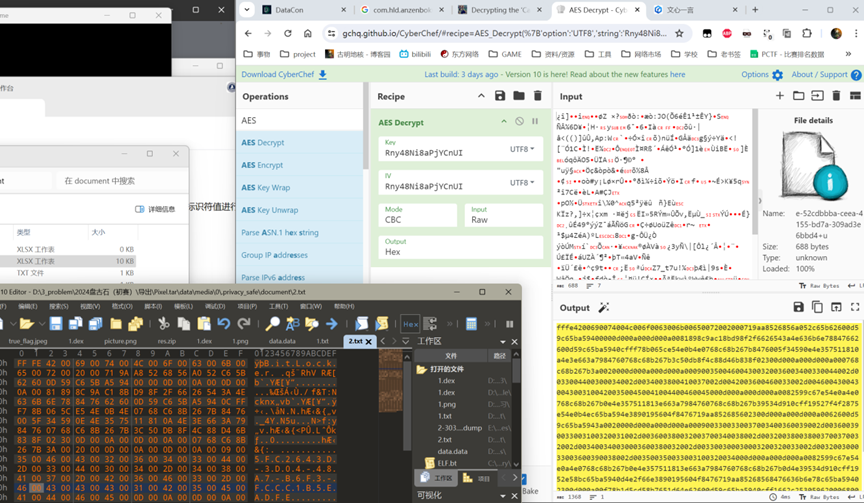
手机取证
分析伏季雅的手机检材,手机的安卓ID是:[答案格式:小写字母和数字][★☆☆☆☆]
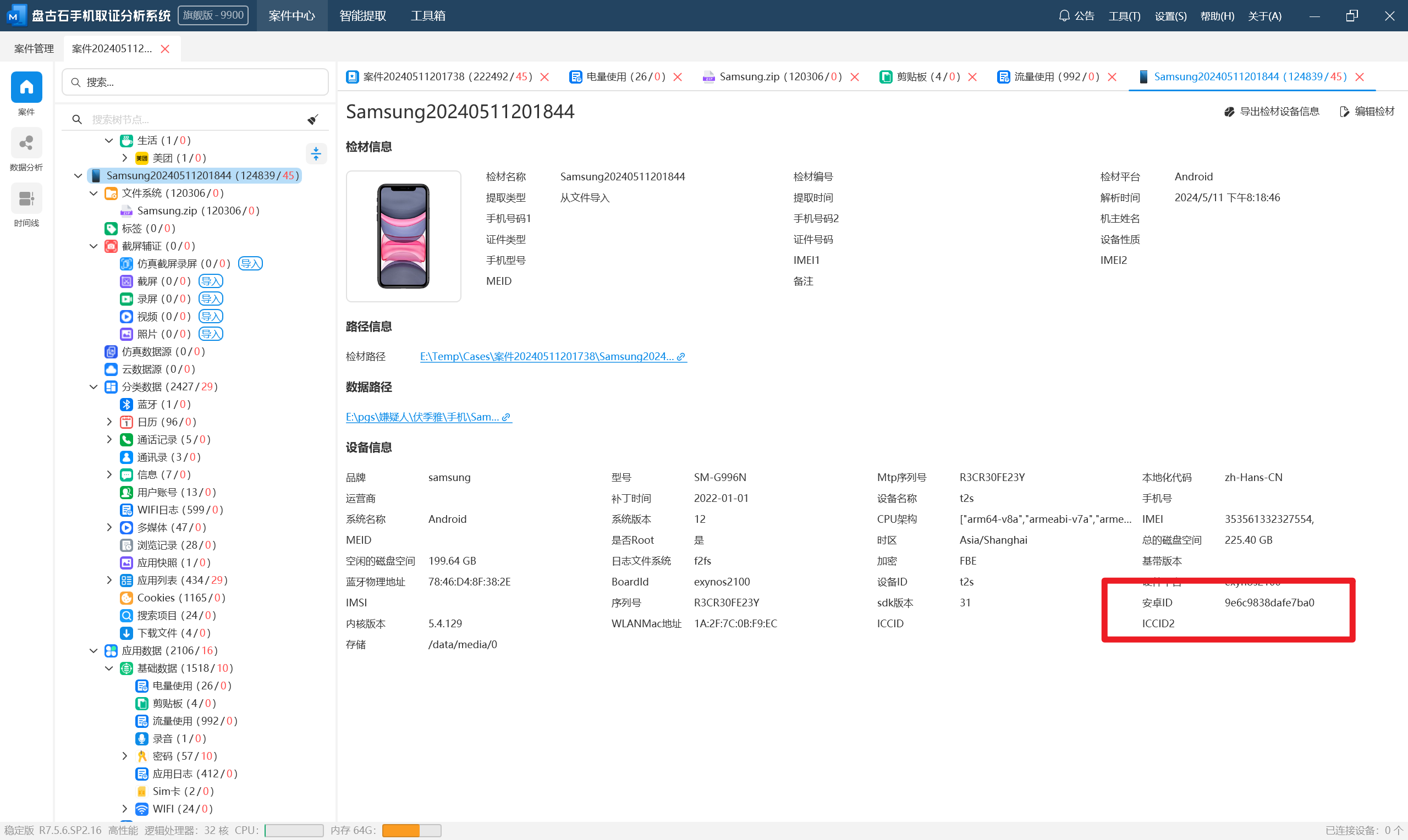
分析伏季雅的手机检材,手机型号是:[答案格式:HUAWEI-FL56T][★☆☆☆☆]
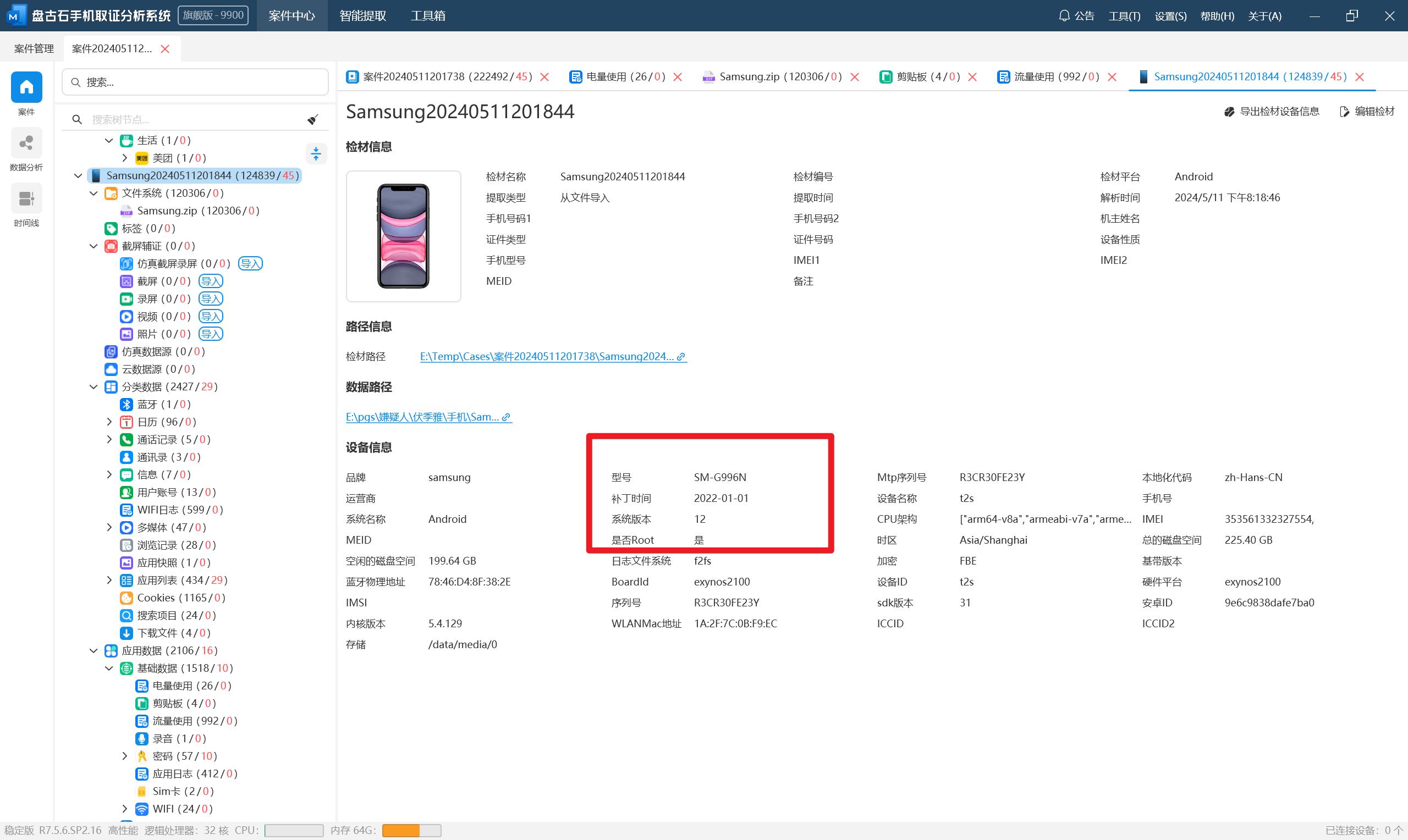
分析伏季雅的手机检材,其和受害人视频通话的时间是:[答案格式:2024-01-01-04-05][★☆☆☆☆]
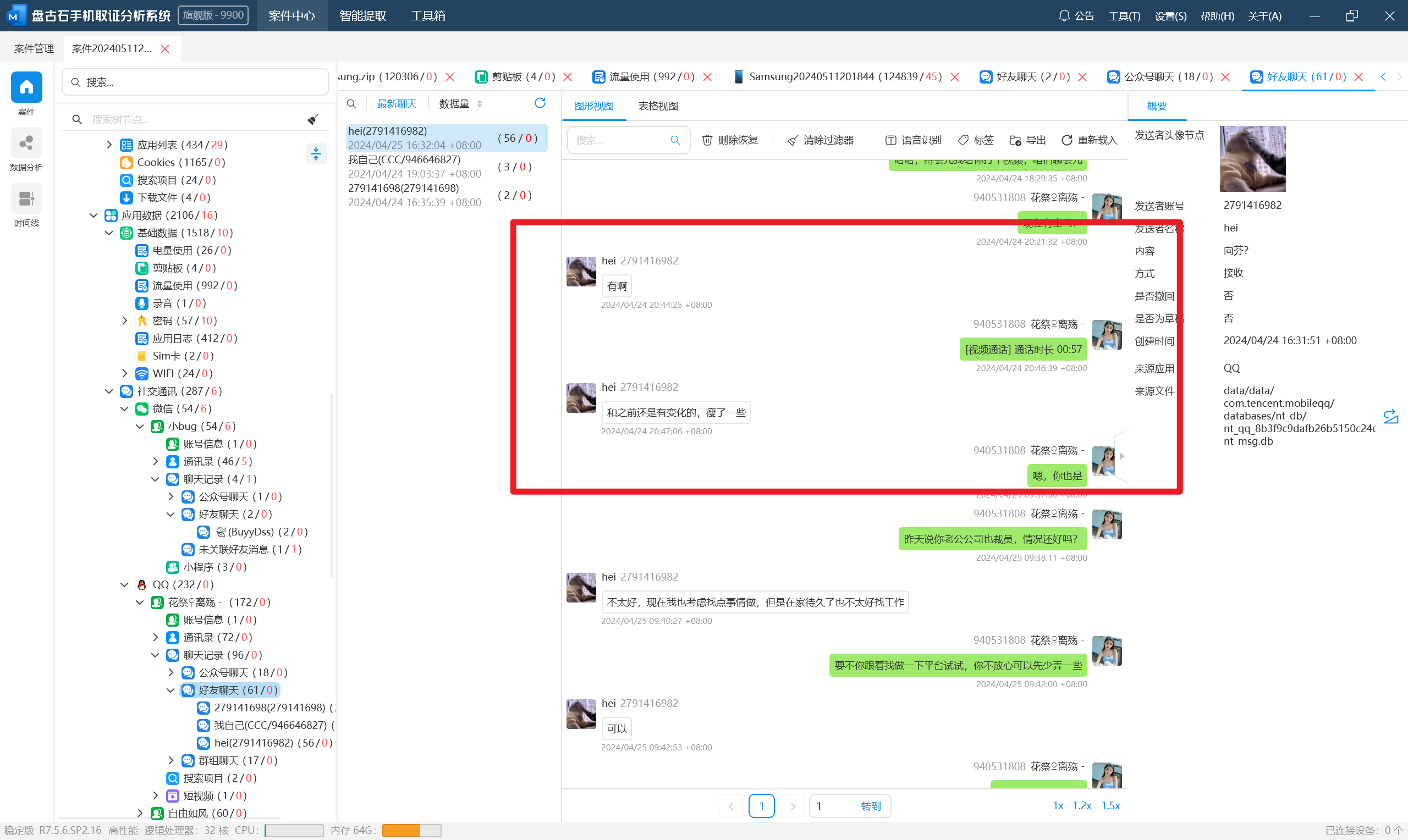
分析伏季雅的手机检材,手机中安装了一款记账APP,该记账APP存储记账信息的数据库名称是:[答案格式:abcabc,区分大小写][★☆☆☆☆]
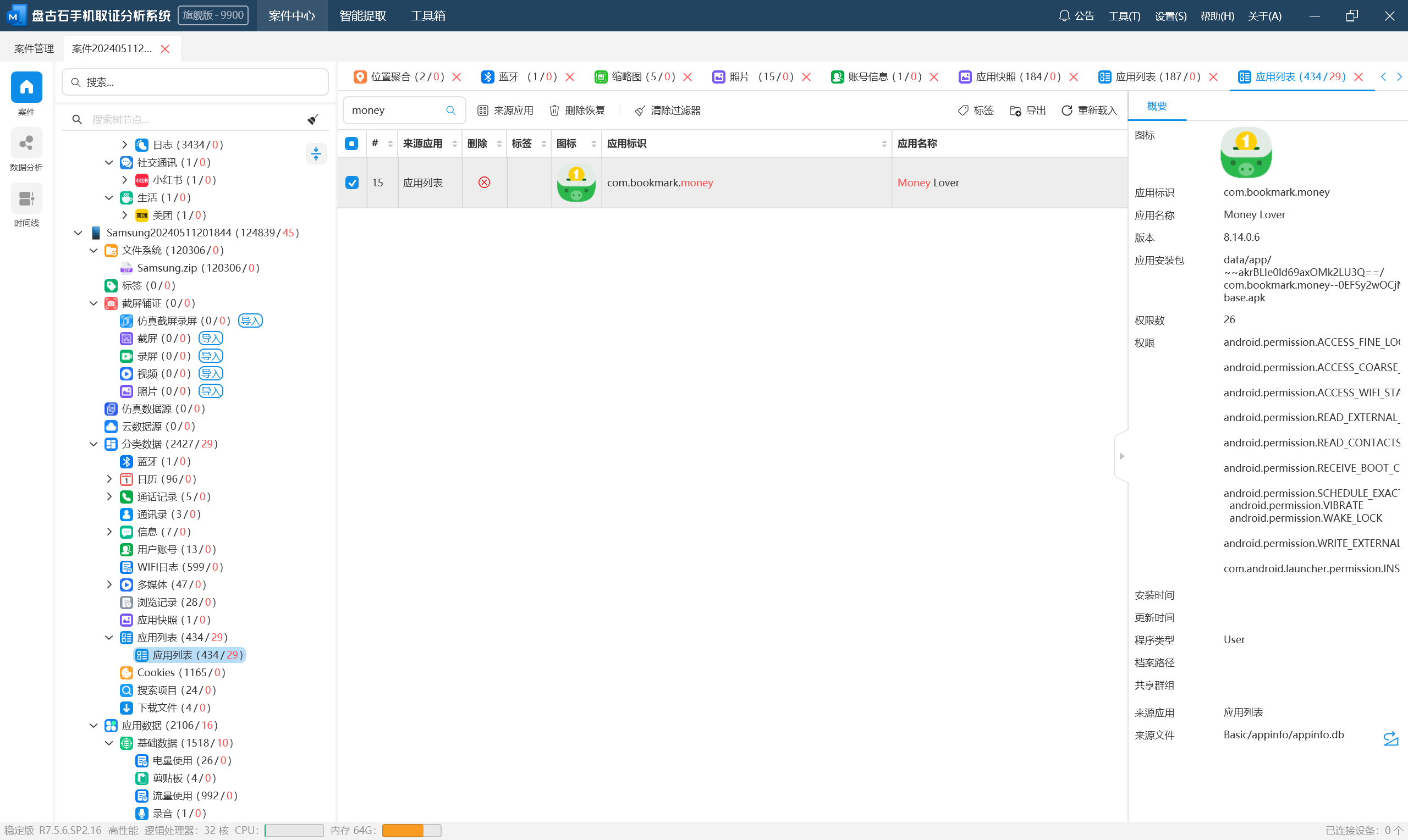
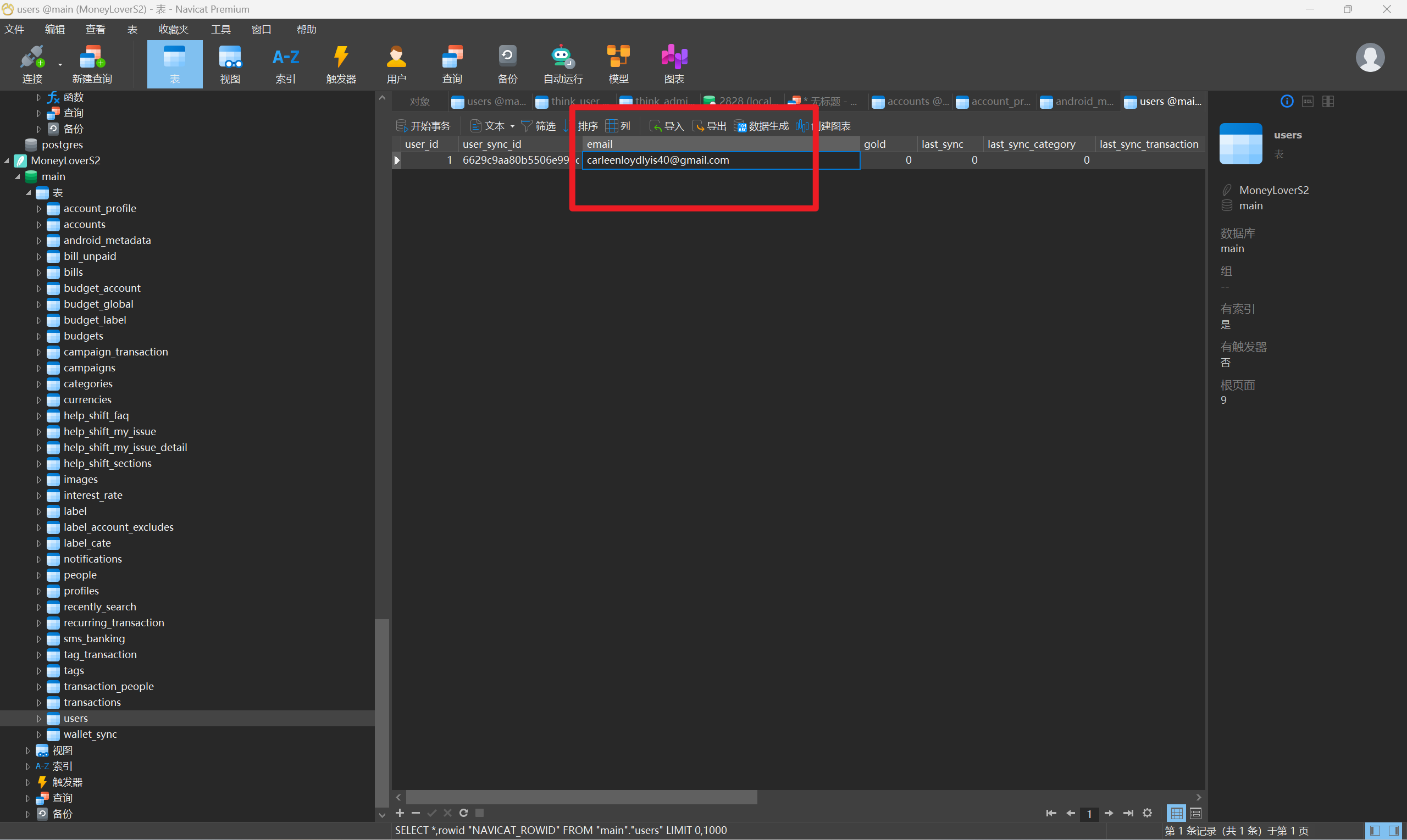
\嫌疑人\伏季雅\手机\Samsung\data\data\com.bookmark.money\databases\MoneyLoverS2
接上题,该记账APP登录的邮箱账号是:[答案格式:abc@abc.com][★★★☆☆]
接上题,该记账APP中记录的所有收入金额合计是:[答案格式:1234][★★★☆☆]
1 | SELECT |
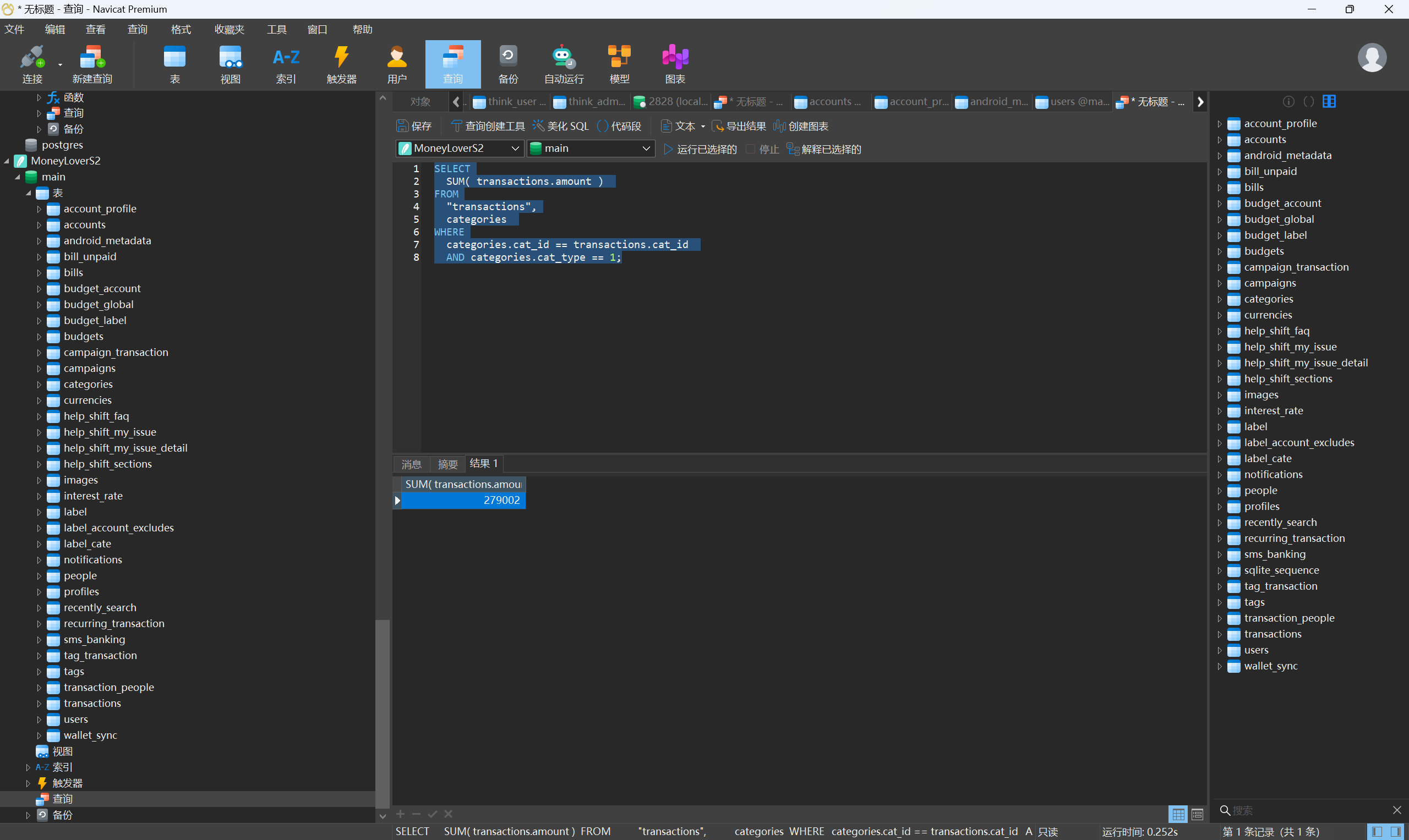
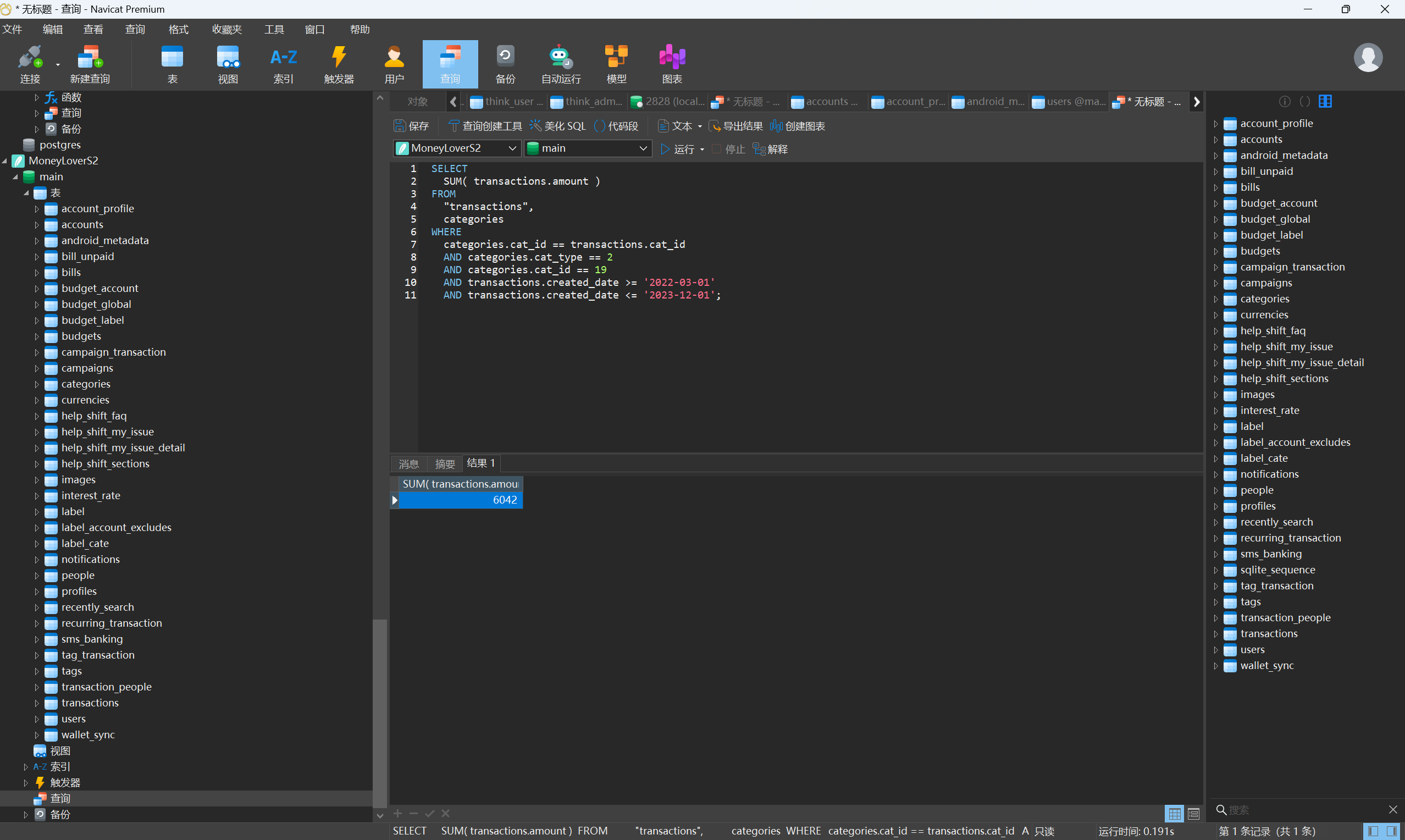
接上题,分析该记账APP中的消费记录,统计从2022-3-1(含)到2023-12-1(含)期间,用于交通的支出费用合计是:[答案格式:1234][★★★☆☆]
1 | SELECT |
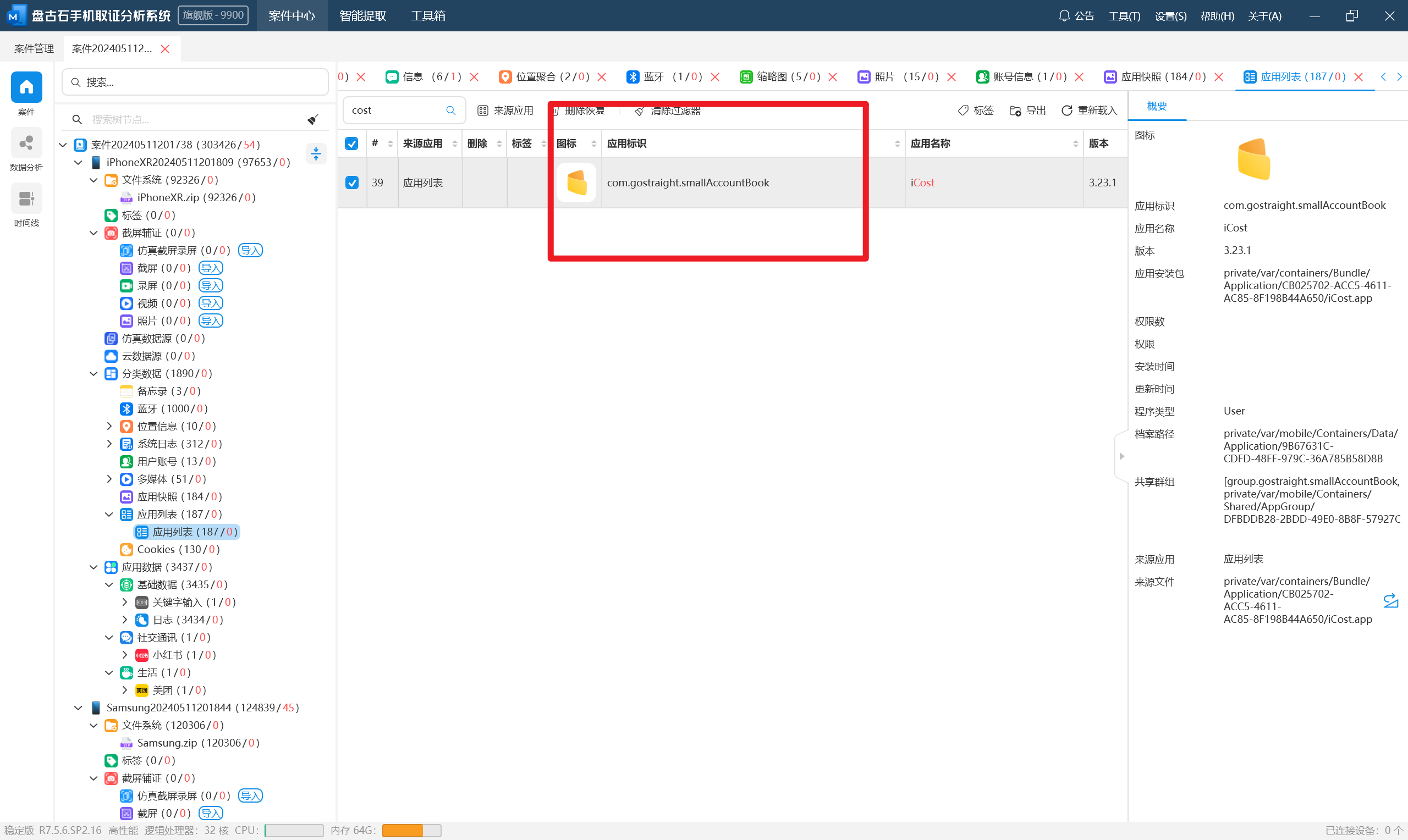
分析毛雪柳的手机检材,手机中有一个记账APP,该APP的应用名称是:[答案格式:Telegram,区分大小写][★☆☆☆☆]
分析义言的手机检材,手机中登录的谷歌邮箱账号是:[答案格式:abc@gmail.com][★★☆☆☆]
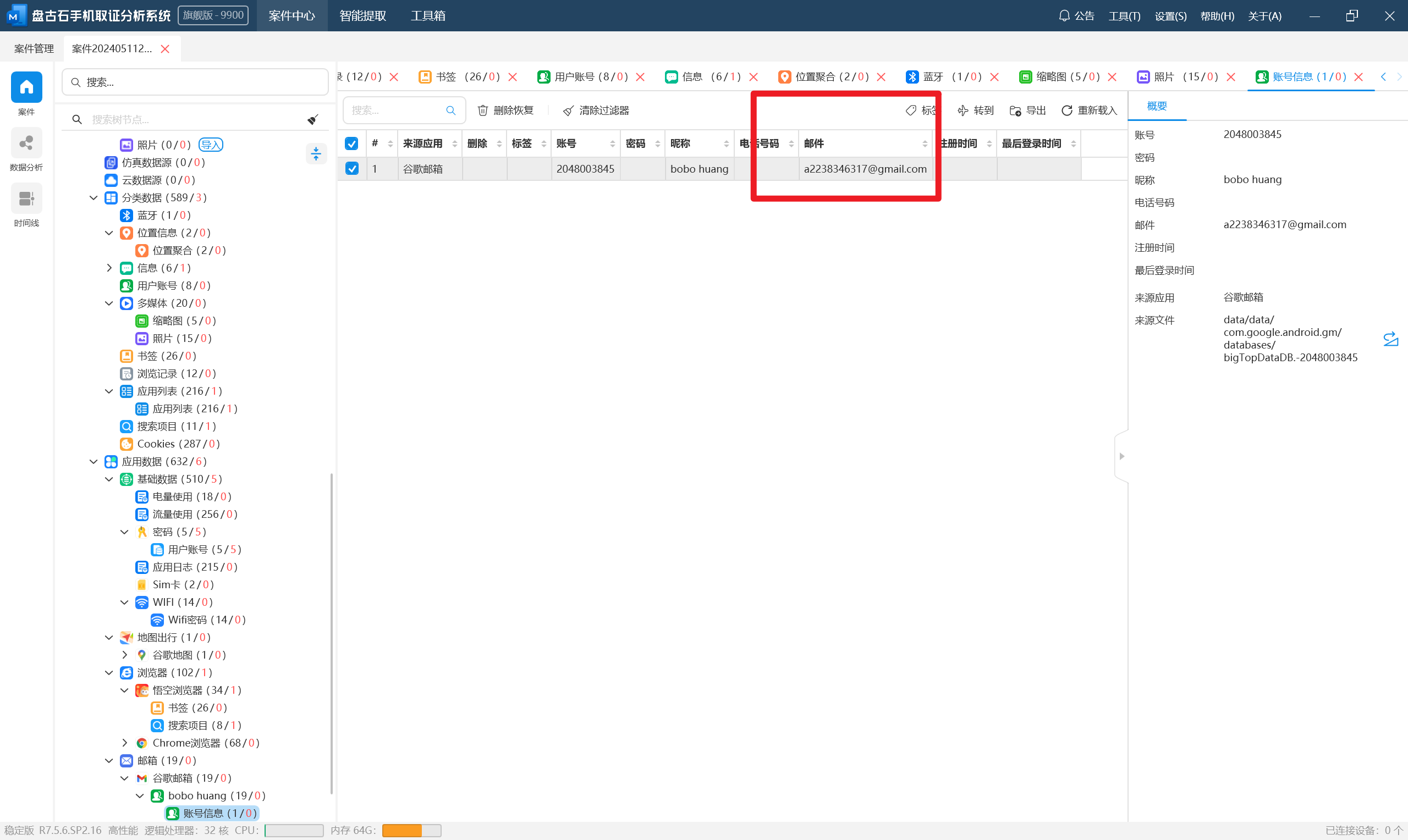
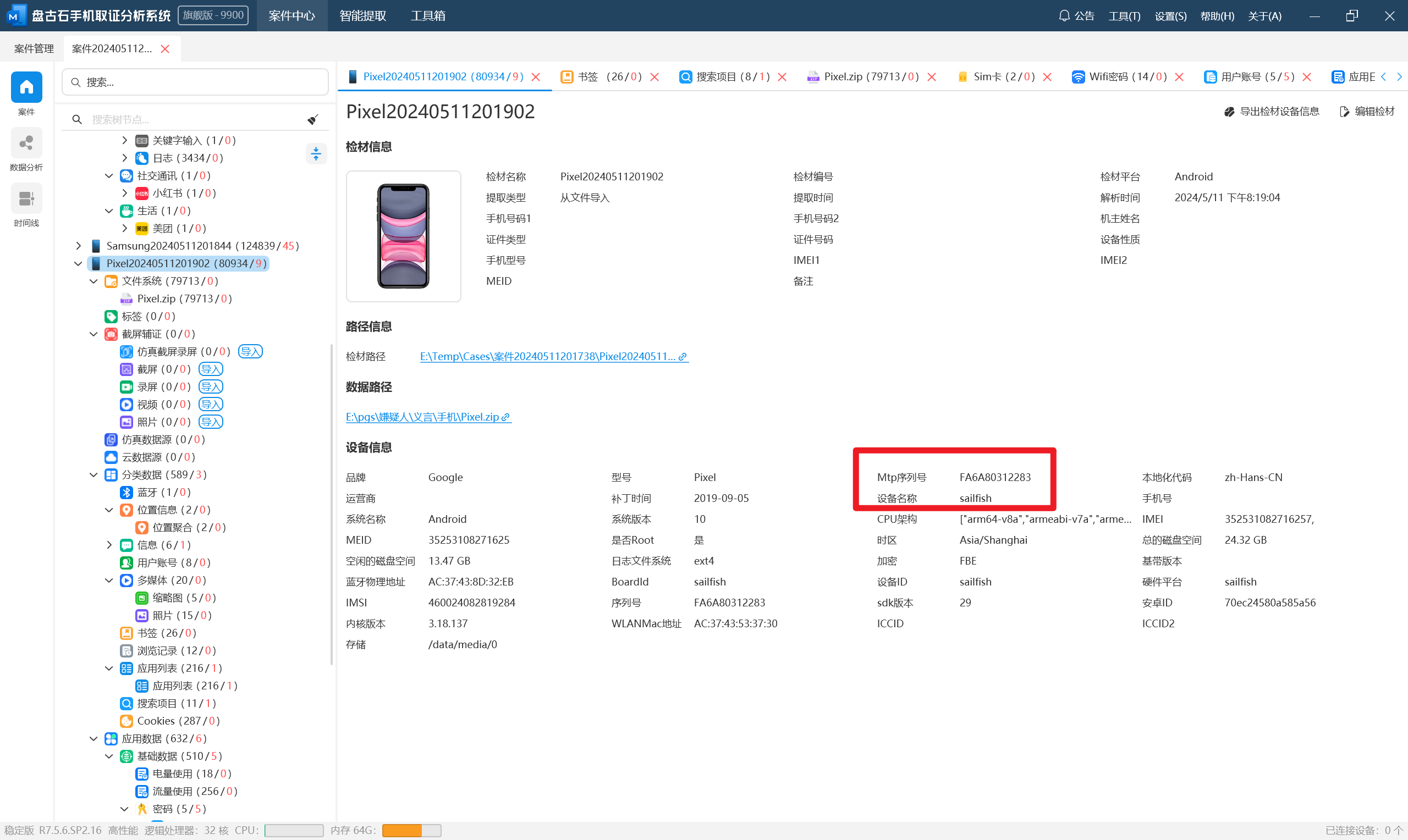
分析义言的手机检材,手机的MTP序列号是:[答案格式:大写字母和数字][★★☆☆☆]
分析义言的手机检材,除系统自带的浏览器外,手机中安装了一款第三方浏览器,该浏览器的应用名称是:[答案格式:百度浏览器][★★☆☆☆]
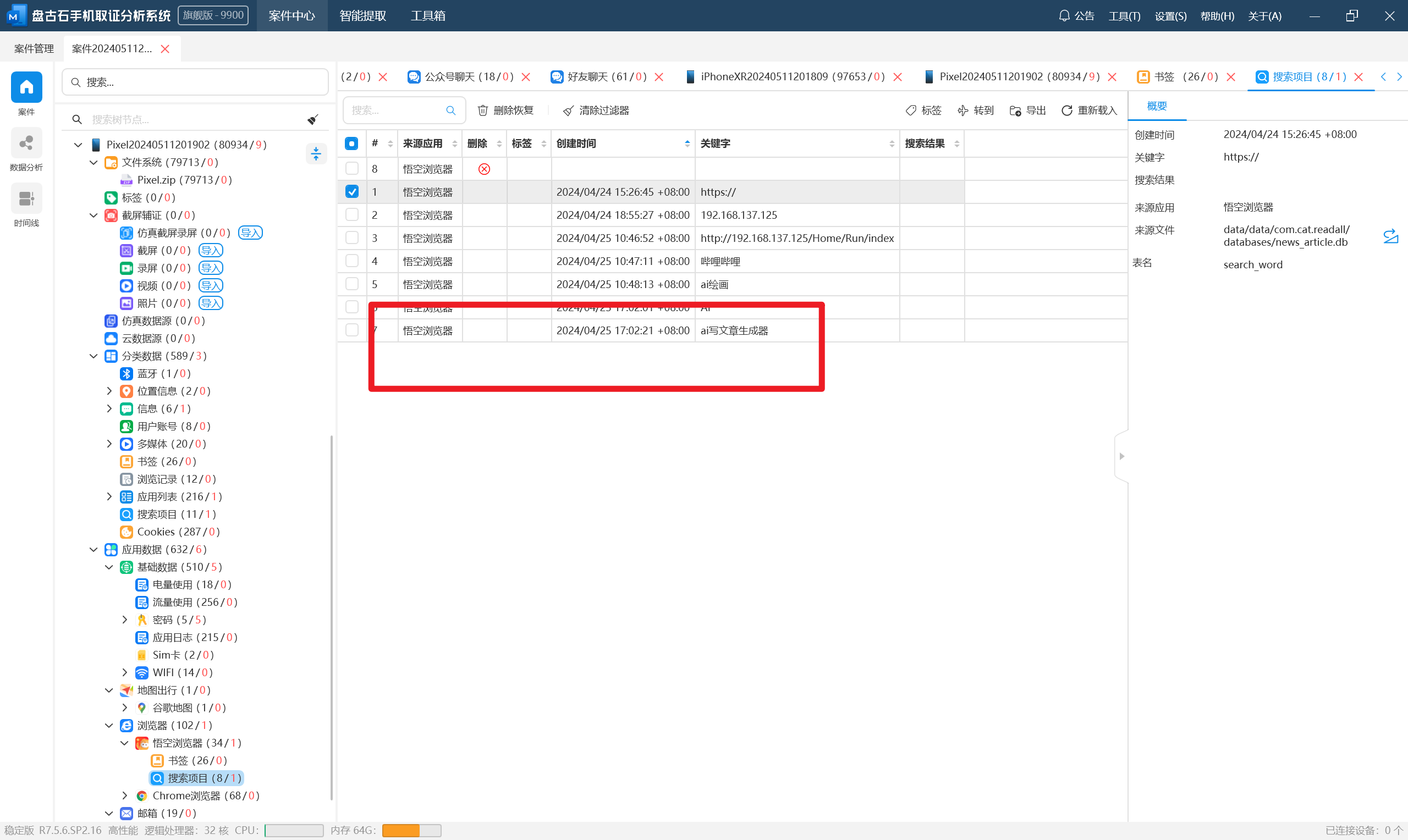
接上题,上述浏览器最后一次搜索的关键字是:[答案格式:百度][★★☆☆☆]
见上
接上题,该浏览器最后一次收藏的网址是:[答案格式:https://baidu.com/acc/123412341234123/][★★★☆☆]
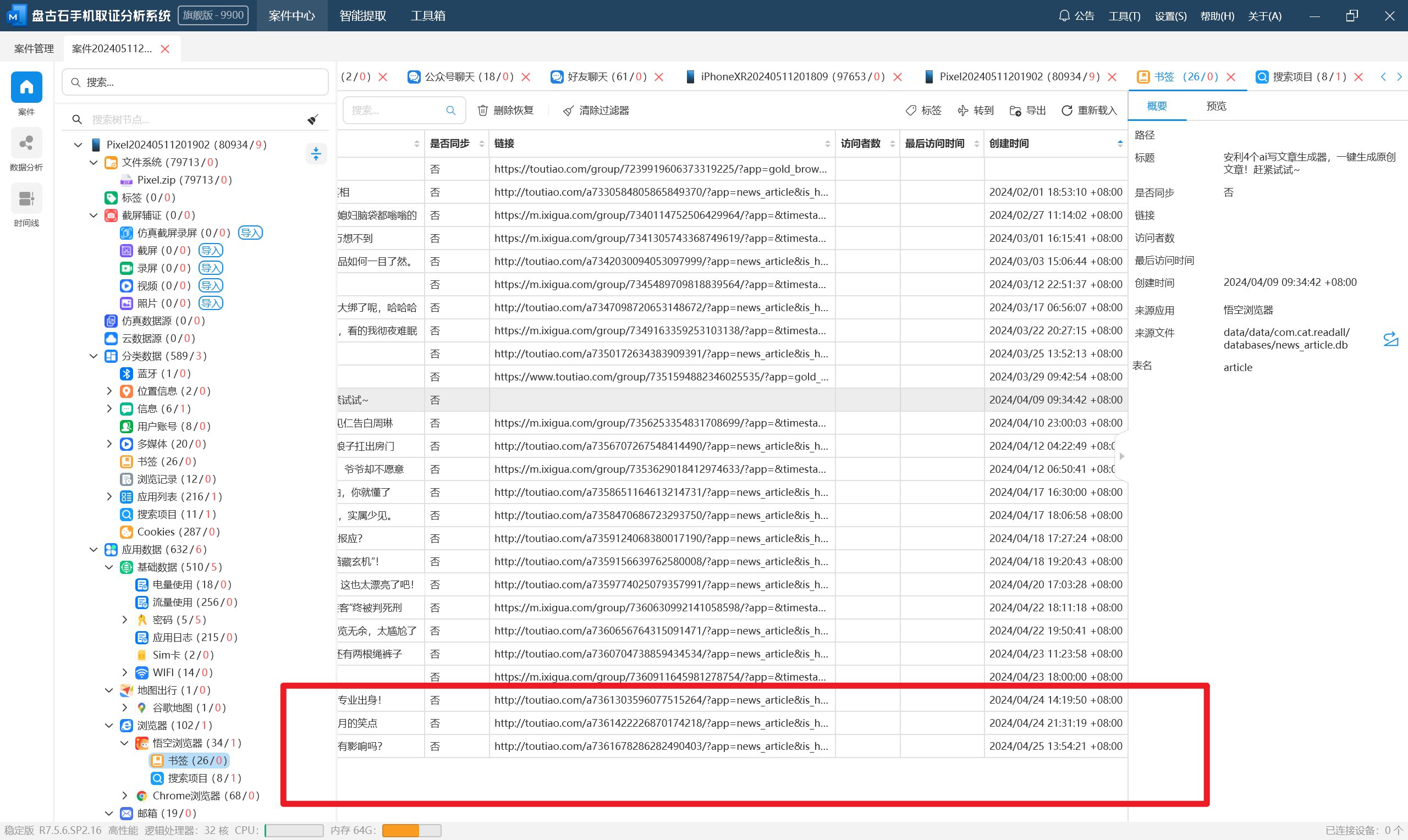
分析义言的手机检材,其所购买的公民信息数据,该数据提供者的手机号码是:[答案格式:13012341234][★☆☆☆☆]
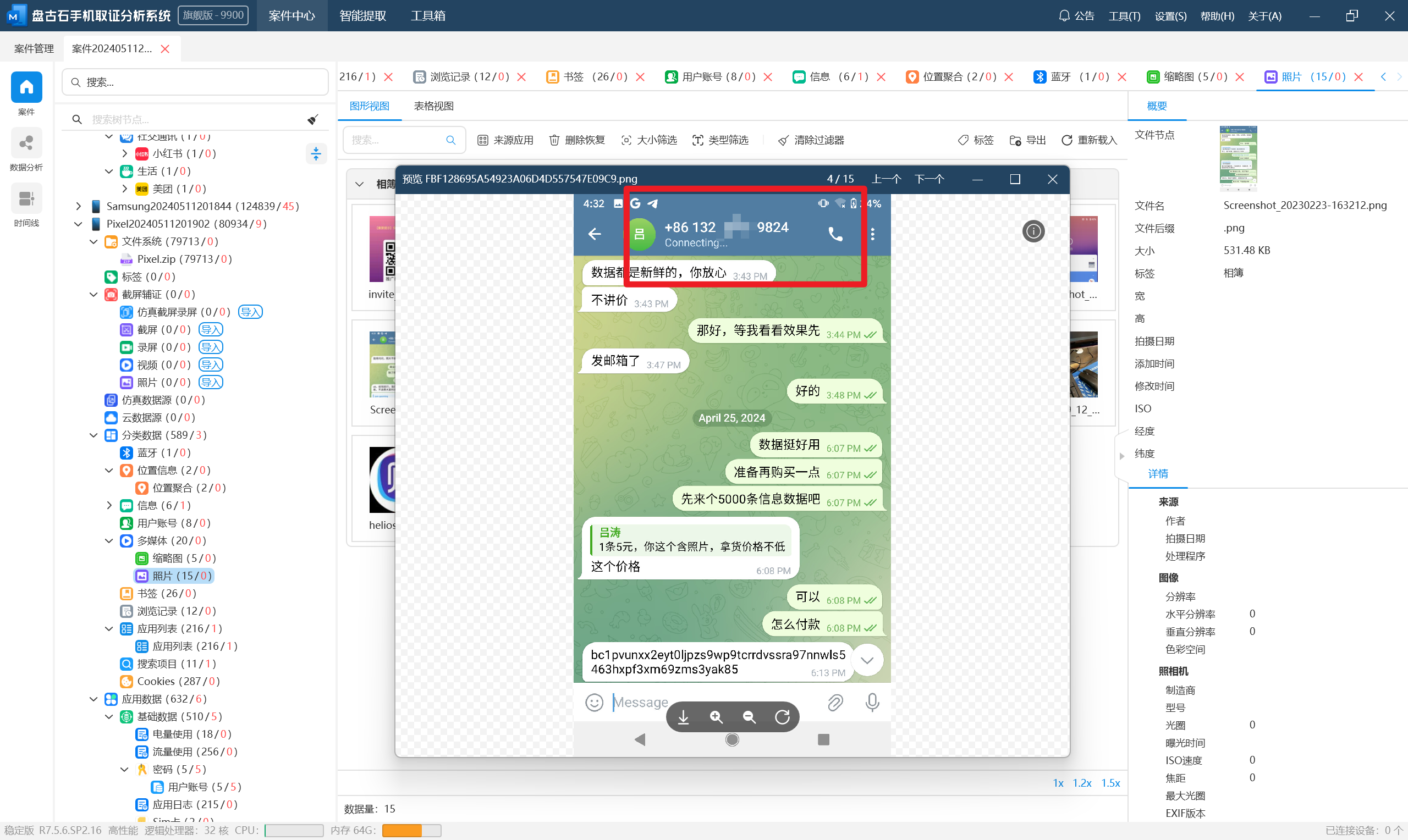
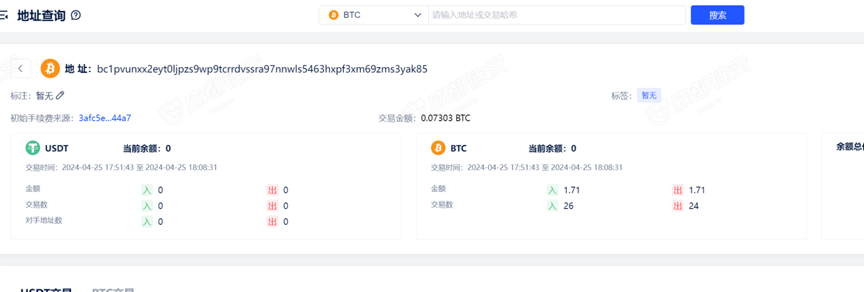
接上题,卖家的收款地址:[答案格式:小写字母和数字][★☆☆☆☆]
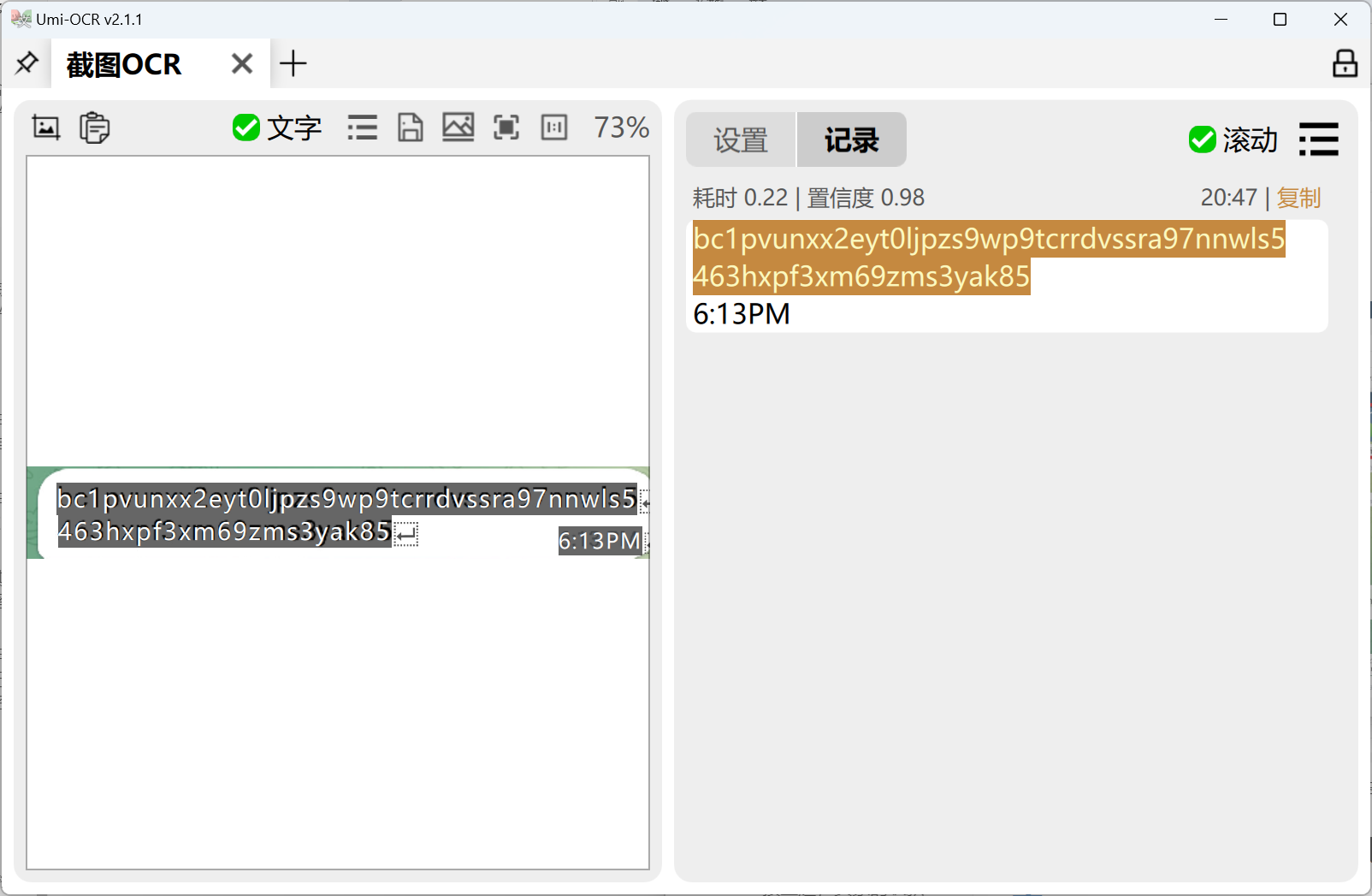
接上题,购买上述公民信息,义言一共支付了多少钱:[答案格式:0.000123BTC][★☆☆☆☆]
交易hash:4630a72ad8e7339e553cdba67a1dc7d33716a1db0cf7b44ec281ae08ac6249f8
发送地址:bc1puq3evrtuaky9sk08sf5dnmjfx4yuwc5c63ylzy05jcc9nqx267aqcv7fjf
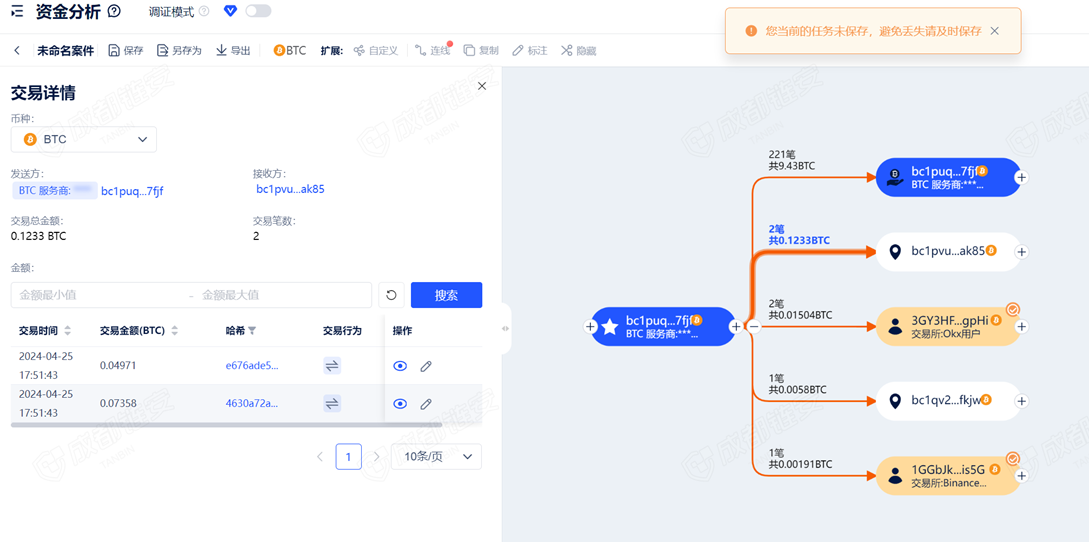
因为答案格式为精度到小数点后6位,所以把交易记录导出然后精确计算

接上题,该笔交易产生的手续费是多少:[答案格式:0.000123BTC][★★☆☆☆]
手续费链必追没法直接查高精度,直接拿交易哈希去官网浏览器查
0.000061
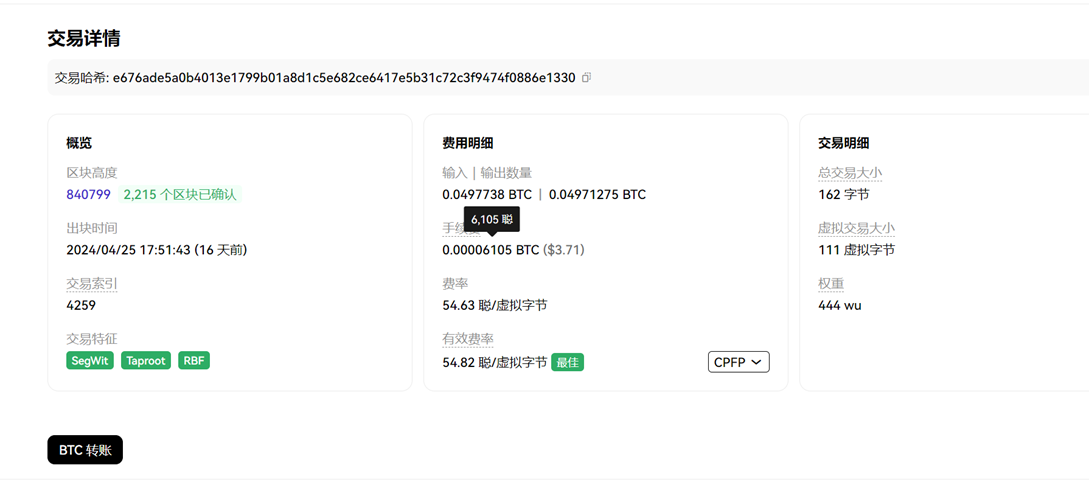
0.000061
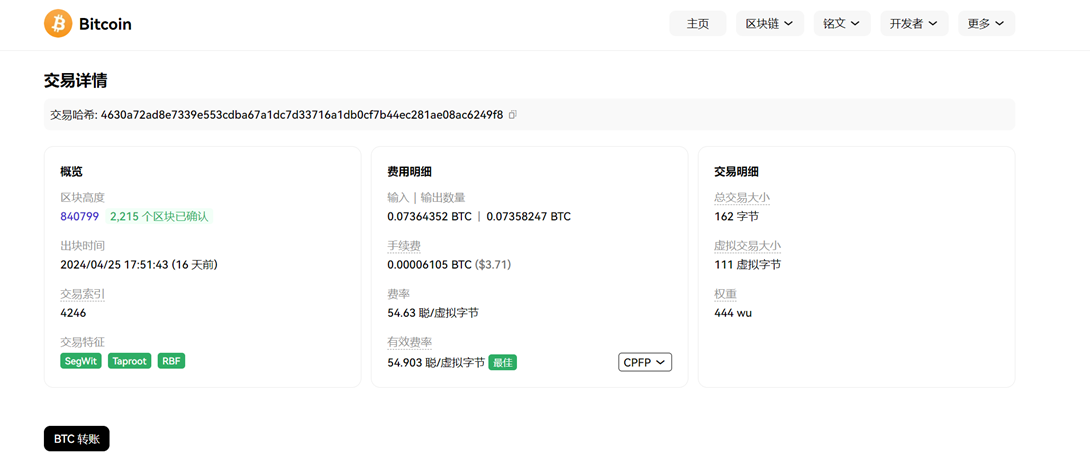
总共0.000122BTC
总结
有两位蓝桥杯人才在,我躺的很舒服
如有纰漏,欢迎微信交流:WQZ1127786222
Galaxy#b3nguang
2024.5.12
